Azure Storage Account is a public service, so the date can be access via public endpoints or through supported applications. In this project, I will be demonstrating the various ways Azure storage account can be accessed and the ways to secure them.
Prerequisites
- An Azure tenant
- Azure Storage Explorer application in a windows machine
Ways to access Azure Storage Accounts:
- Azure portal with the right roles assigned
- Can access via external application such as Azure Storage Explorer using Access Keys, Shared Access Signatures(SAS) token, public endpoints, Microsoft Entra id
Create a Storage Account in Azure
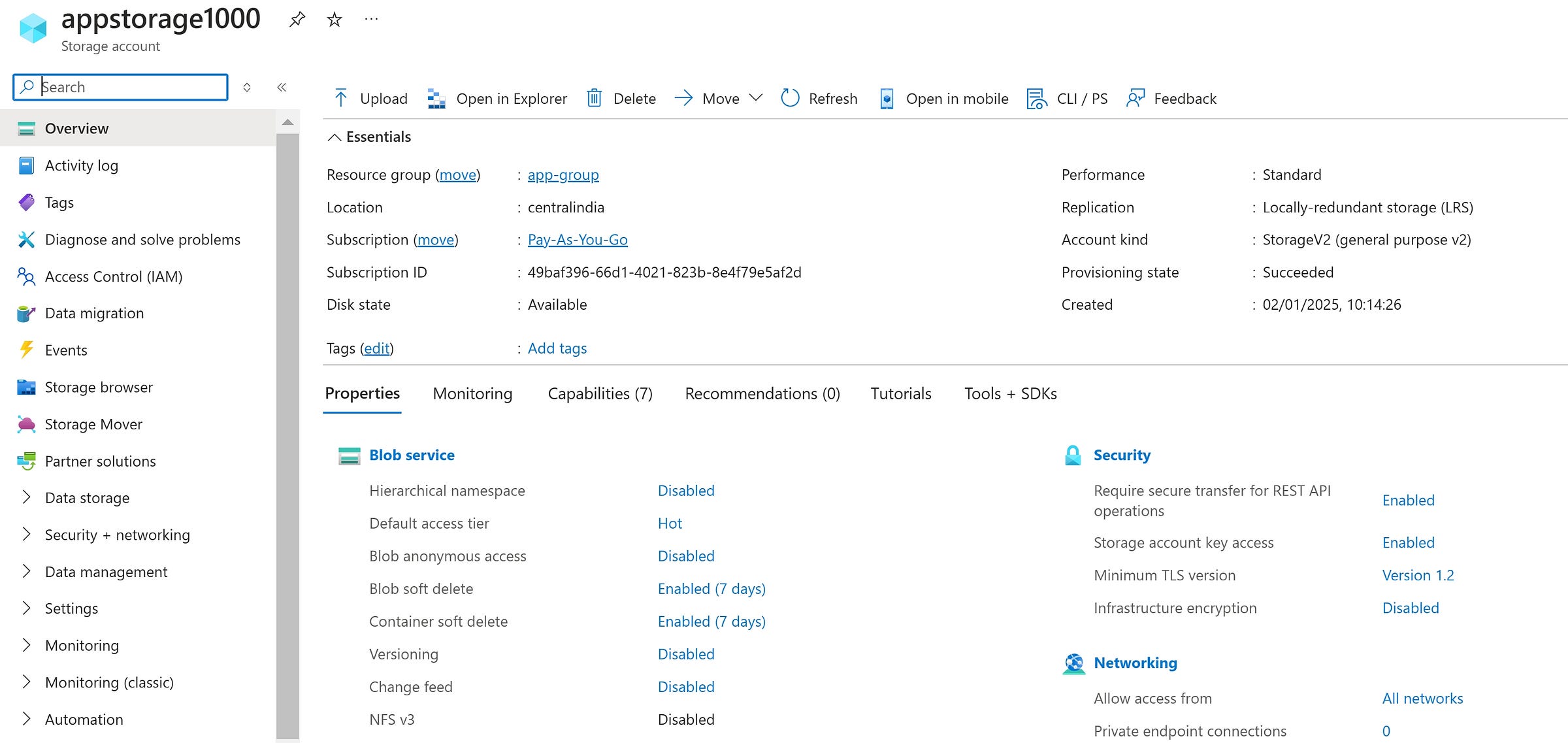
Create a storage account from Azure marketplace with simple configuration. Provide the resource group, unique Storage Account name and default settings are used for this demonstration.
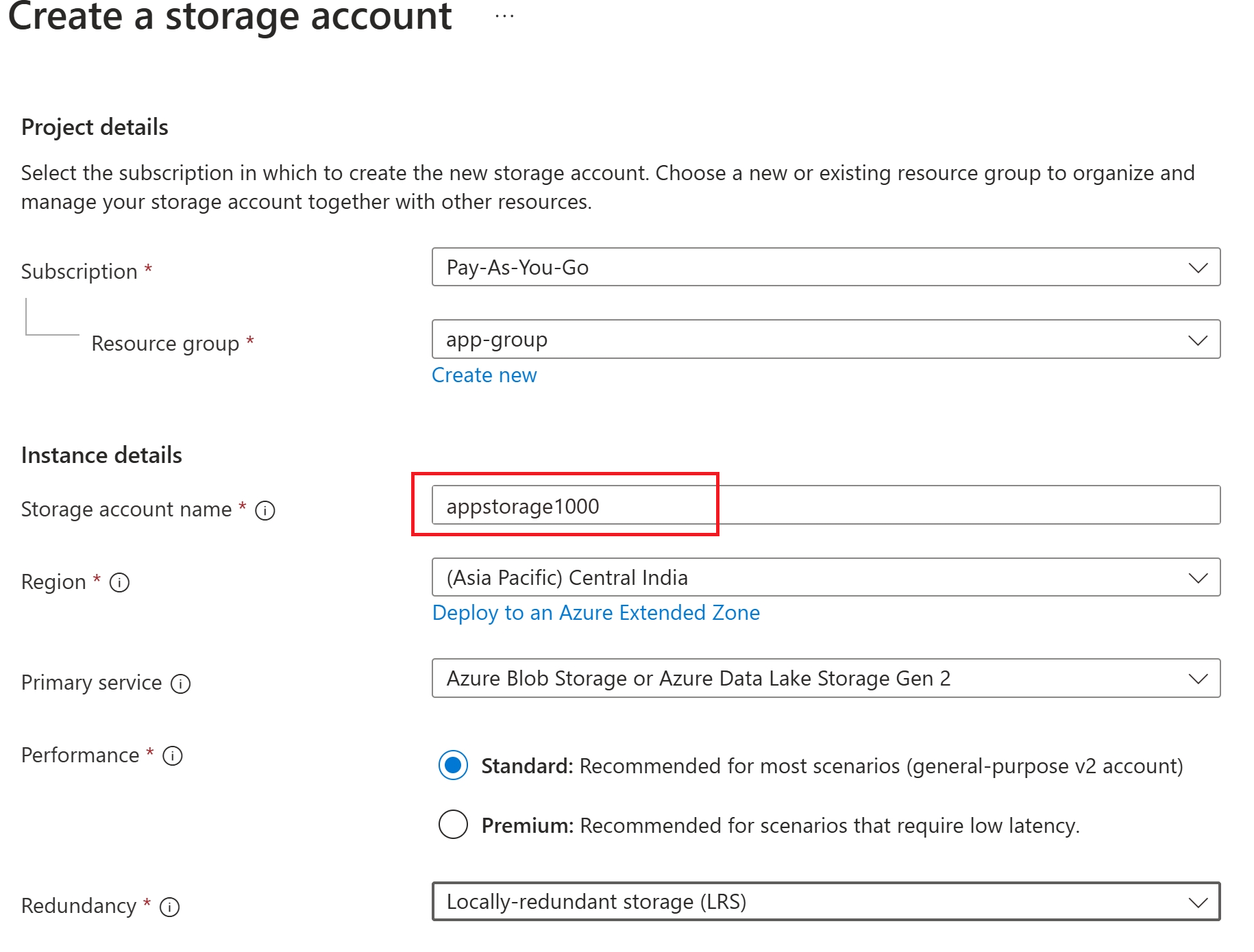
Storage Account is created as below
Azure Storage Account supports the following types
- Blob
- File Storage
- Queue for messaging
- Tables
In this blog, we will be using the blob containers as everything is similar when it comes to securing the storage account except the Microsoft Entra Roles. Roles specific to each types are added at the bottom of this blog.
Create a Container in Storage Account and upload files
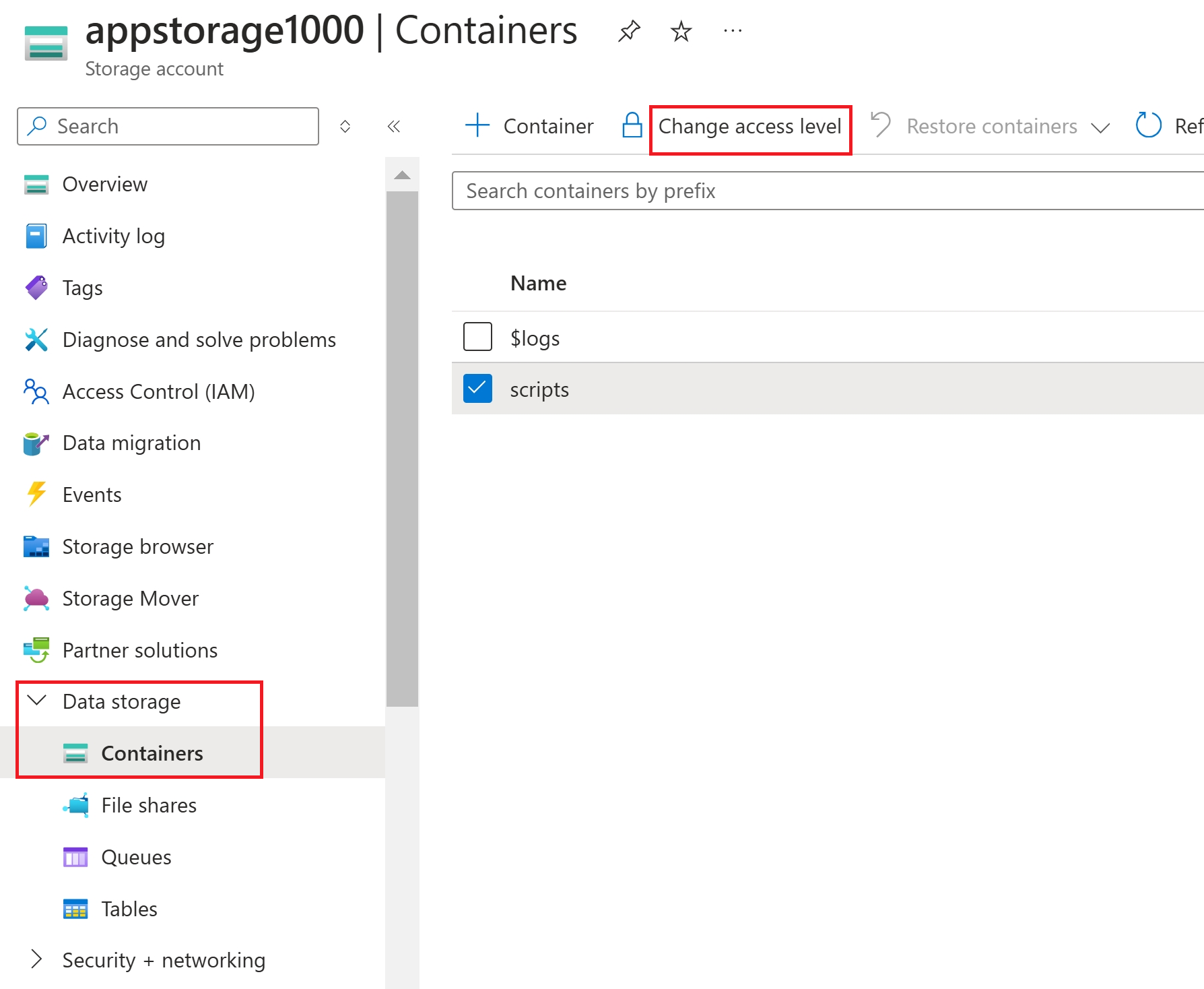
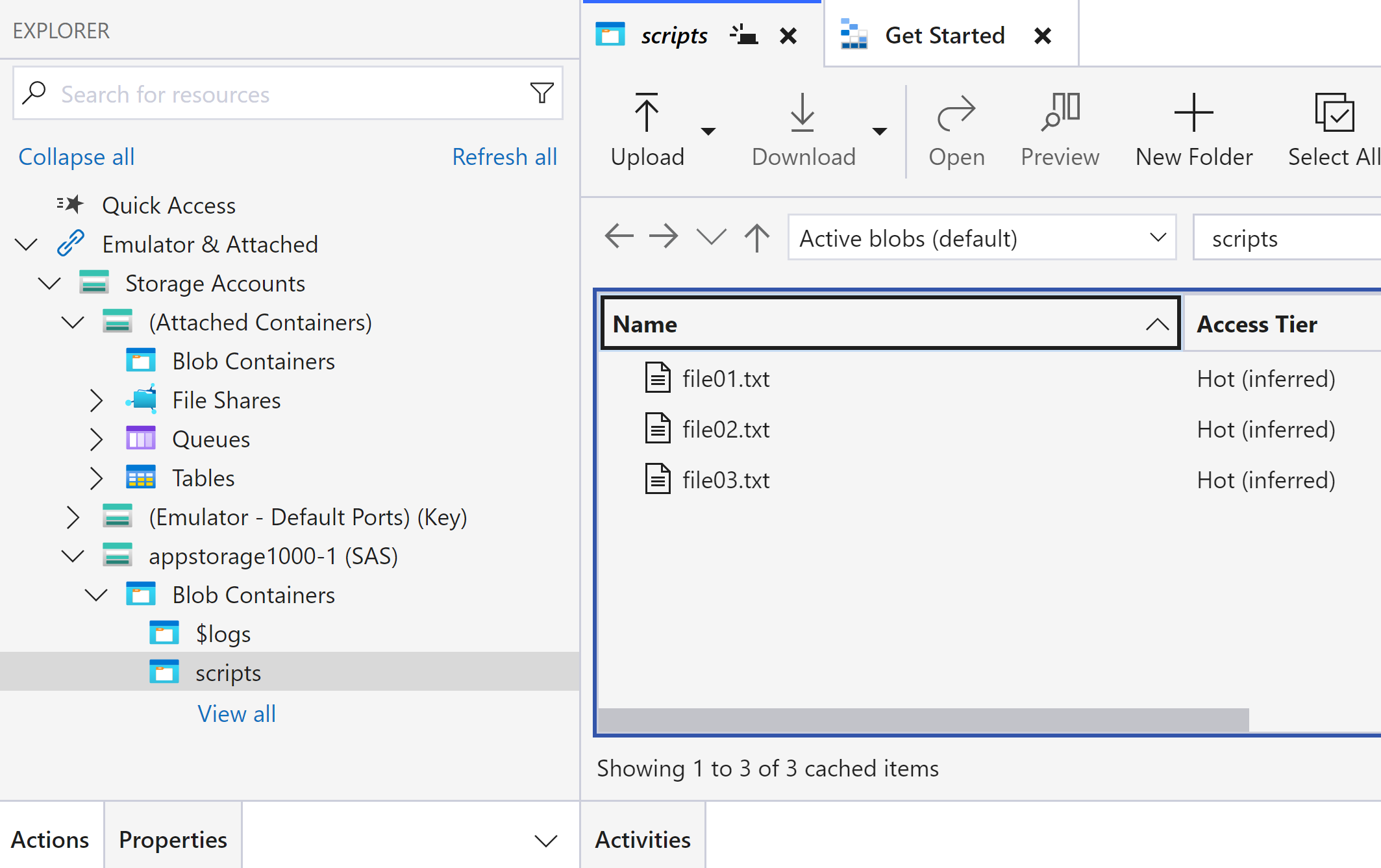
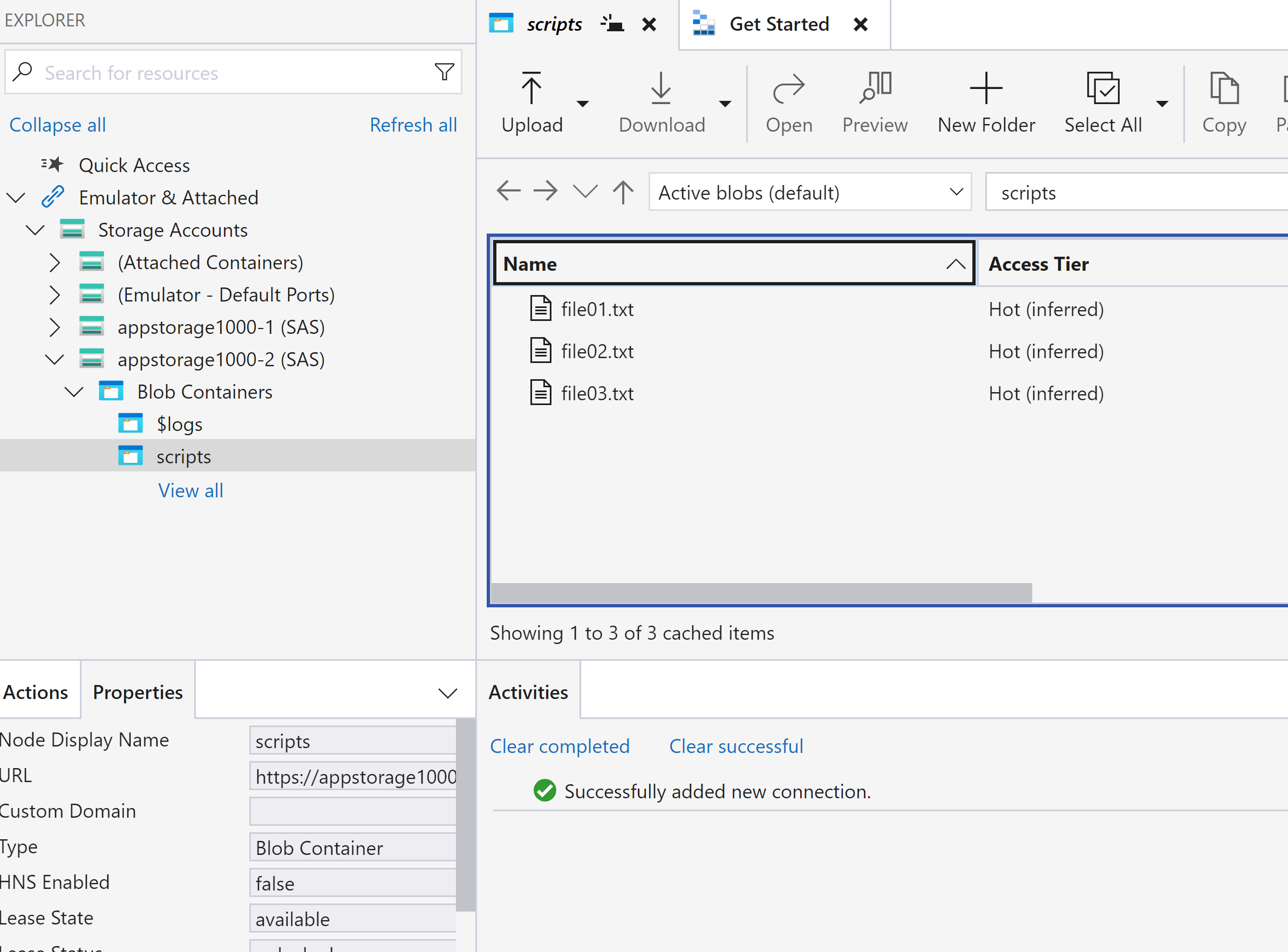
Azure Storage Account → Data Storage → Containers and created a container named ‘scripts’
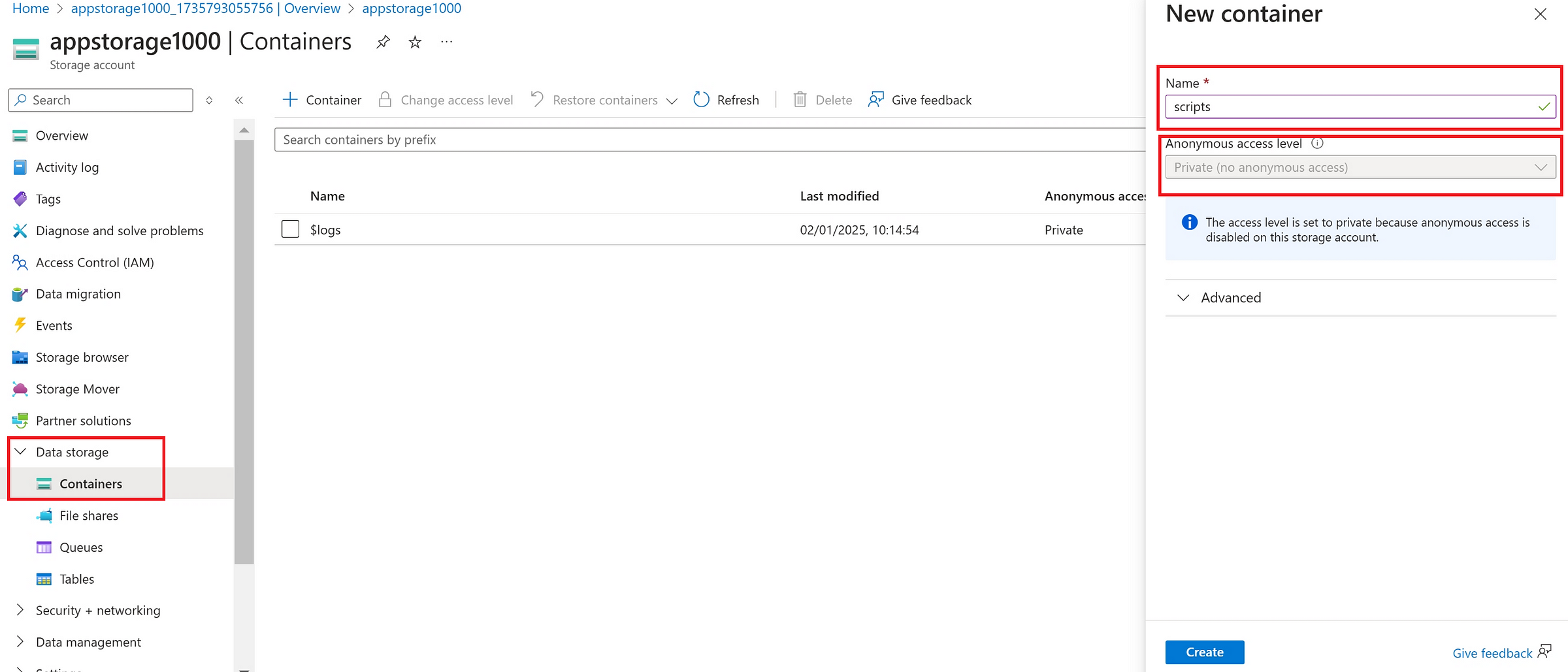
in ‘script’ container, uploaded 3 files as below

Each file will have individual property and a public endpoint to access via pubic channel.
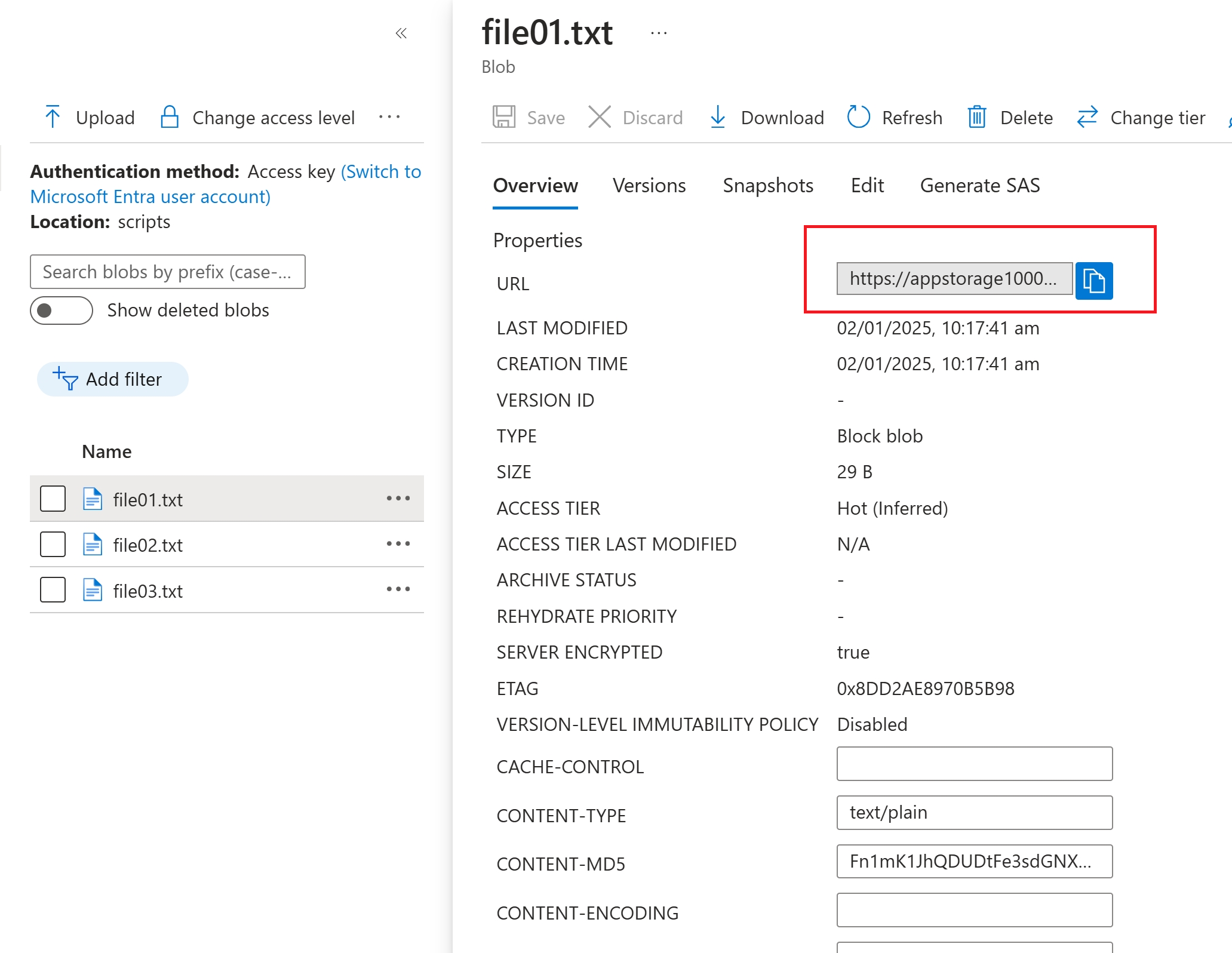
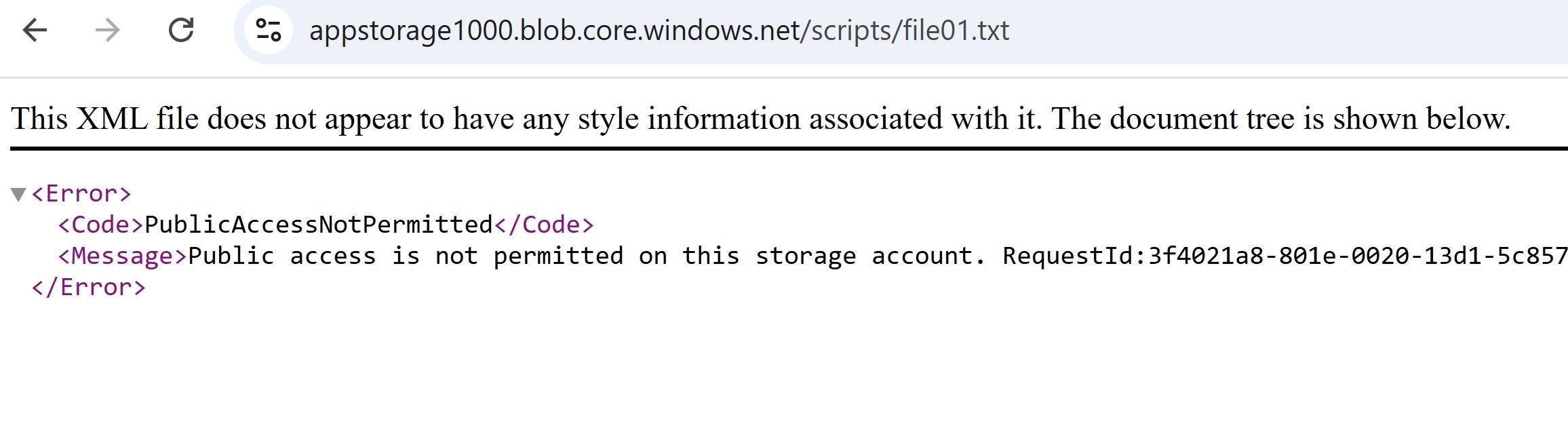
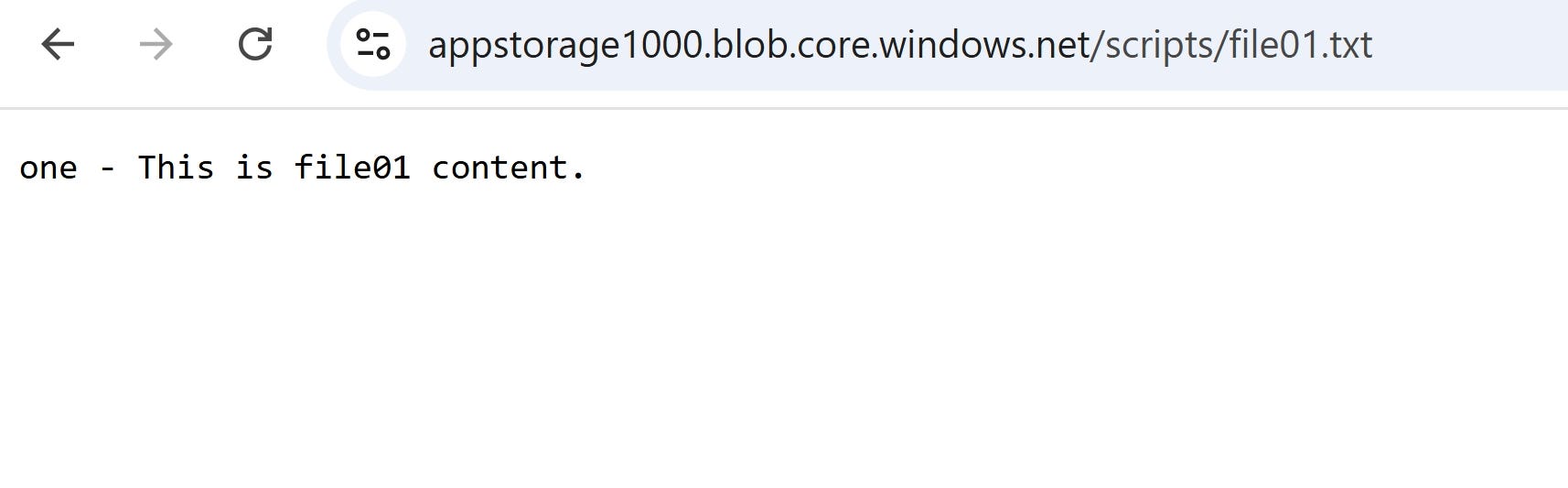
The endpoint doesn’t open the content of the file, since public anonymous access is disabled by default.
Azure Storage Account → Settings → Configuration
Enabled : Allow BLOB anonymous access
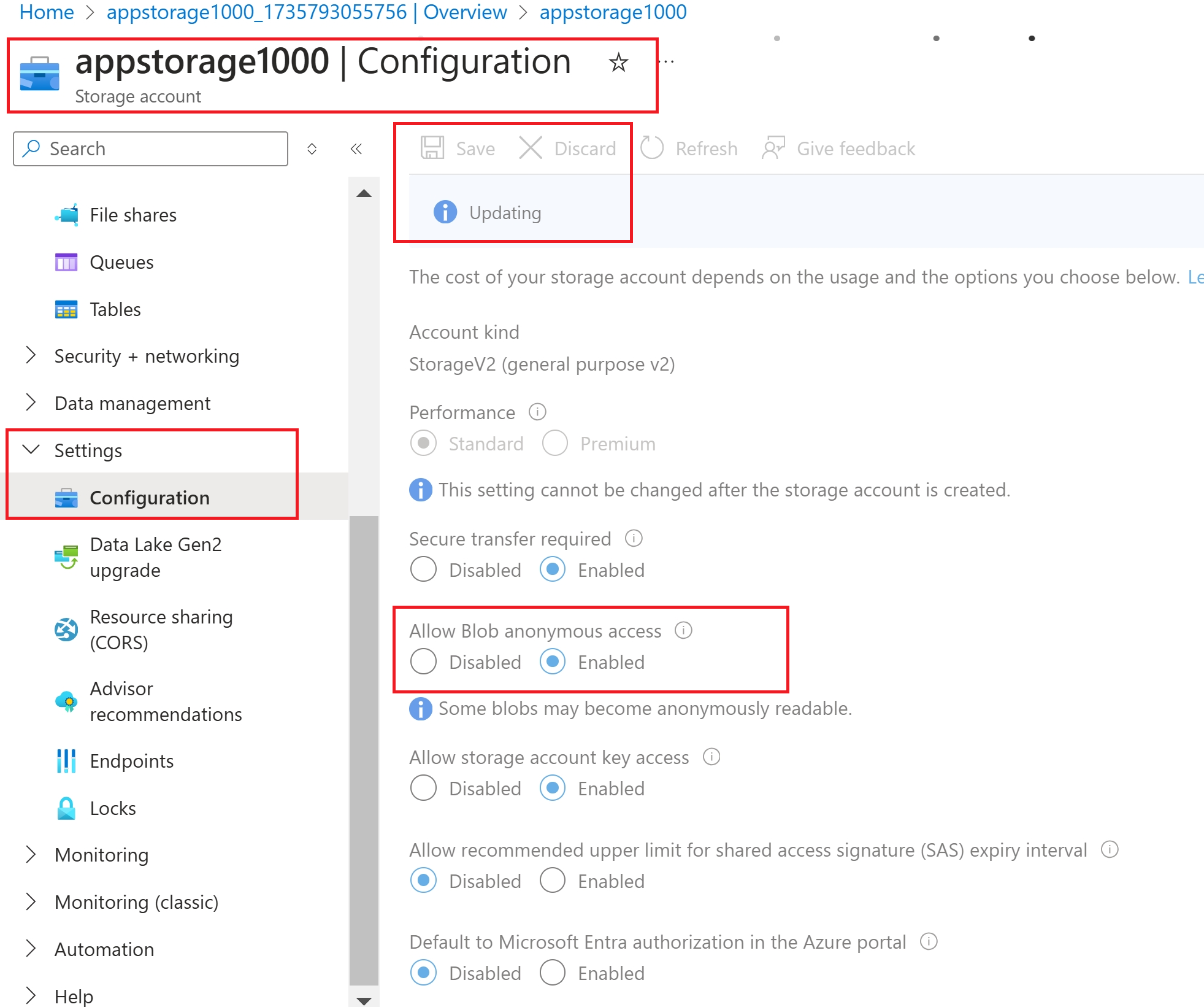
Now, “change access level” to enable anonymous access at the container level
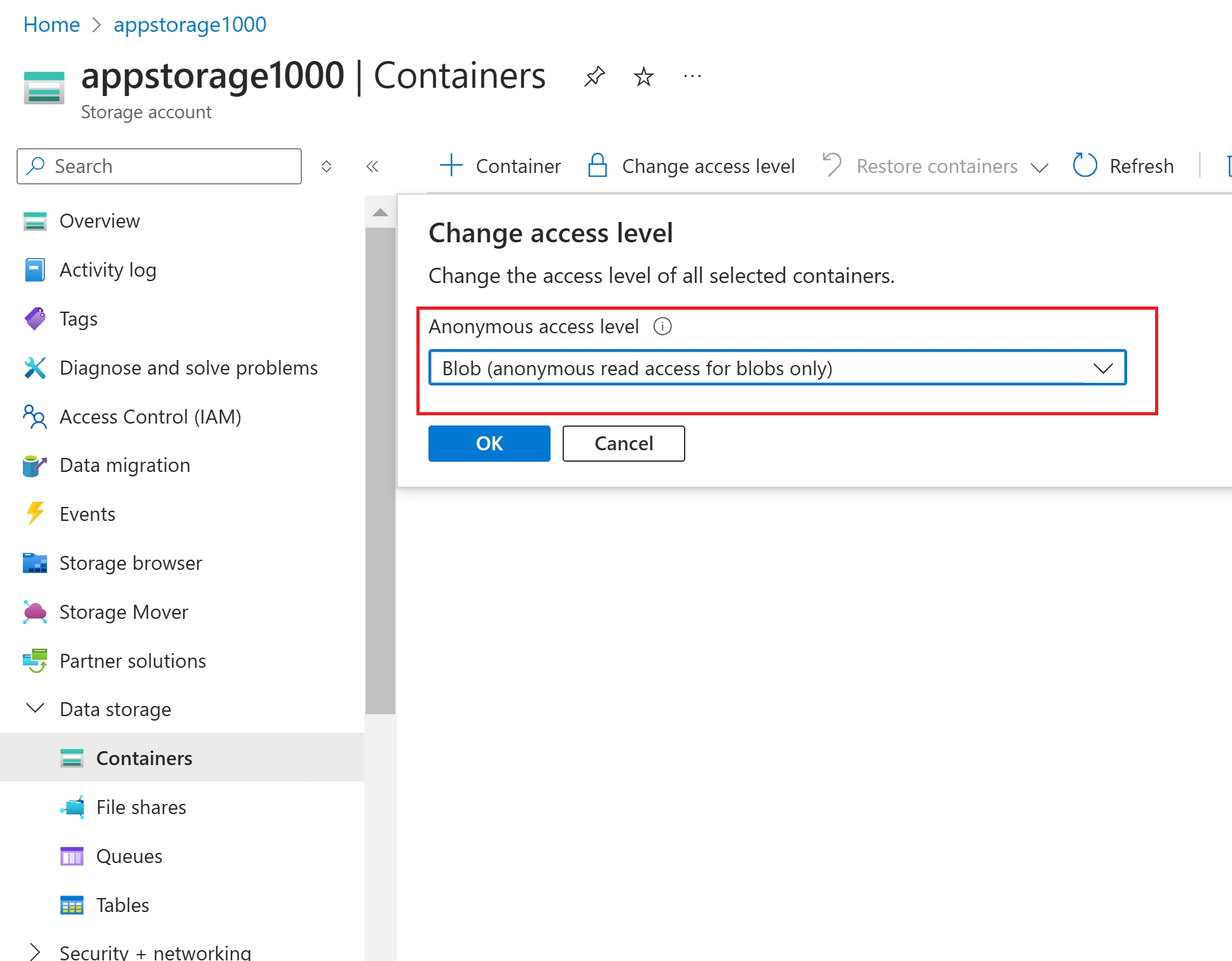
Now the file content is visible in the browser using the public endpoint as below.
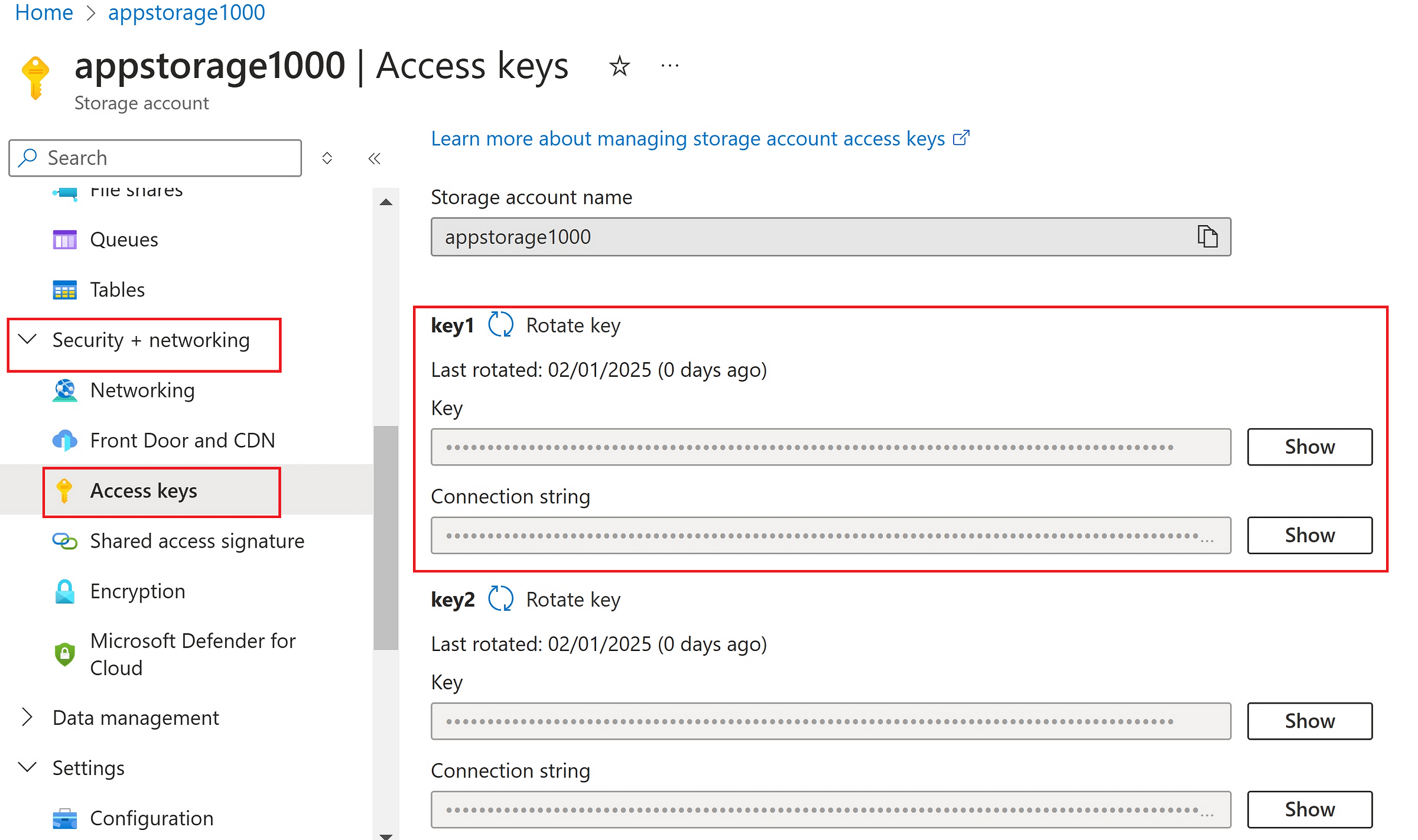
Access Storage Account using ‘Account Keys’
Access keys have all the permissions on the Storage account. So, using access keys is not advised. This is for the demonstration purpose only.
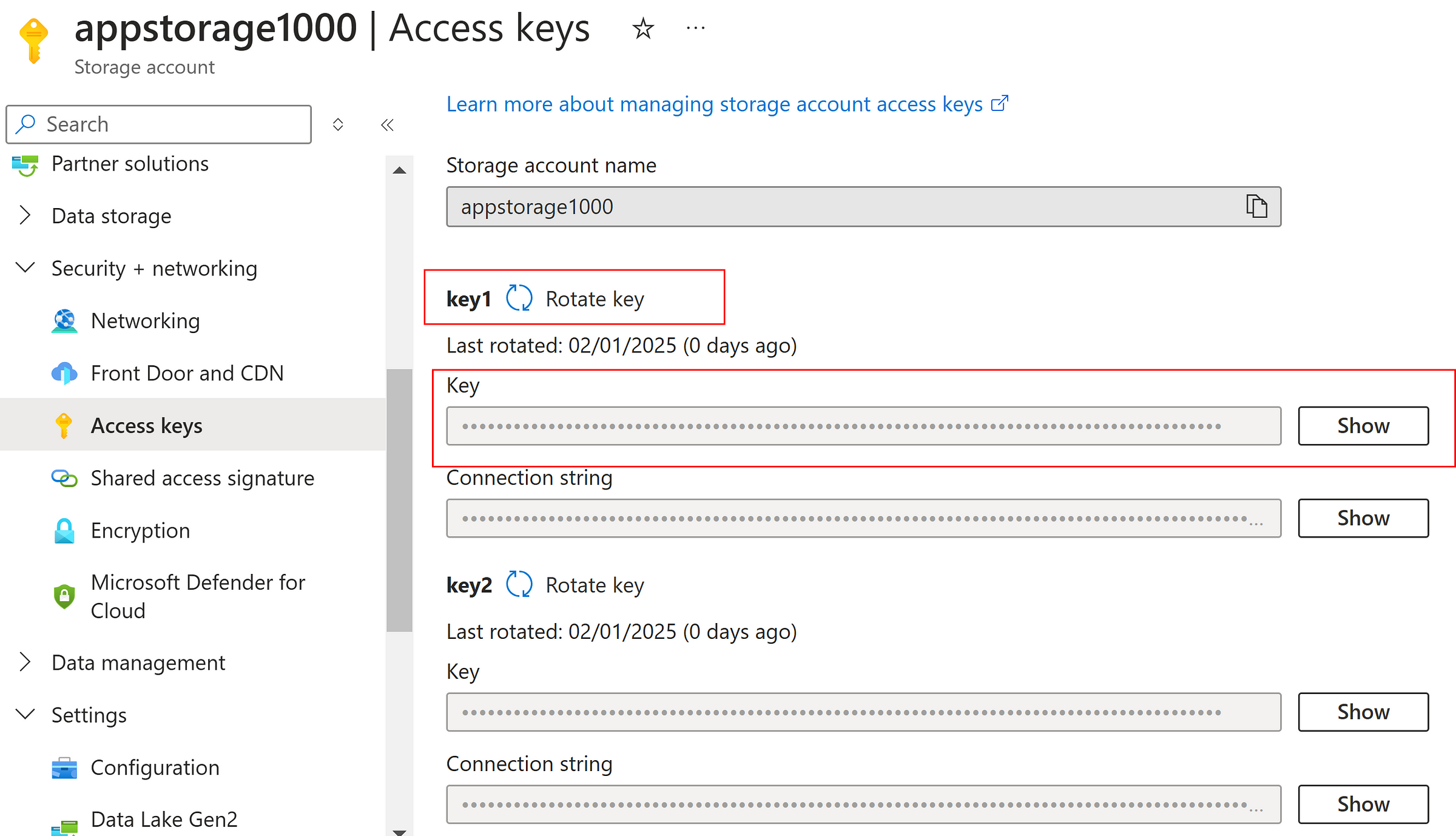
Storage Account → Security + Networking → Access Keys
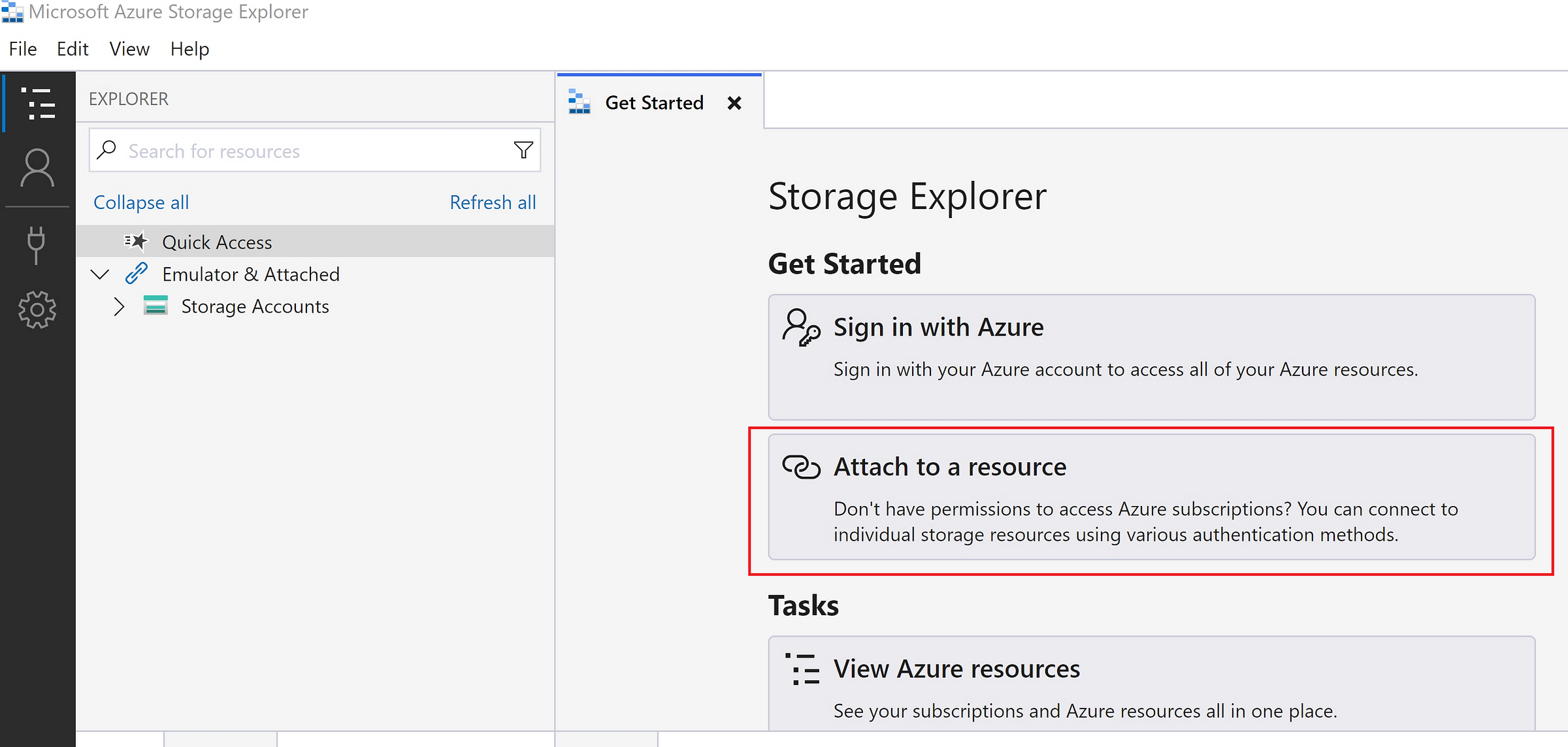
Launched Azure Storage Account and selected ‘Attach to a resource’
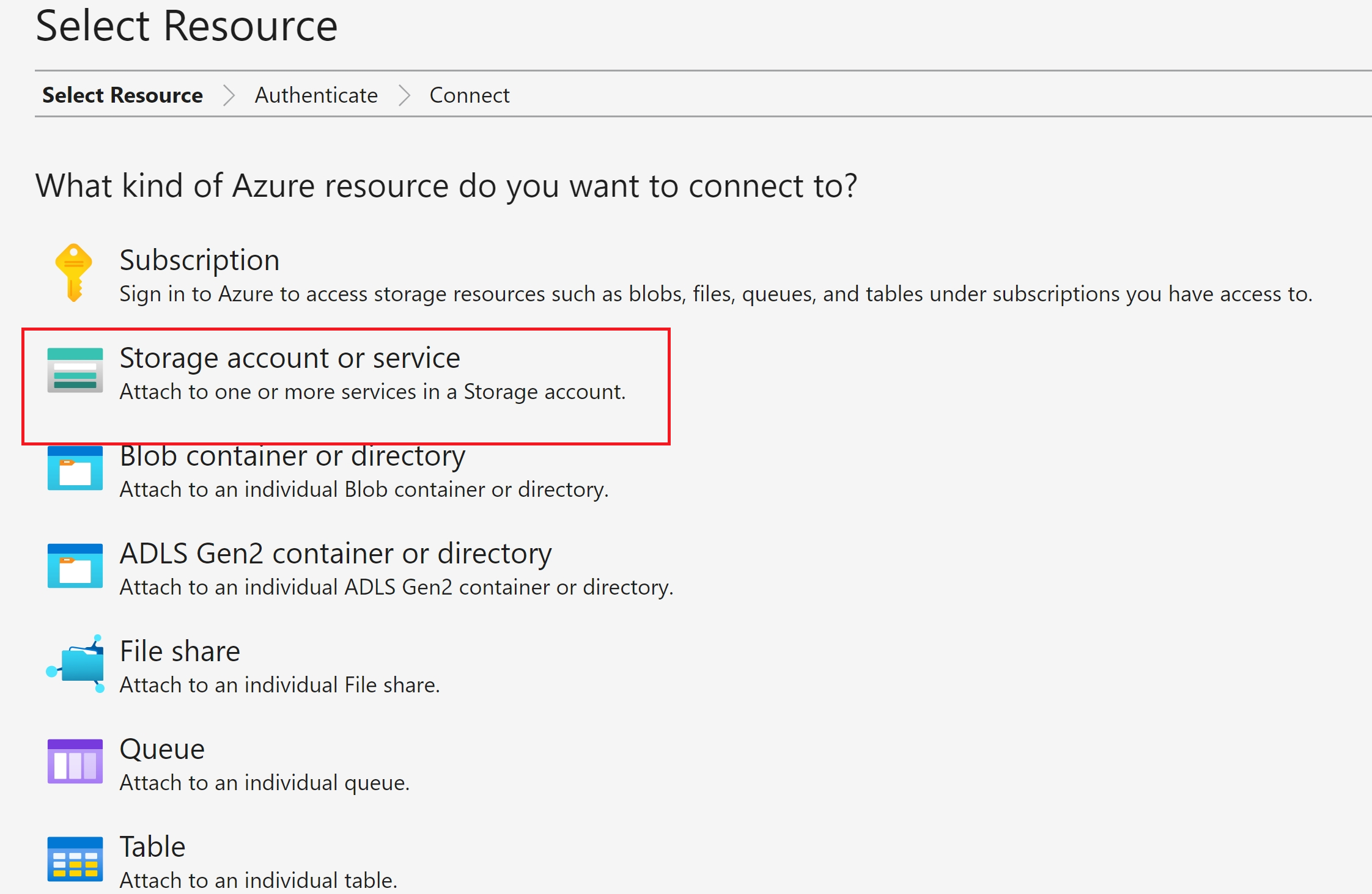
Selected ‘Storage Account or Service’
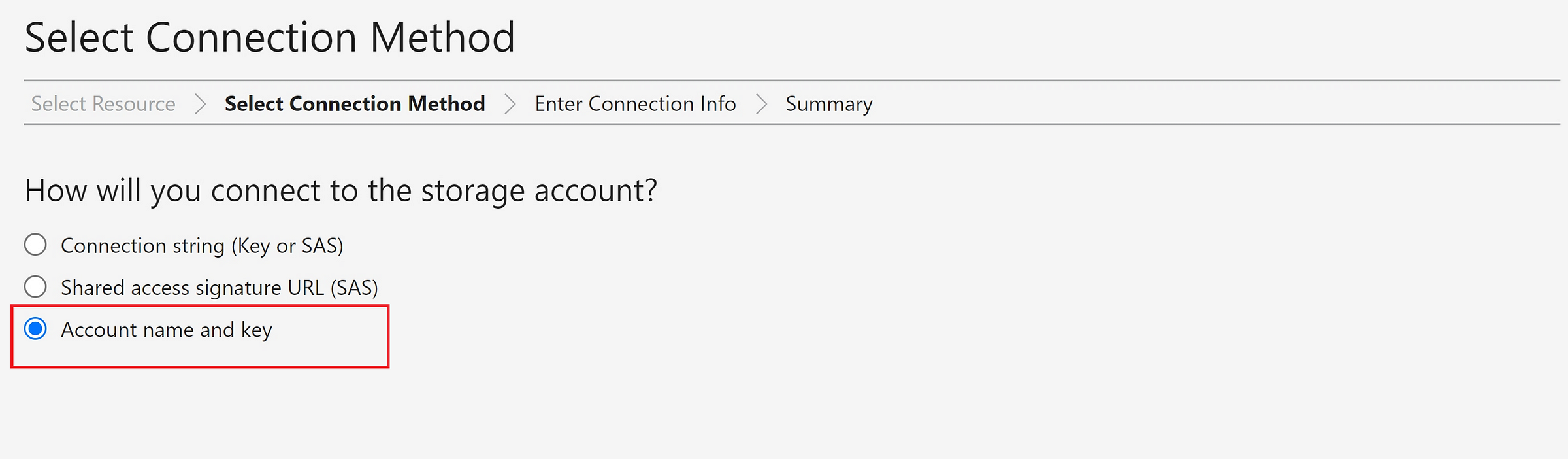
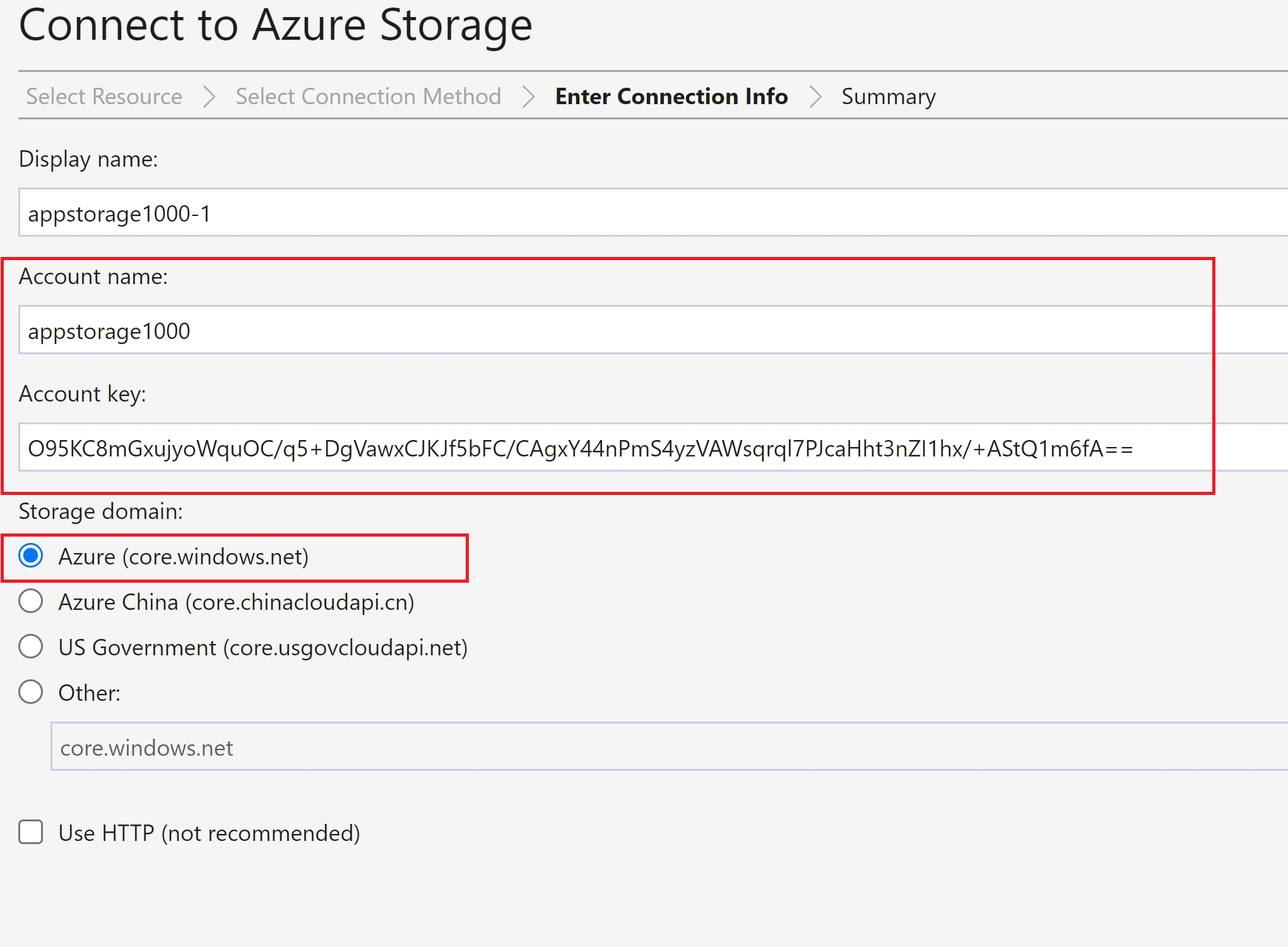
Selected ‘Account name and key’
Copy the account name and keys from the settings
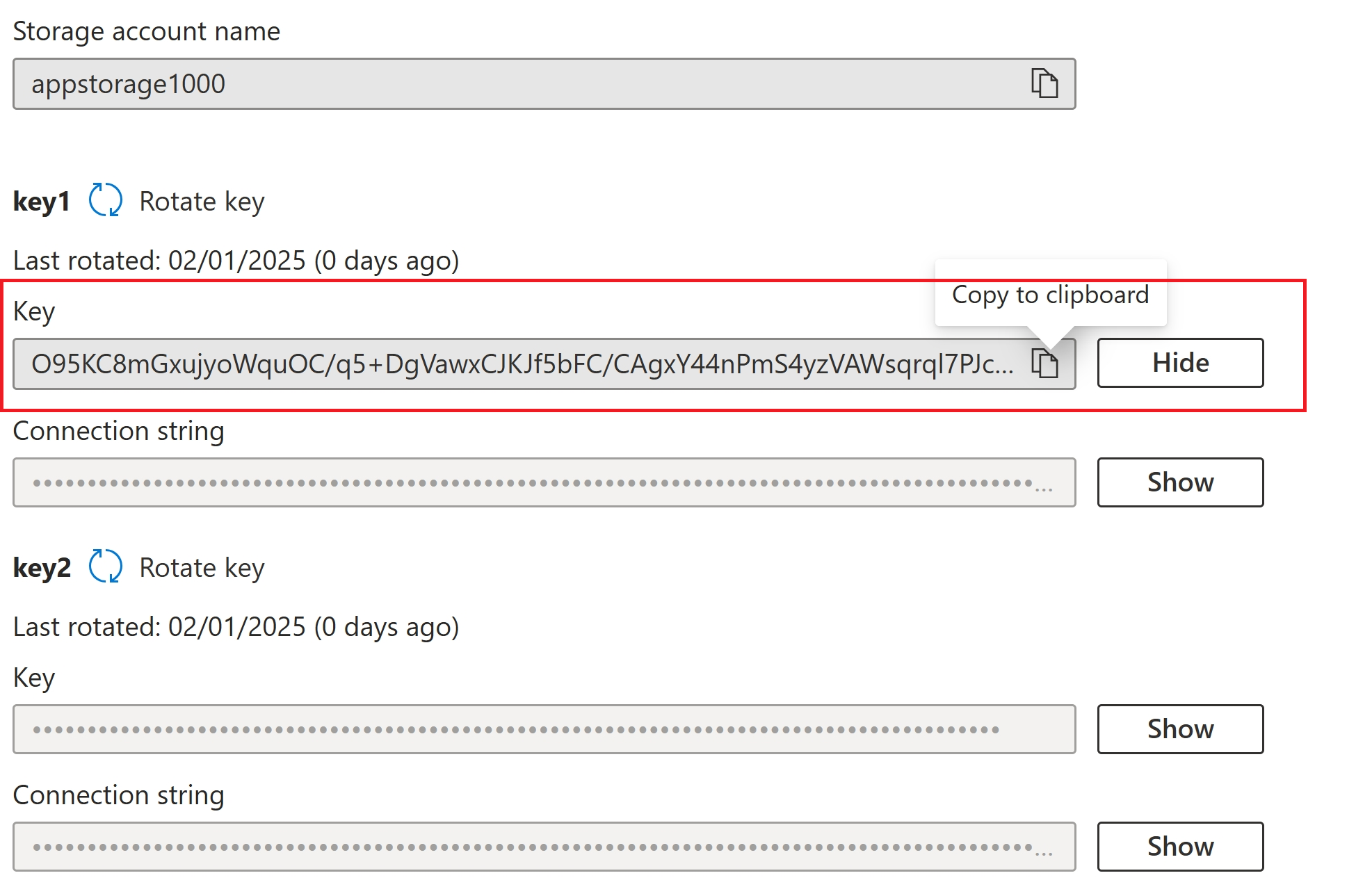
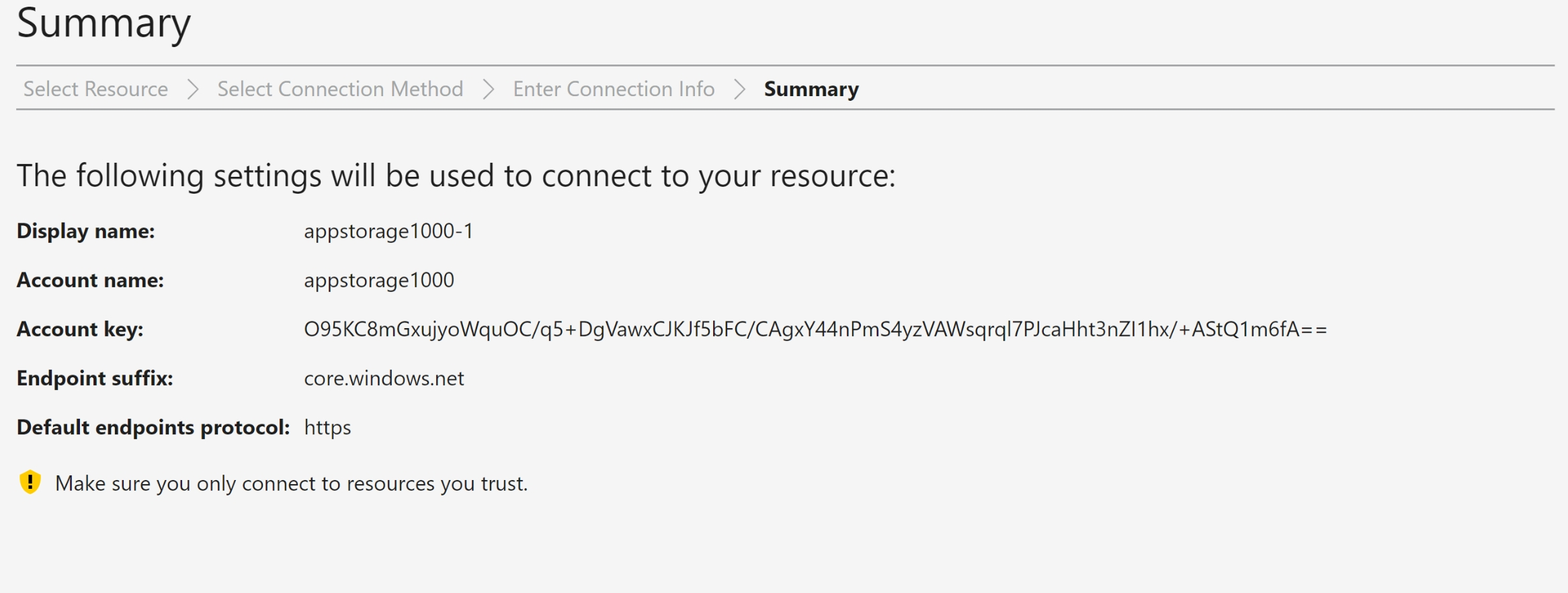
Provided the details and connected to Azure Storage Account
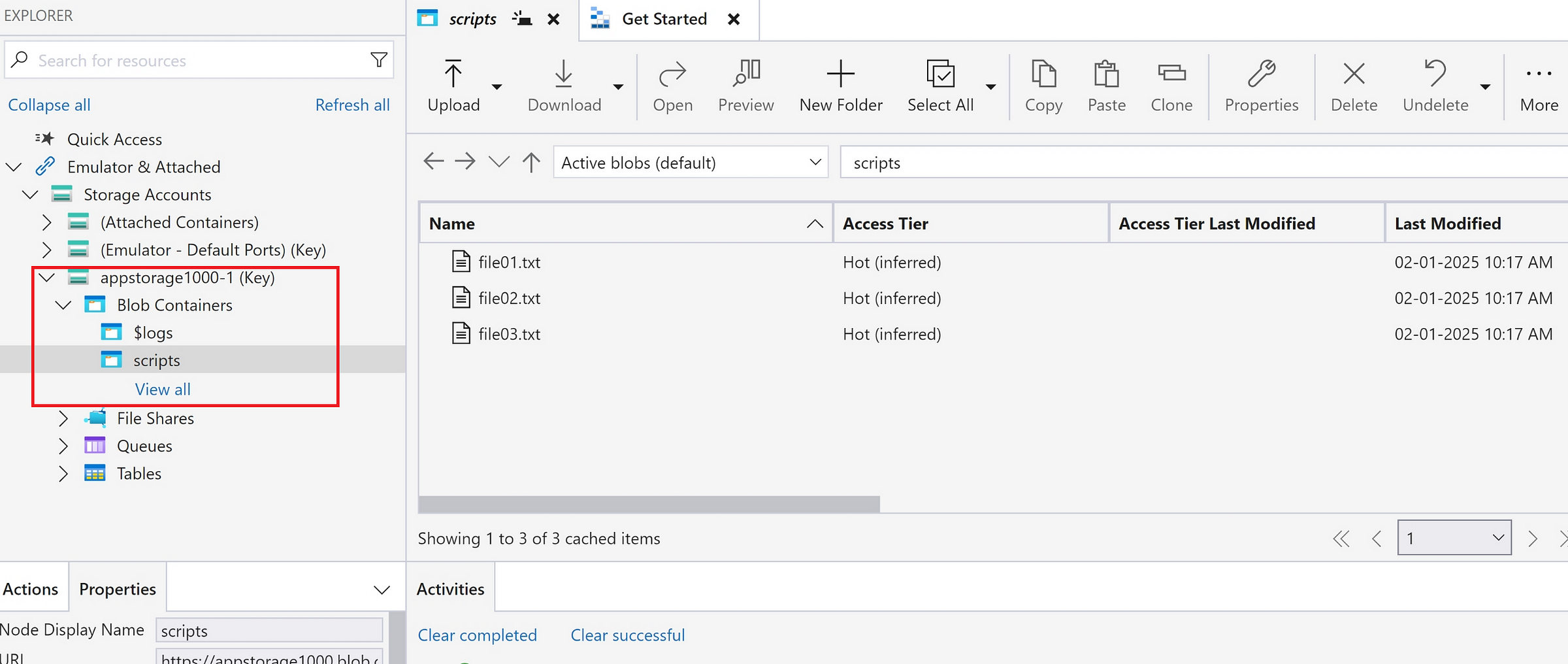
As Account keys have all the permissions, we could be able to see the files in the containers, will be able to view, edit, delete the files
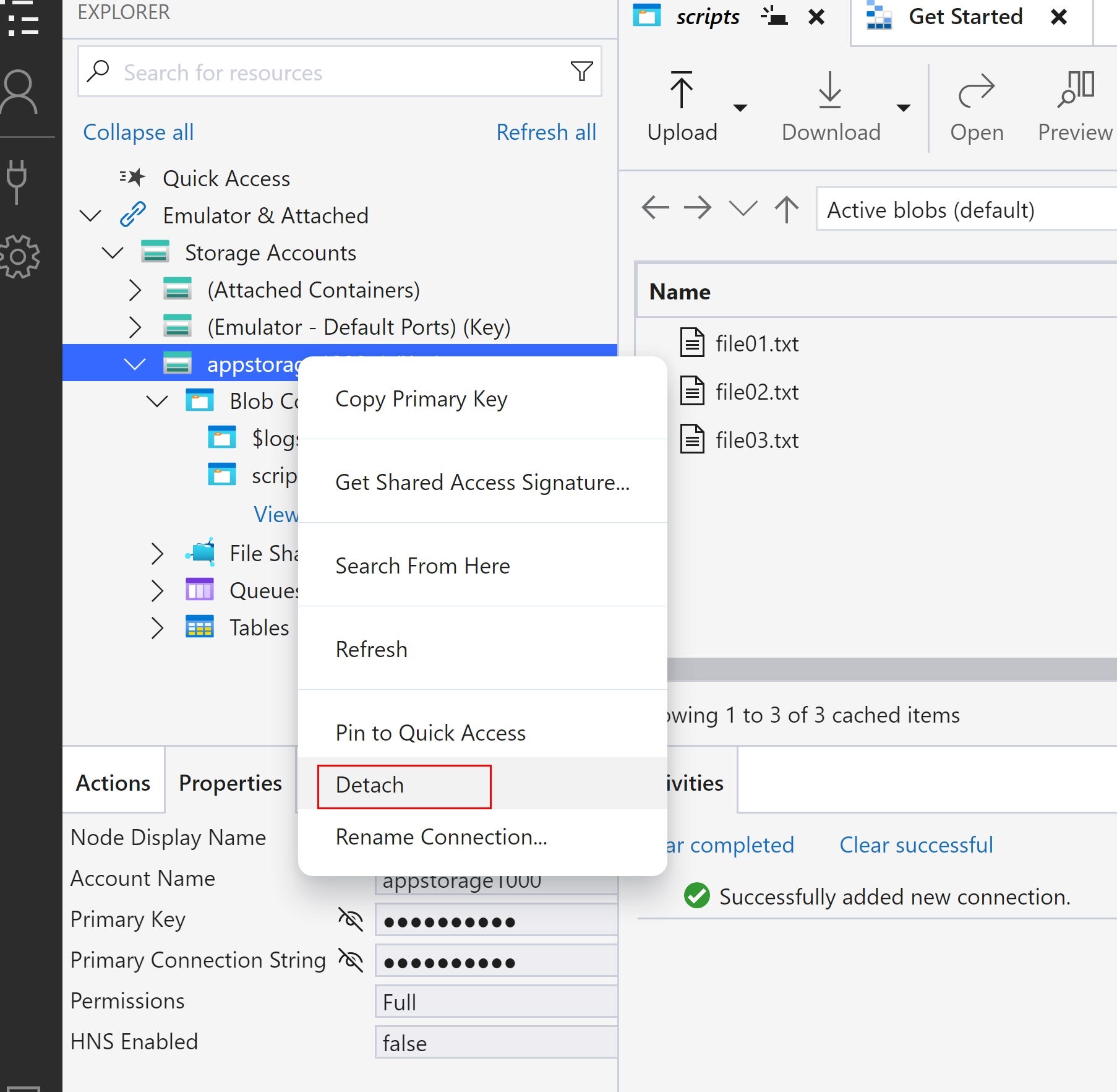
To disconnect, right click and detach the storage account as below.
Access Storage Account in Azure Storage Explorer using Shared Access Signature Token(SAS)
- SAS provides more convenient and secure access to Azure Storage Accounts using time-bound options, policies, but misconfiguration might lead to unnecessary access.
- SAS tokens can be generated at Storage account level, container level and individual file level.
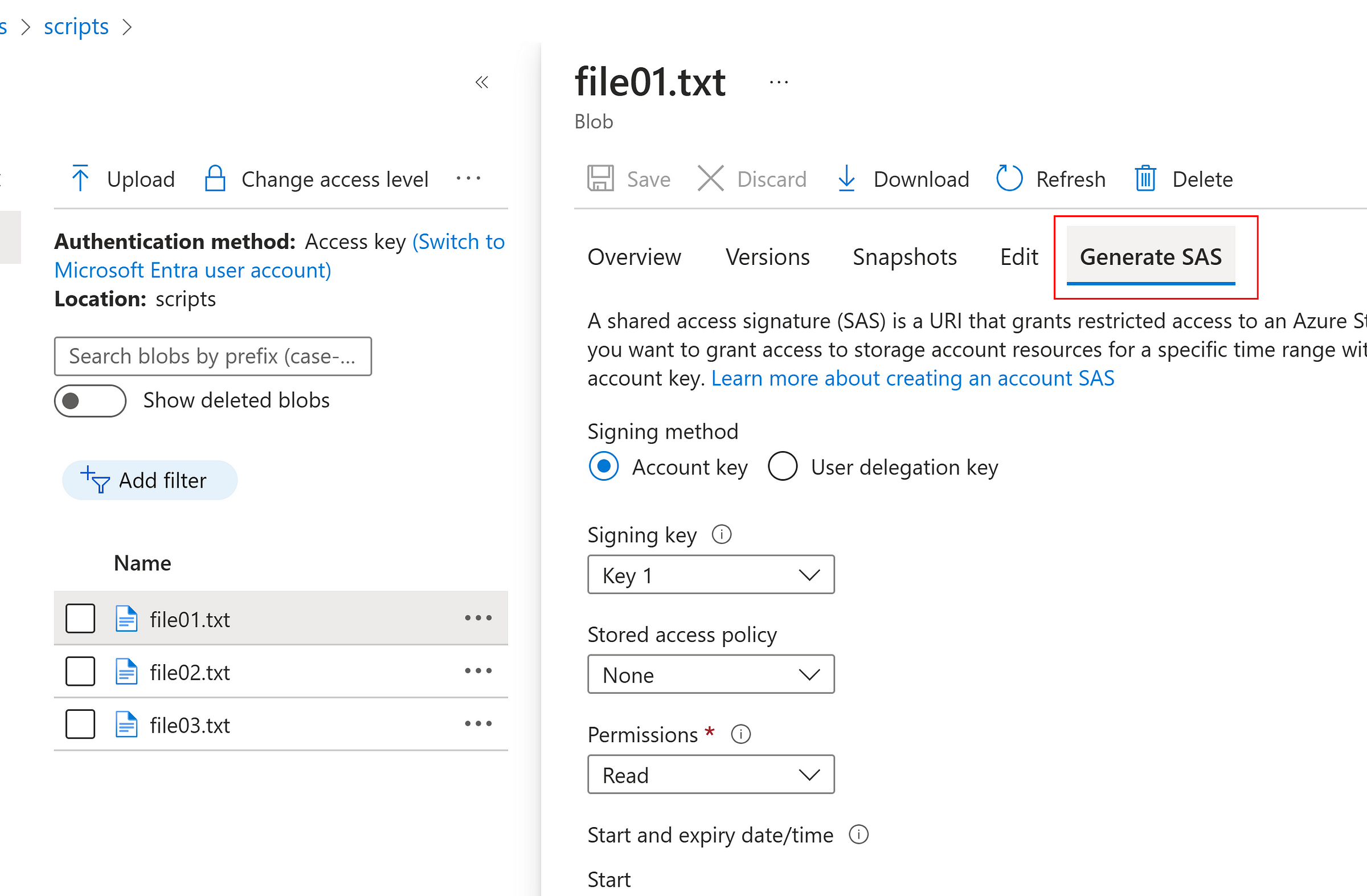
Generate SAS at file level
- It uses the account key as sign-in key to generate SAS token
- Select the permissions as needed
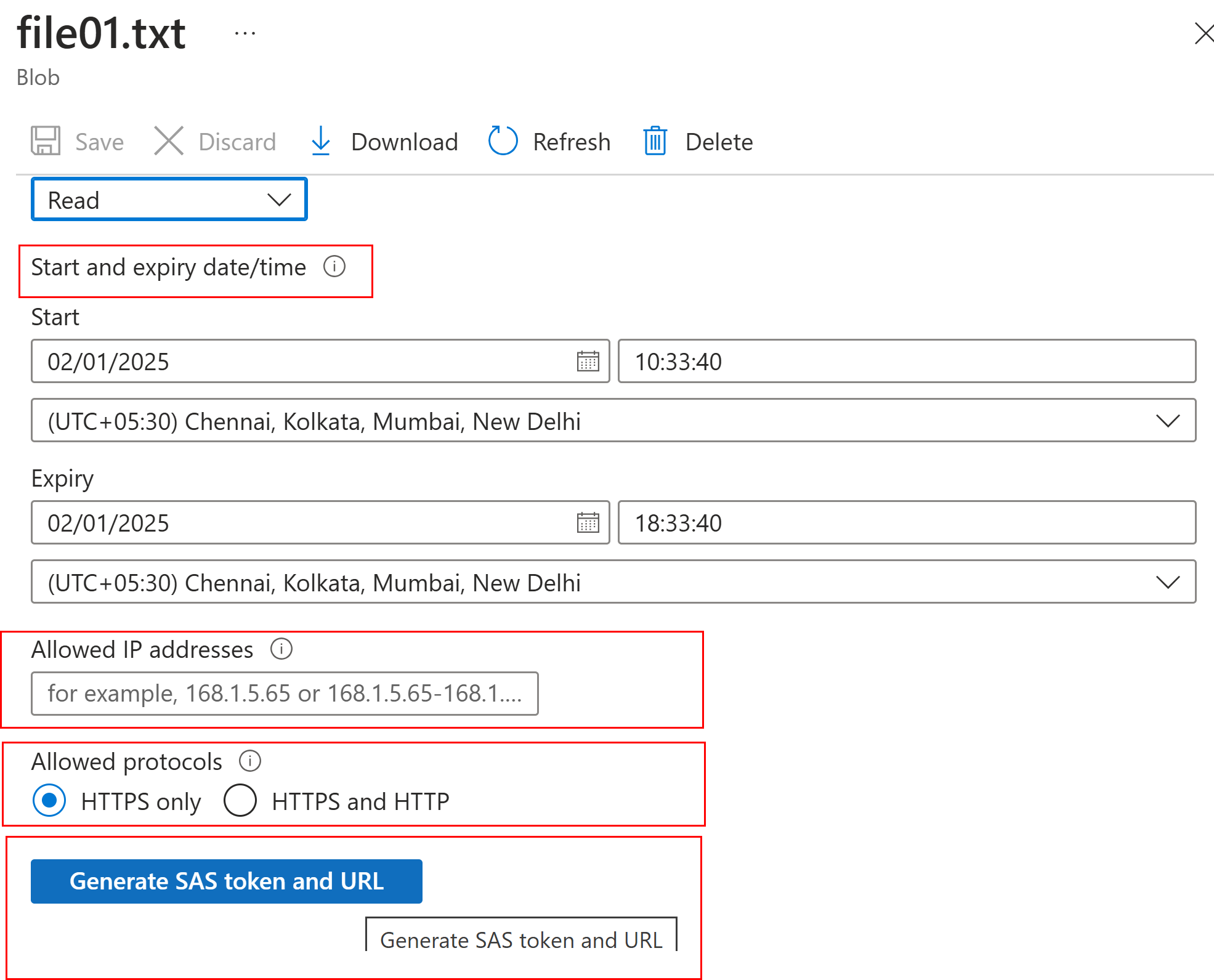
- Select the start and end time for access
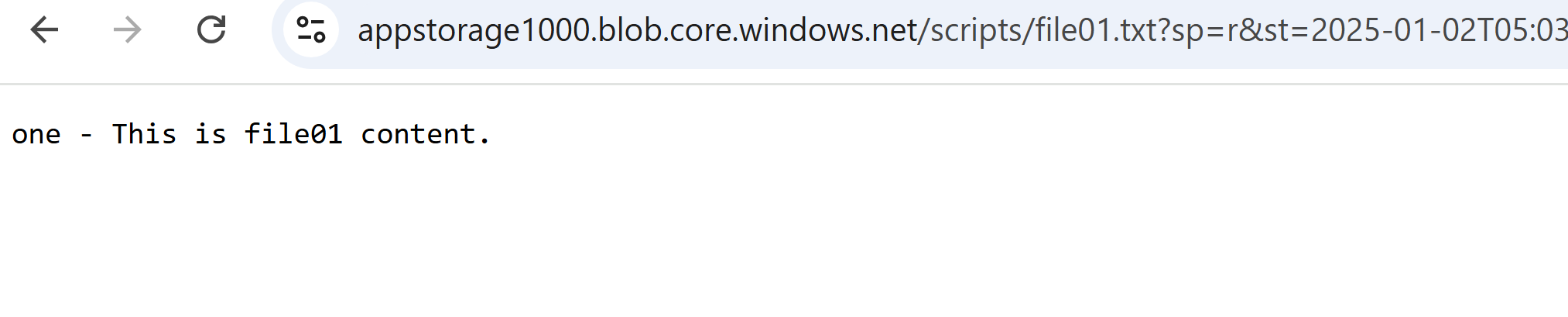
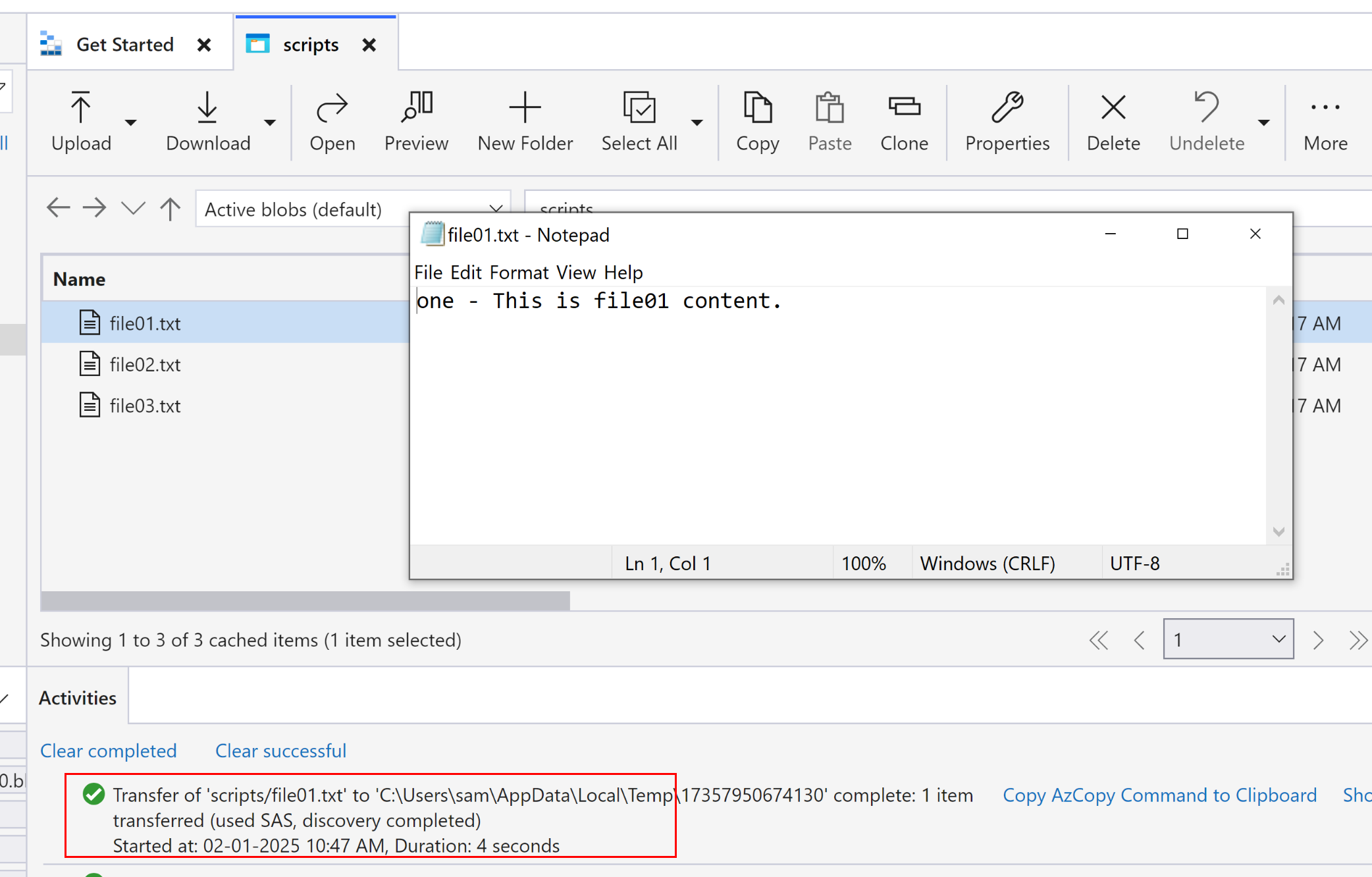
- once the token url is generated, file content can be access via a public browser
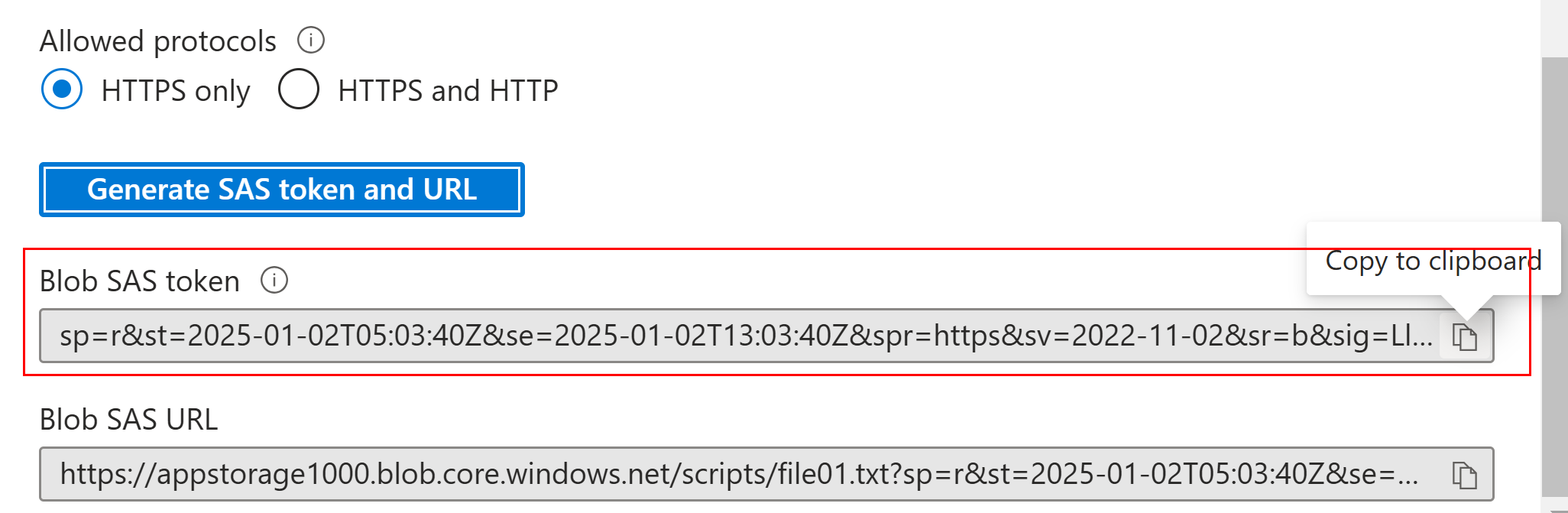
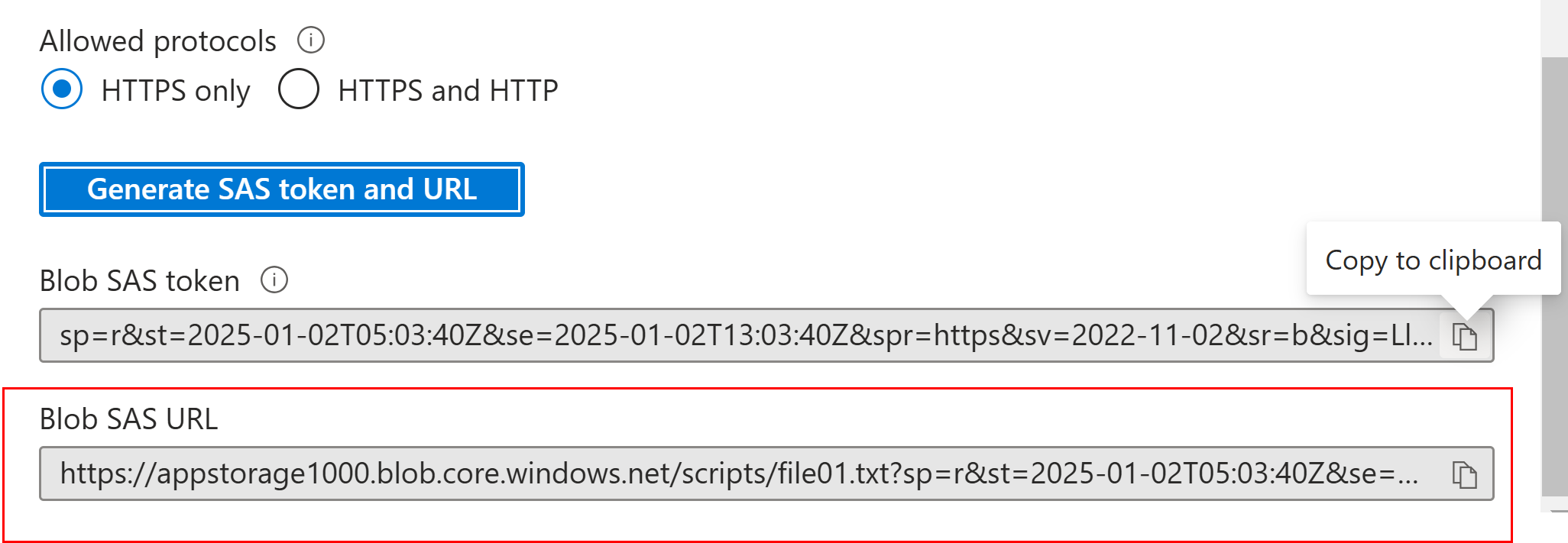
File content is visible as the READ permission was set while generating SAS token
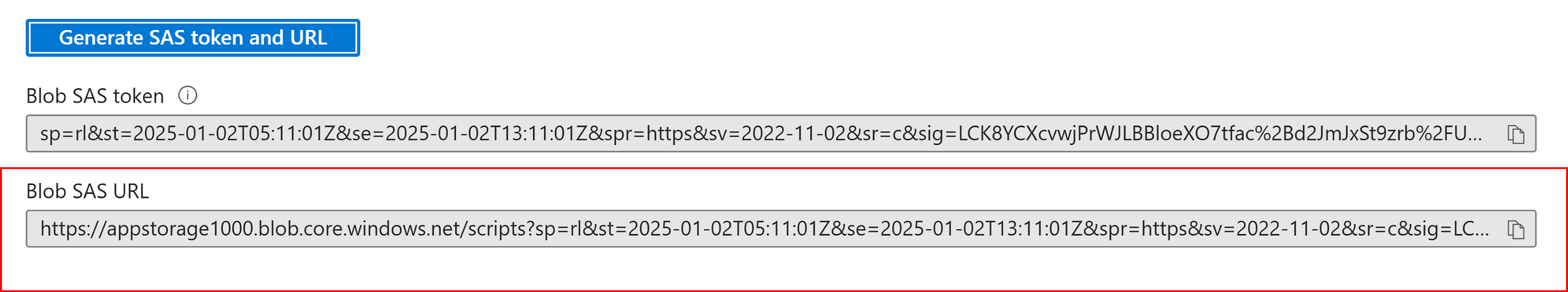
Generate SAS at container level:
Permissions: Read and List
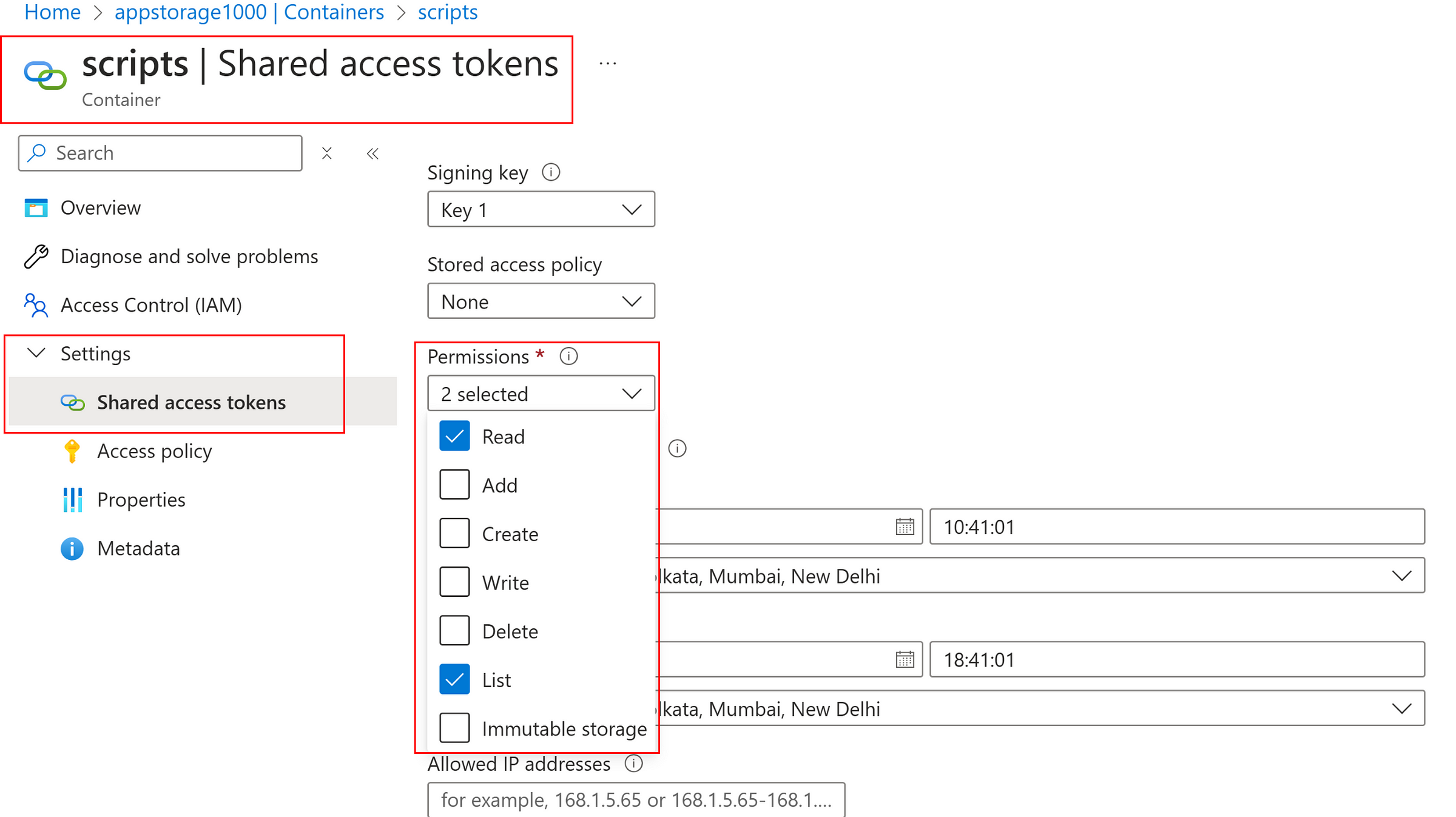
Azure Storage Explorer → Blob Container or directory
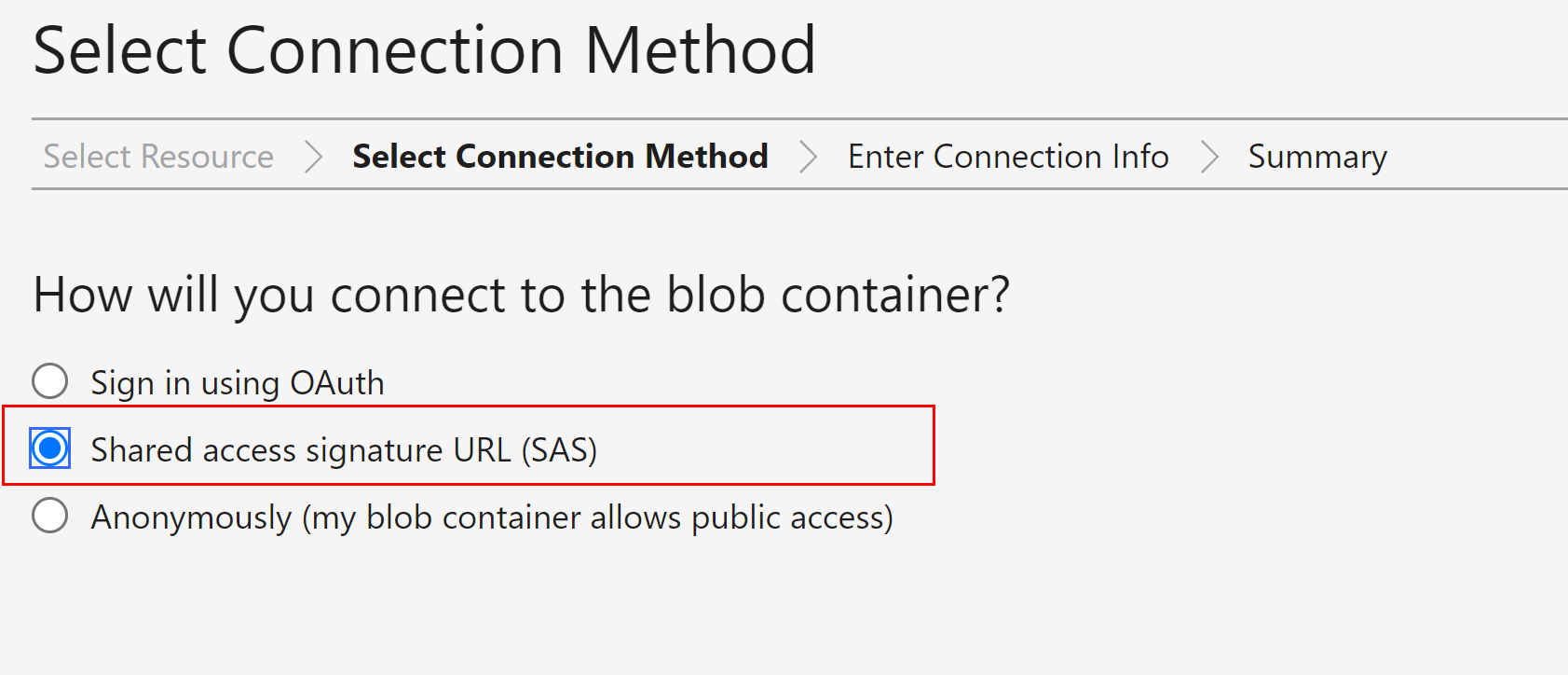
Select connection method as SAS
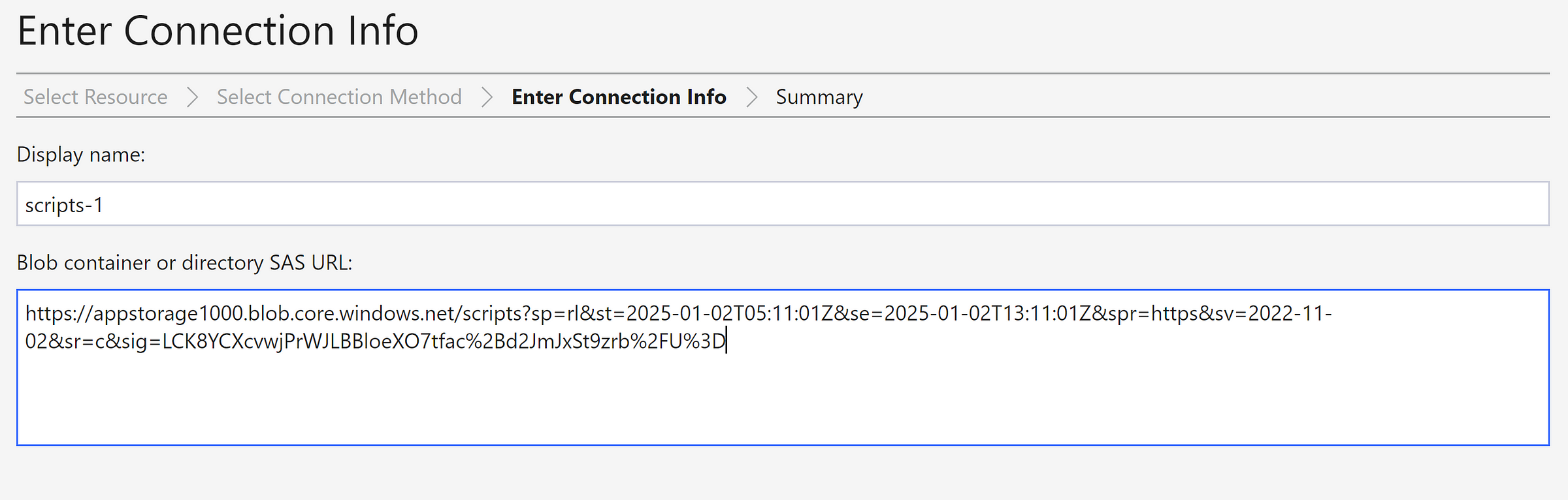
Provide the SAS connection URL
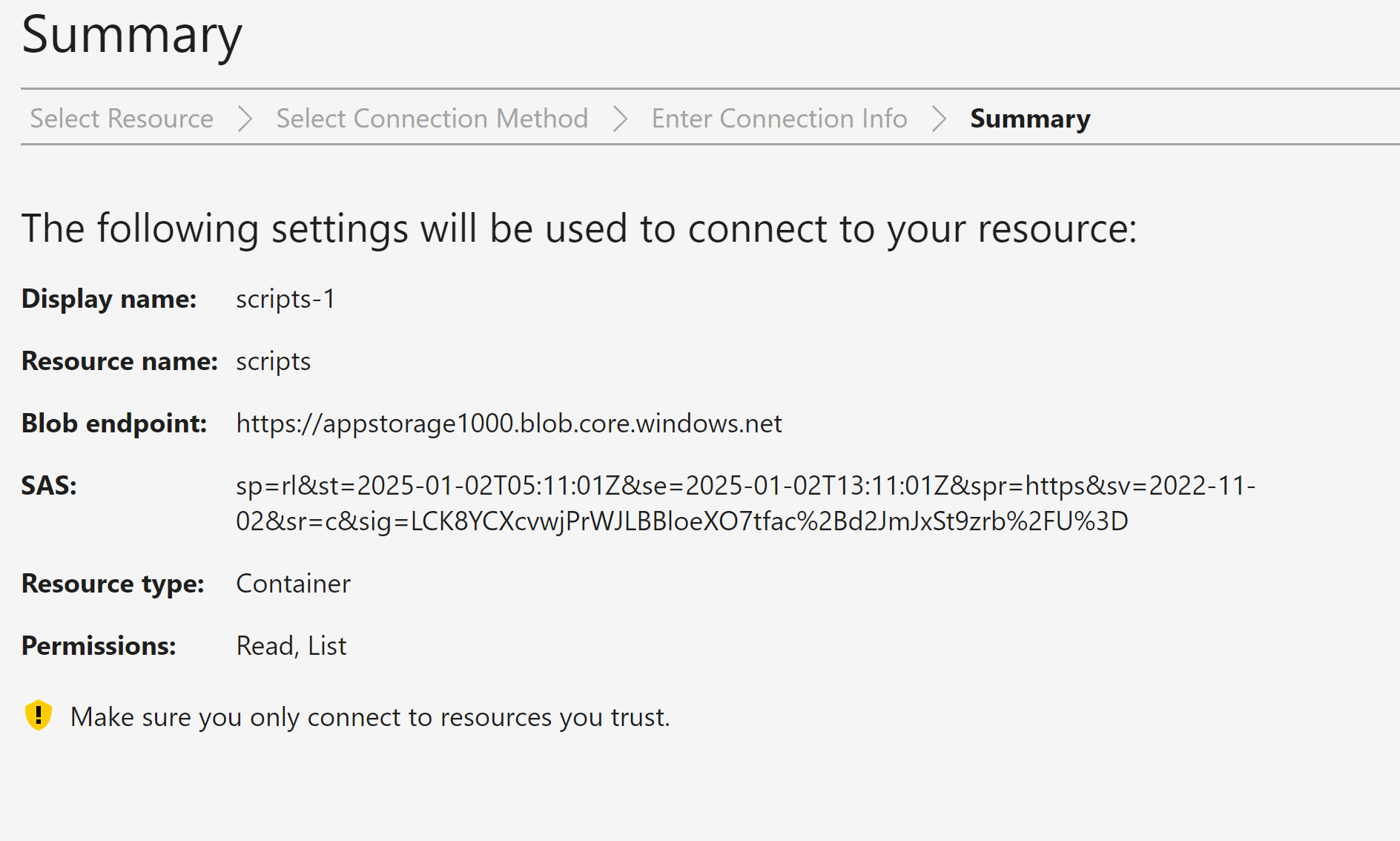
As READ and LIST permissions are set, we can able to see the list of files in container and able to see the data.
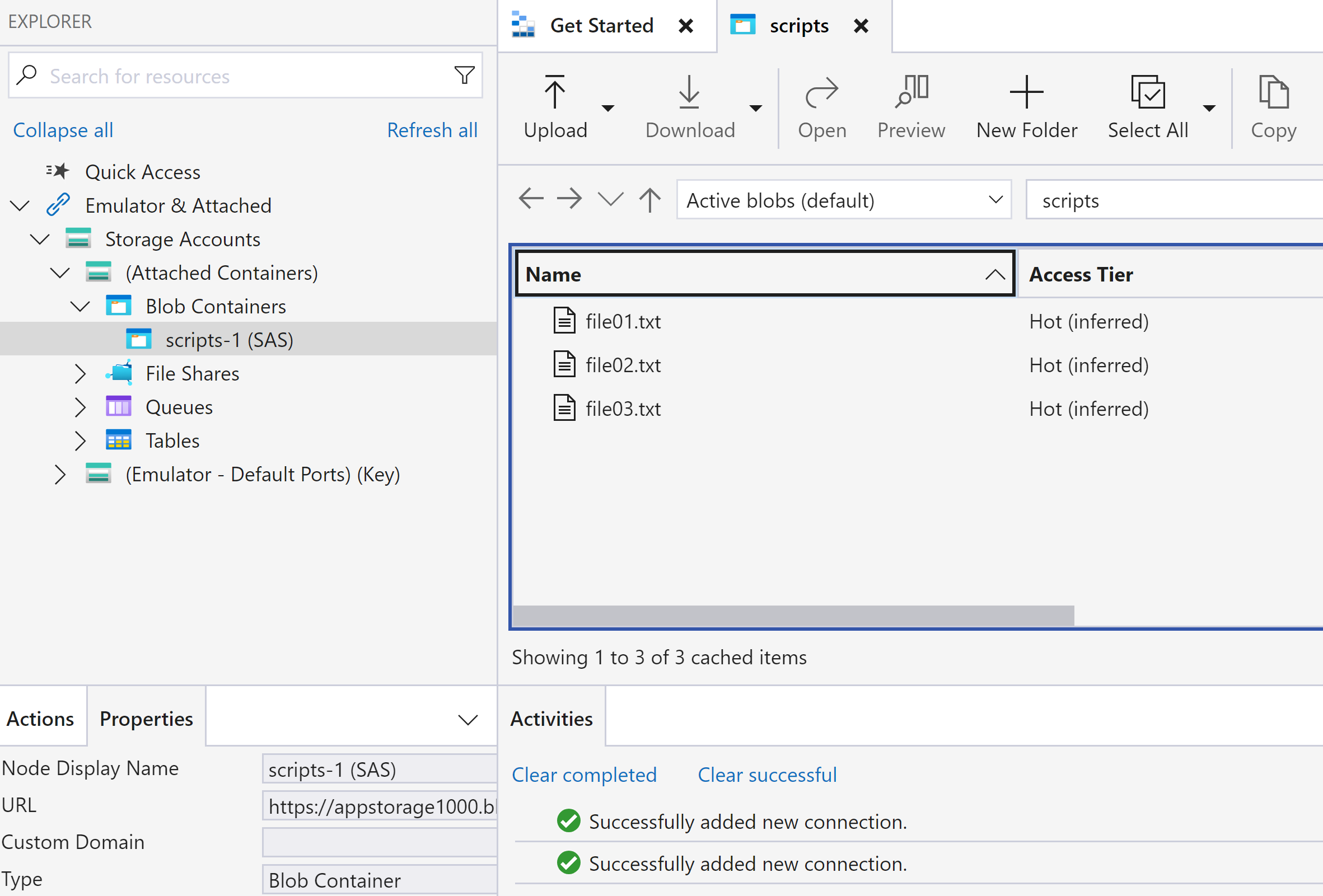
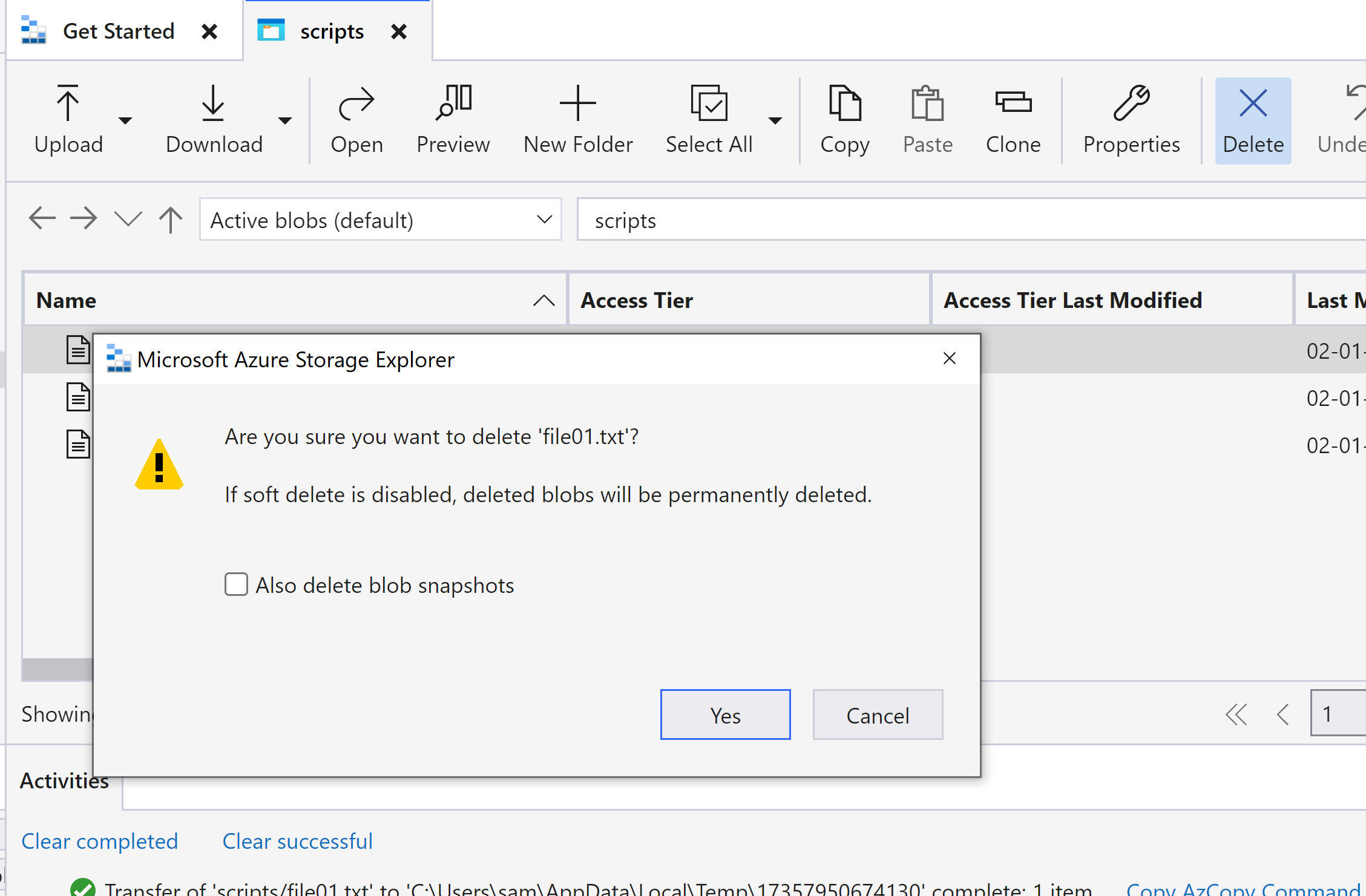
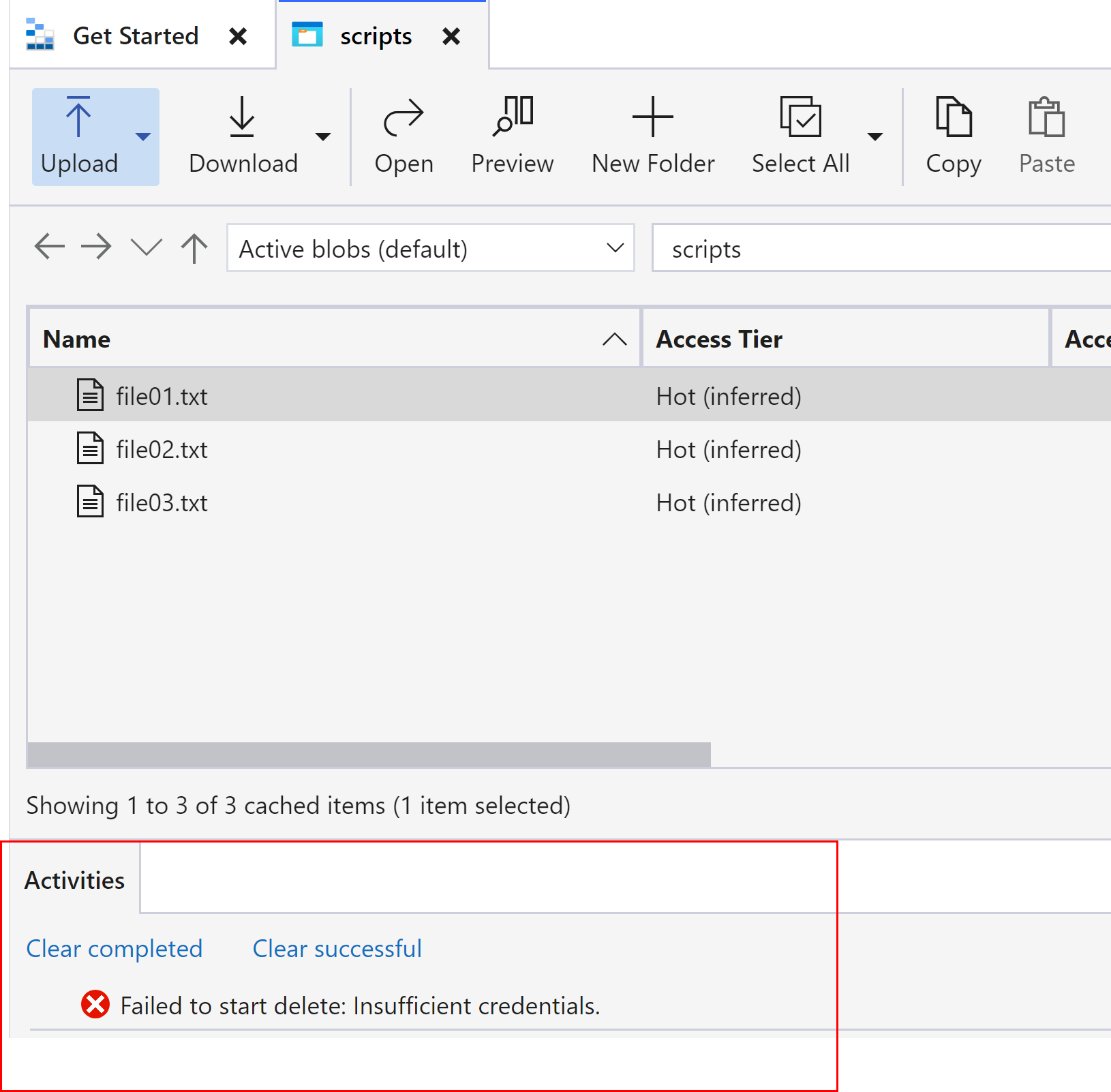
Delete is denied as no delete permission was set during SAS token generation.
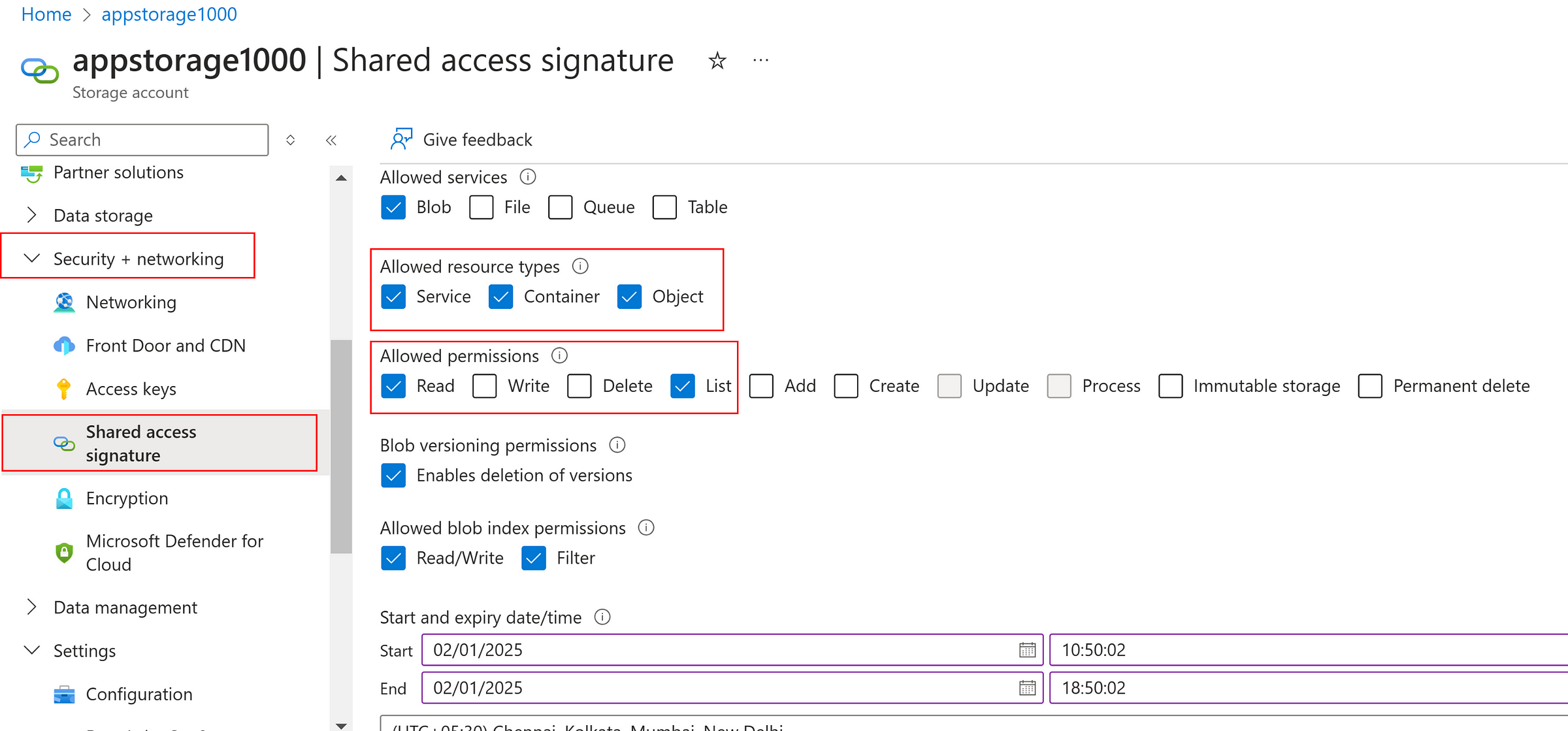
Generate SAS at Storage Account level
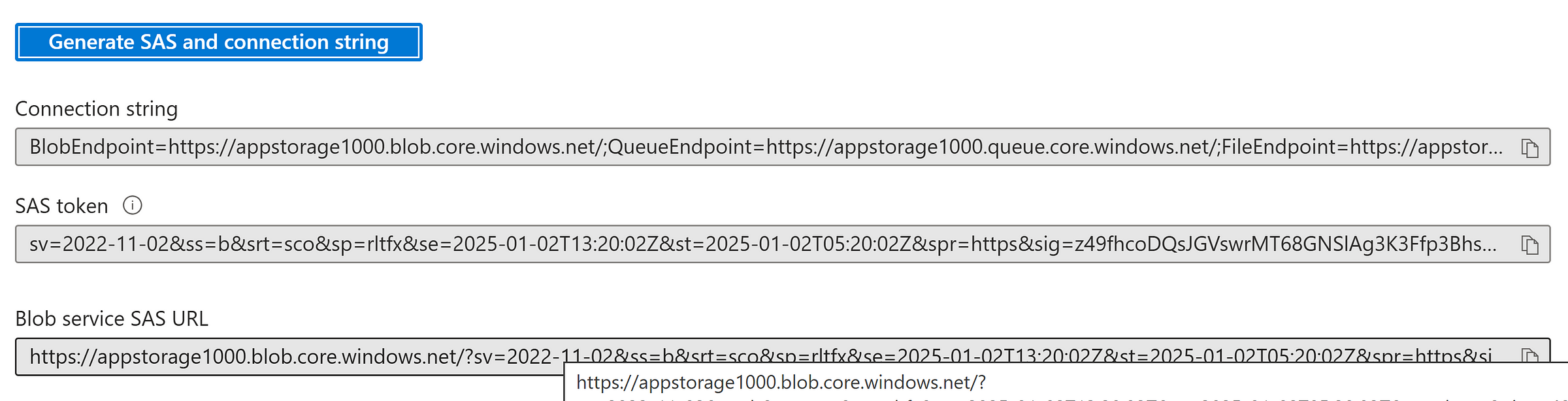
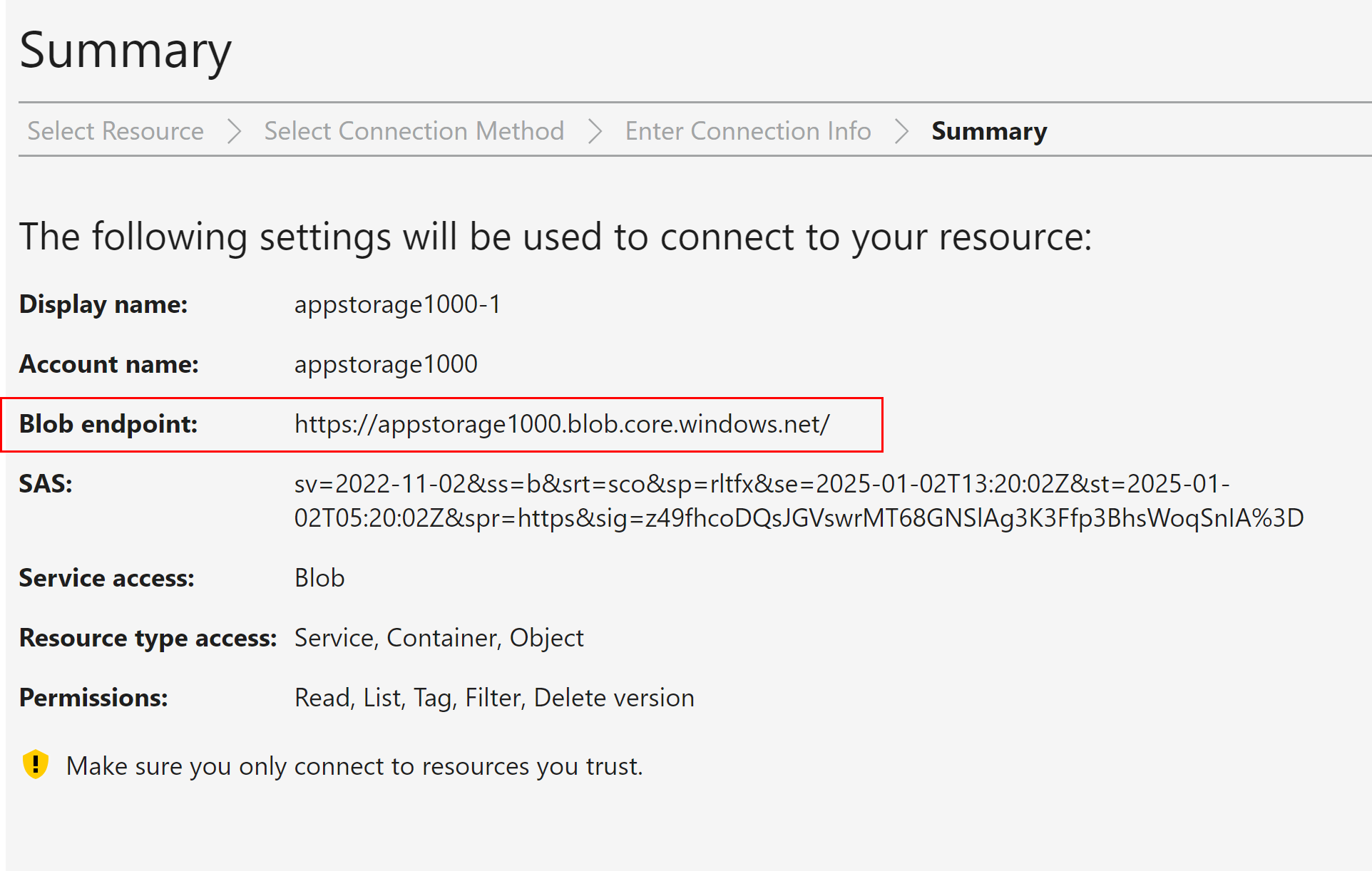
Enter the SAS token URL and connect
How to invalidate the SAS token when it gets into wrong hands?
Option 1
When the SAS token is generated, the key input is Sign-In key which is the Access Keys defined at storage account.
So, by ‘Rotating the Key’ the Key-1 will get deleted and Key-2 will become the primary(key-1) which will invalidate all the SAS token generated using the old key-1.
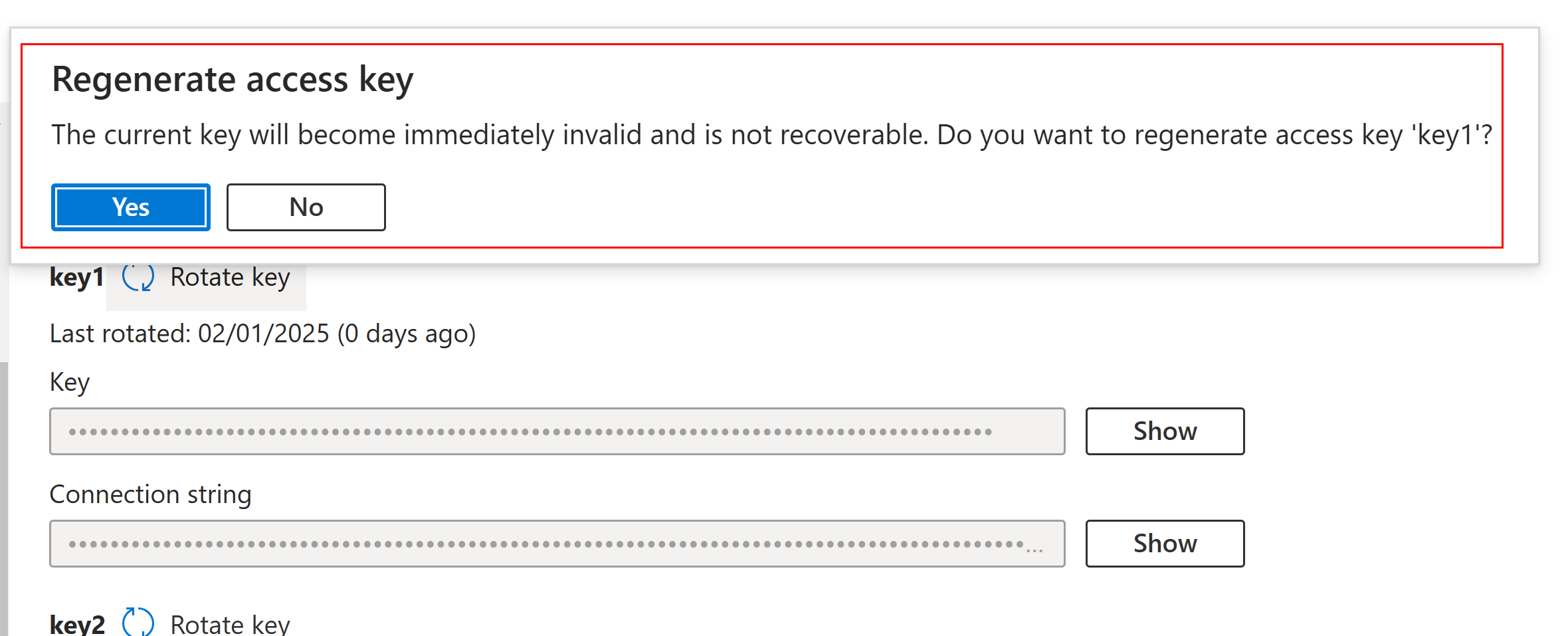
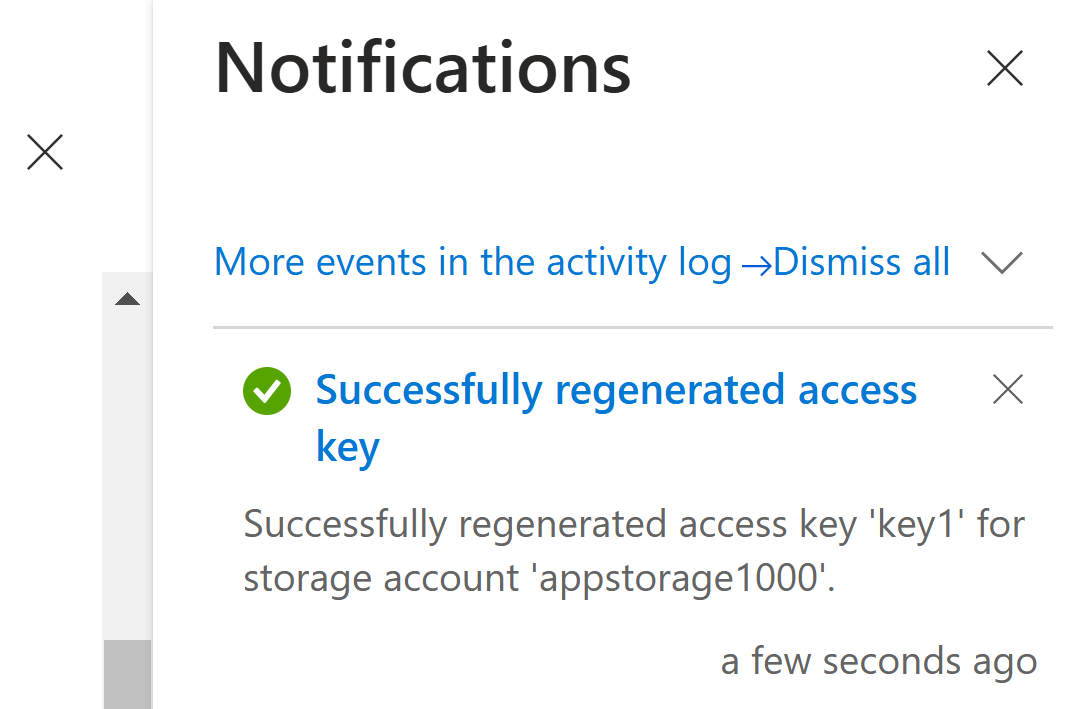
Refresh the connection in Azure Storage Explorer which was connected using the SAS token which used the old key-1 for SAS token generation.
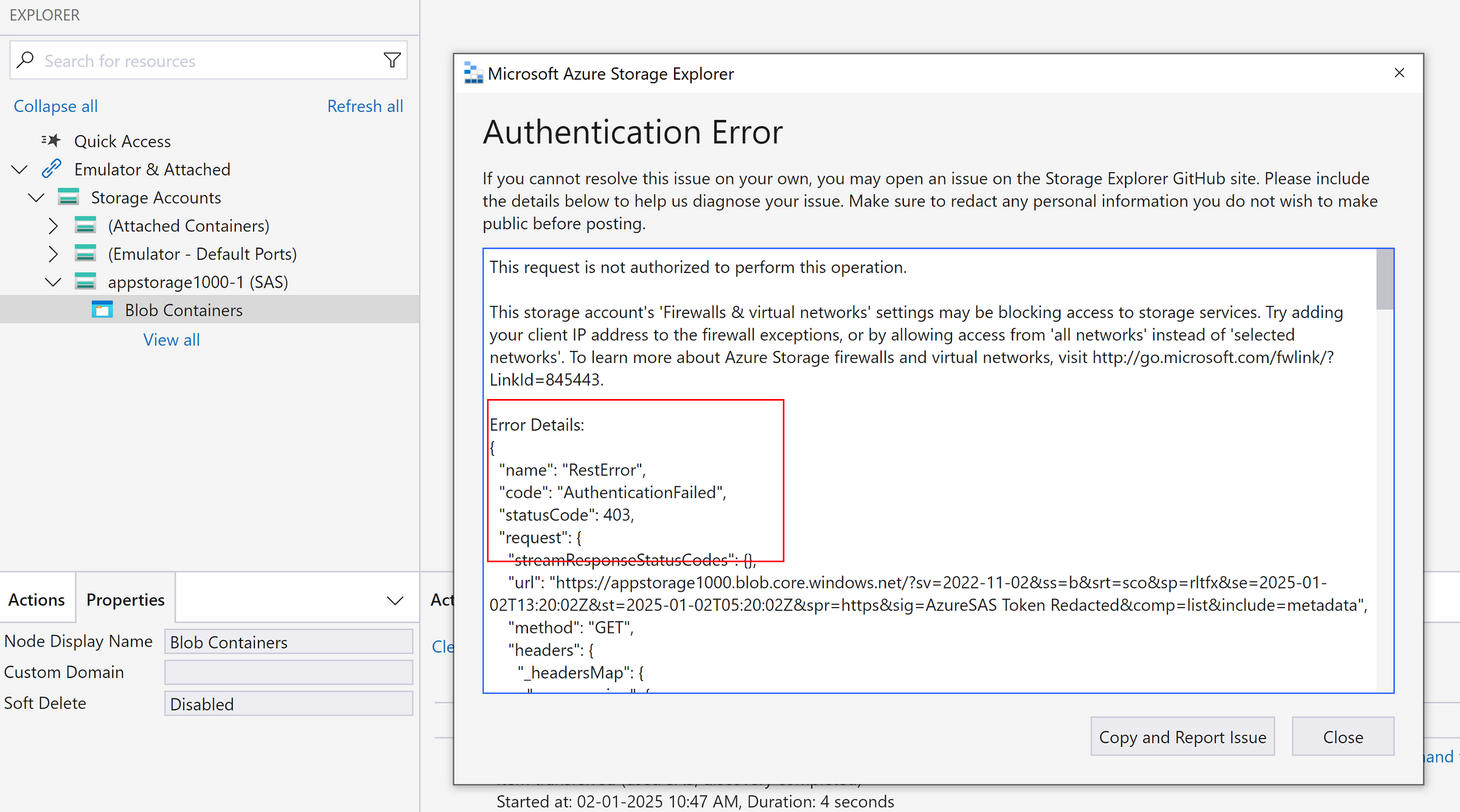
Now, we got the authentication error since the SAS token got invalidated.
Option 2
Access Policies are the alternate and great ways to modify permissions of the SAS token whenever needed.
While generating SAS token, we could select Access Policy as one of the option and Access policies can be edited anytime after the SAS token is generated to modify access.
Create a Access policy at container — scripts
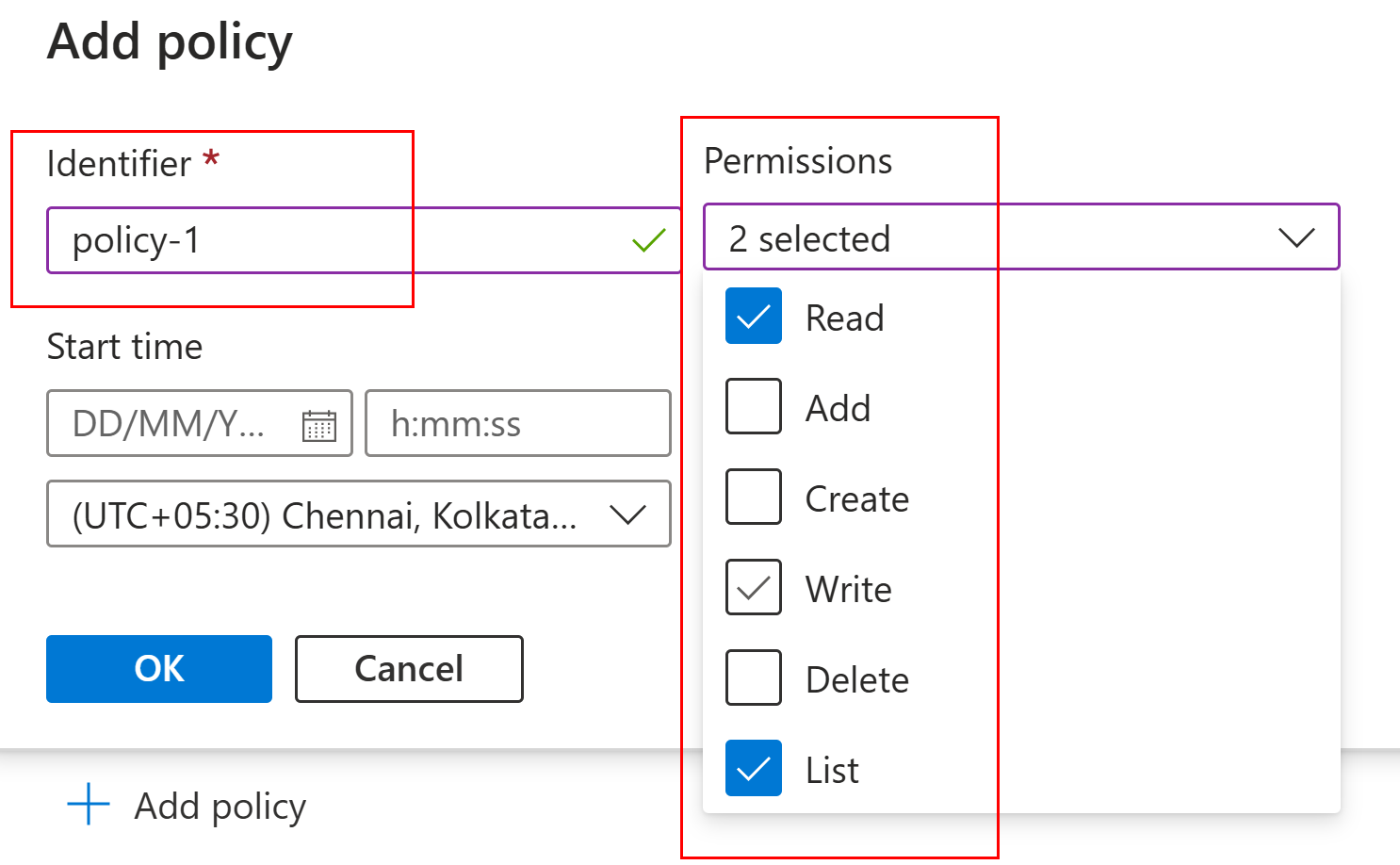
Provide a name, list of permissions needed and the duration.
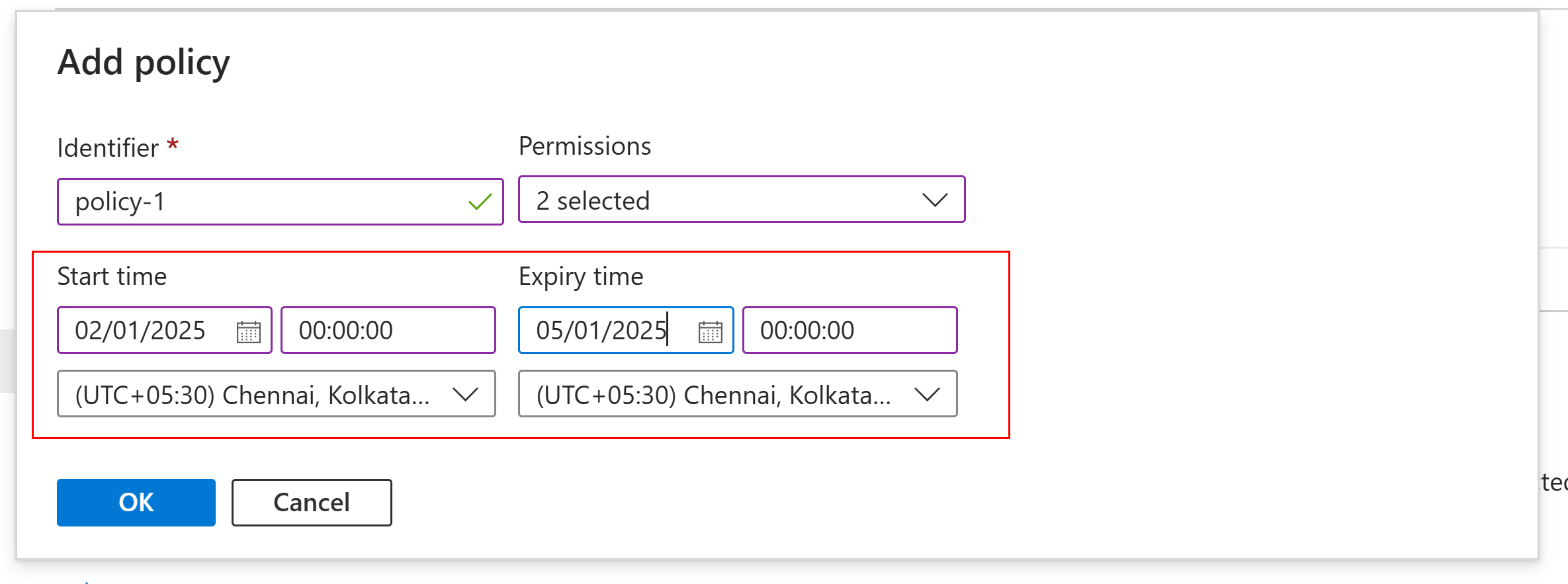
Save the Access policy settings
Generate SAS token at container level using Access Policy — Policy-1
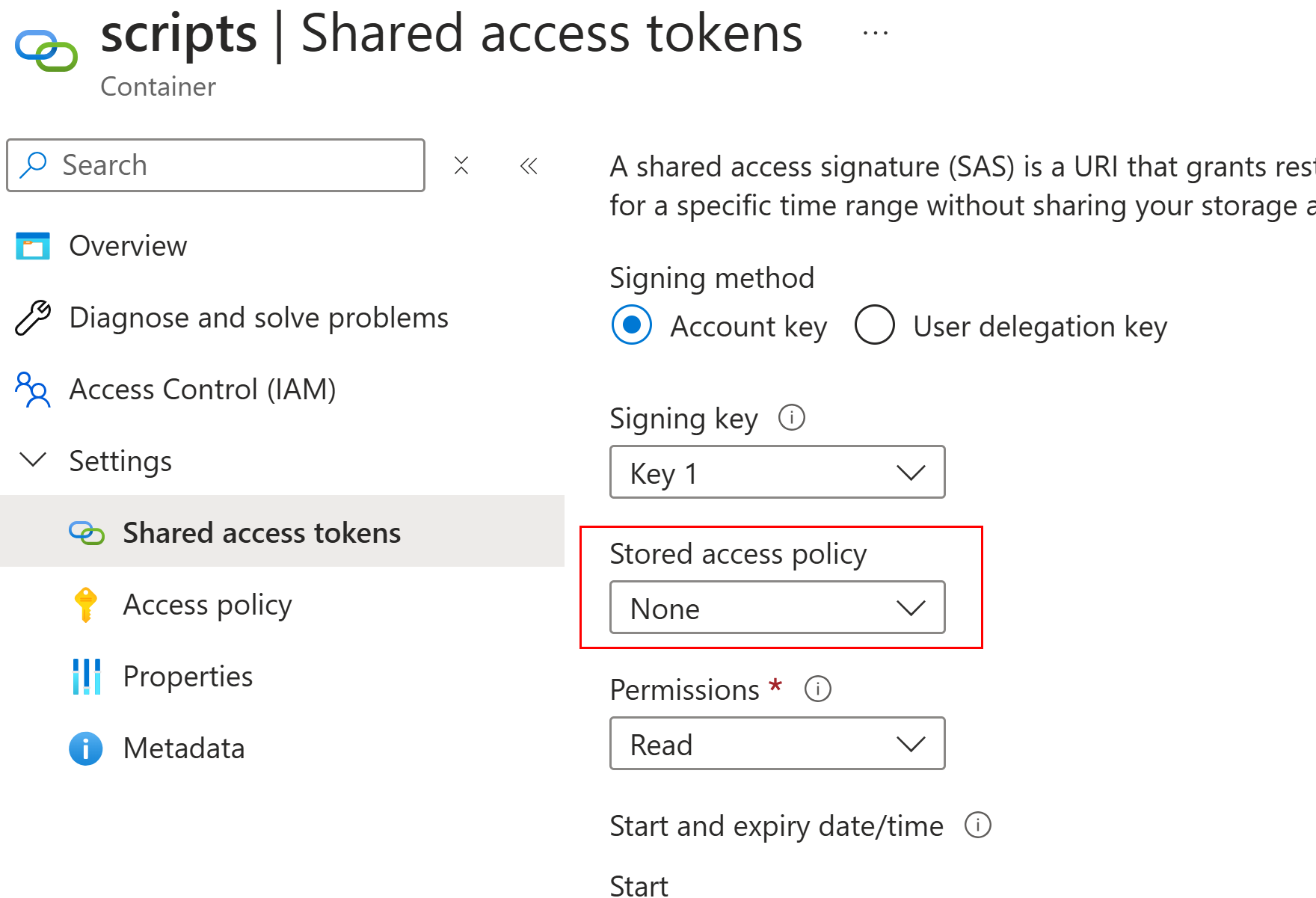
Select Access Policy — Policy-1
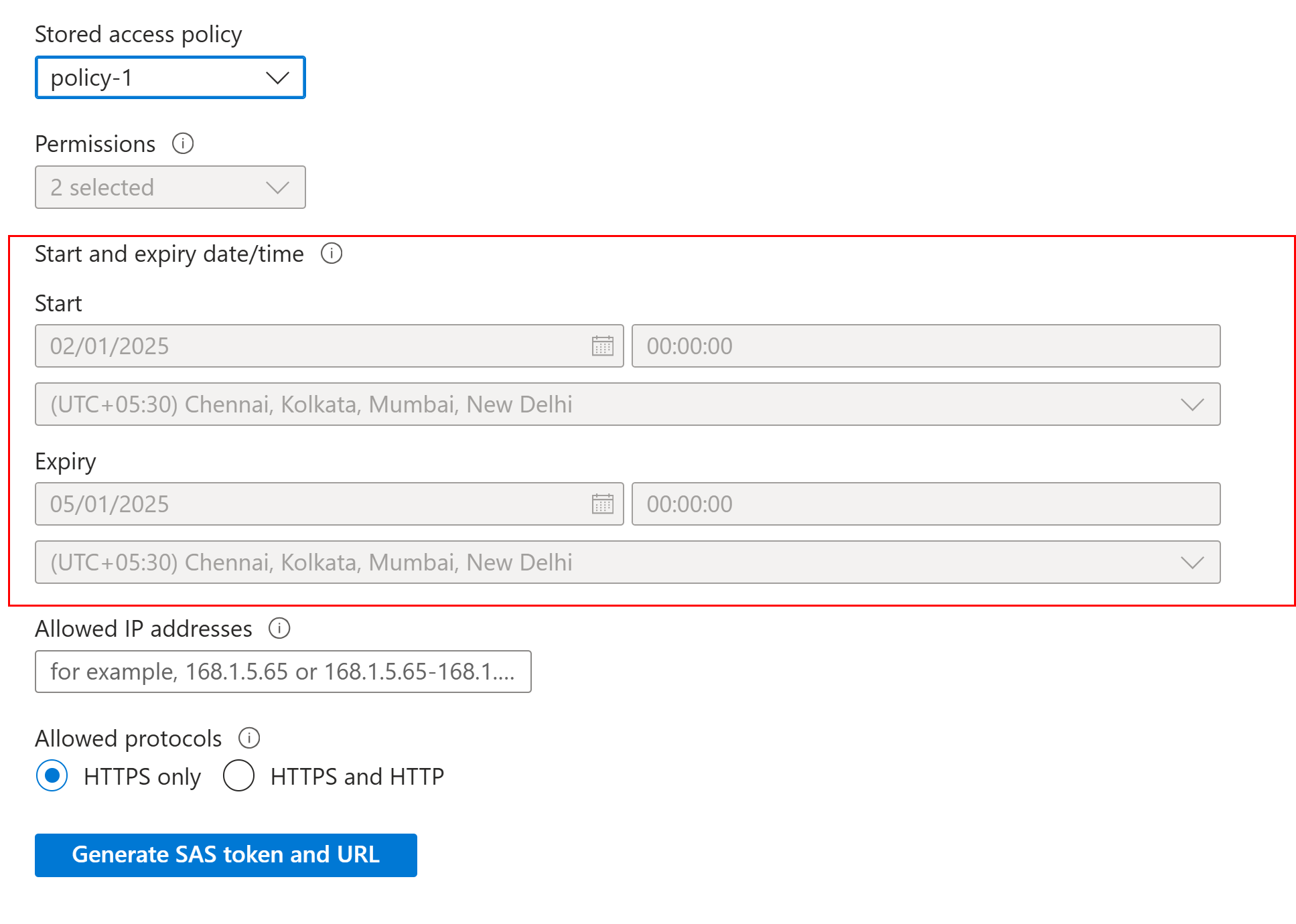
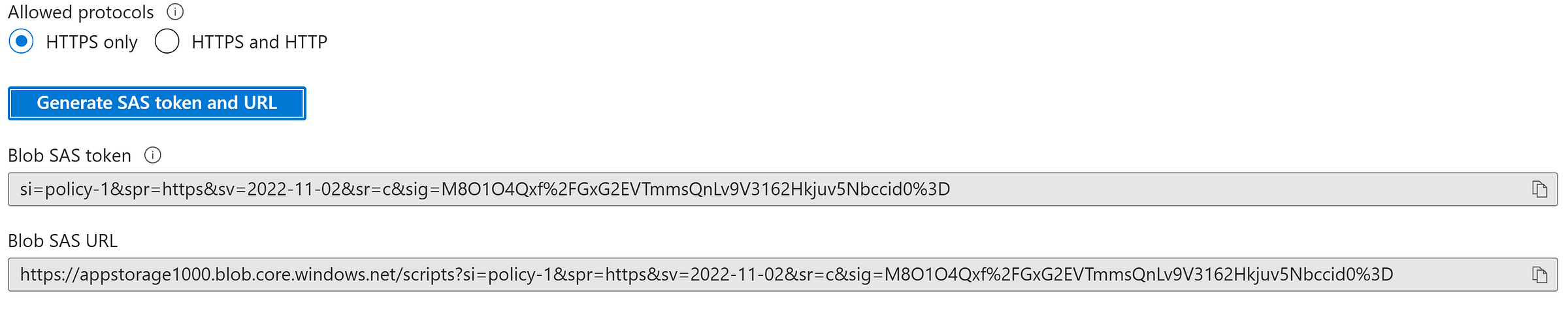
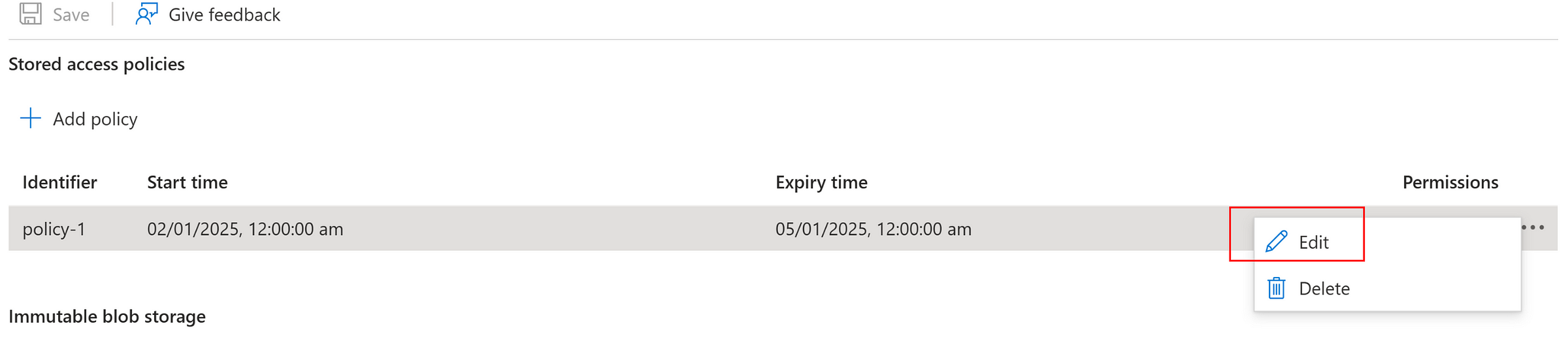
Now we can edit the policy anytime and remove the permissions and he token will behave as expected.
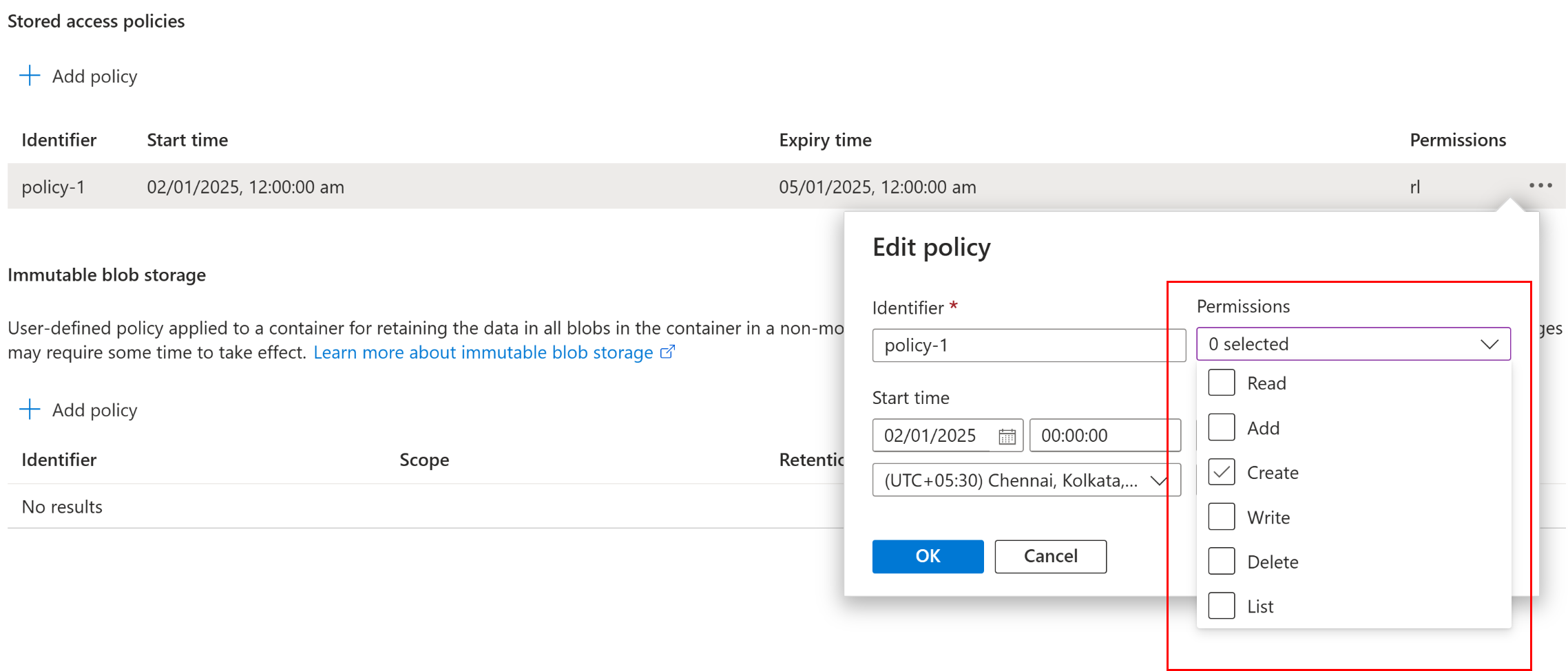
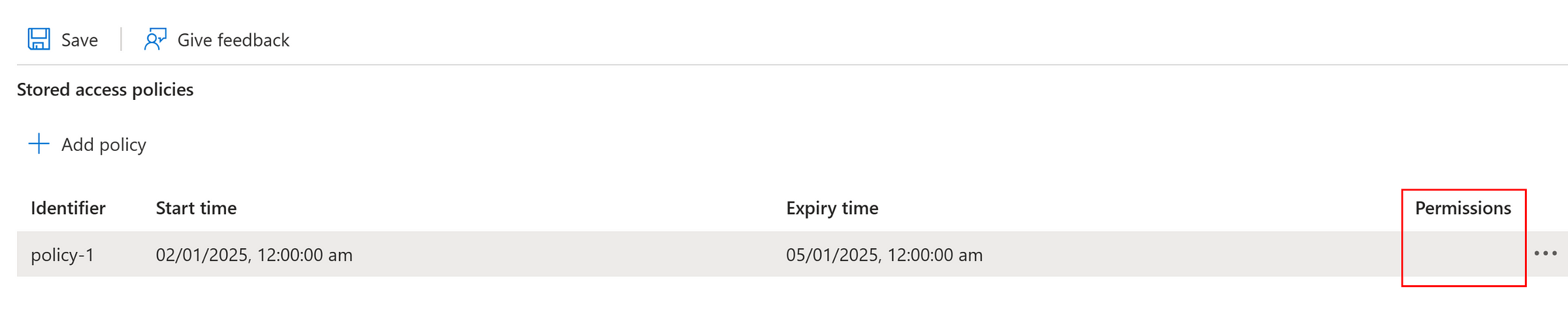
Read, List permissions were removed.
Another important setting in Azure Storage account
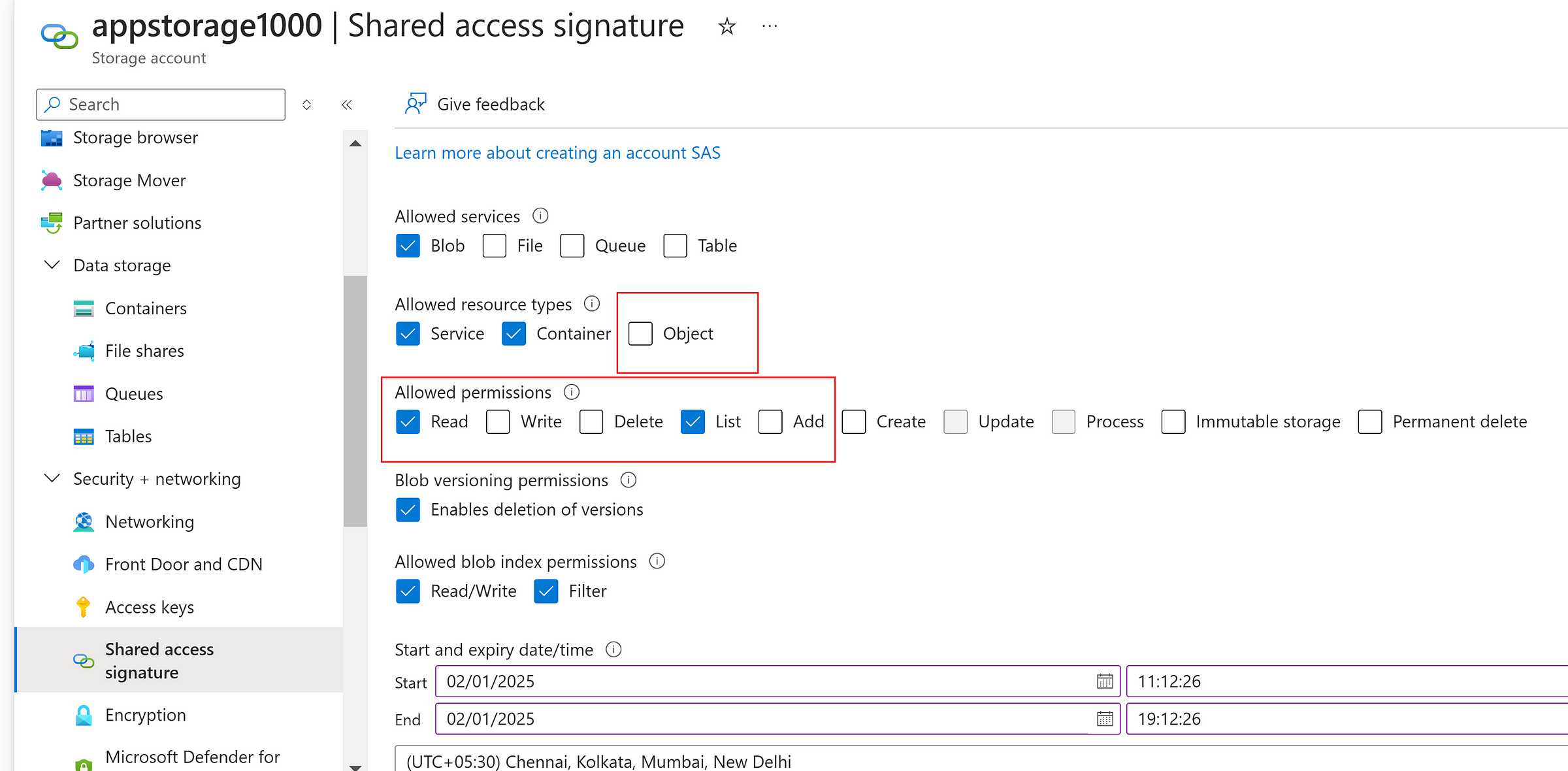
While generating SAS token at storage account level, “Allowed resource types” have the options such as Service, Container and Object.
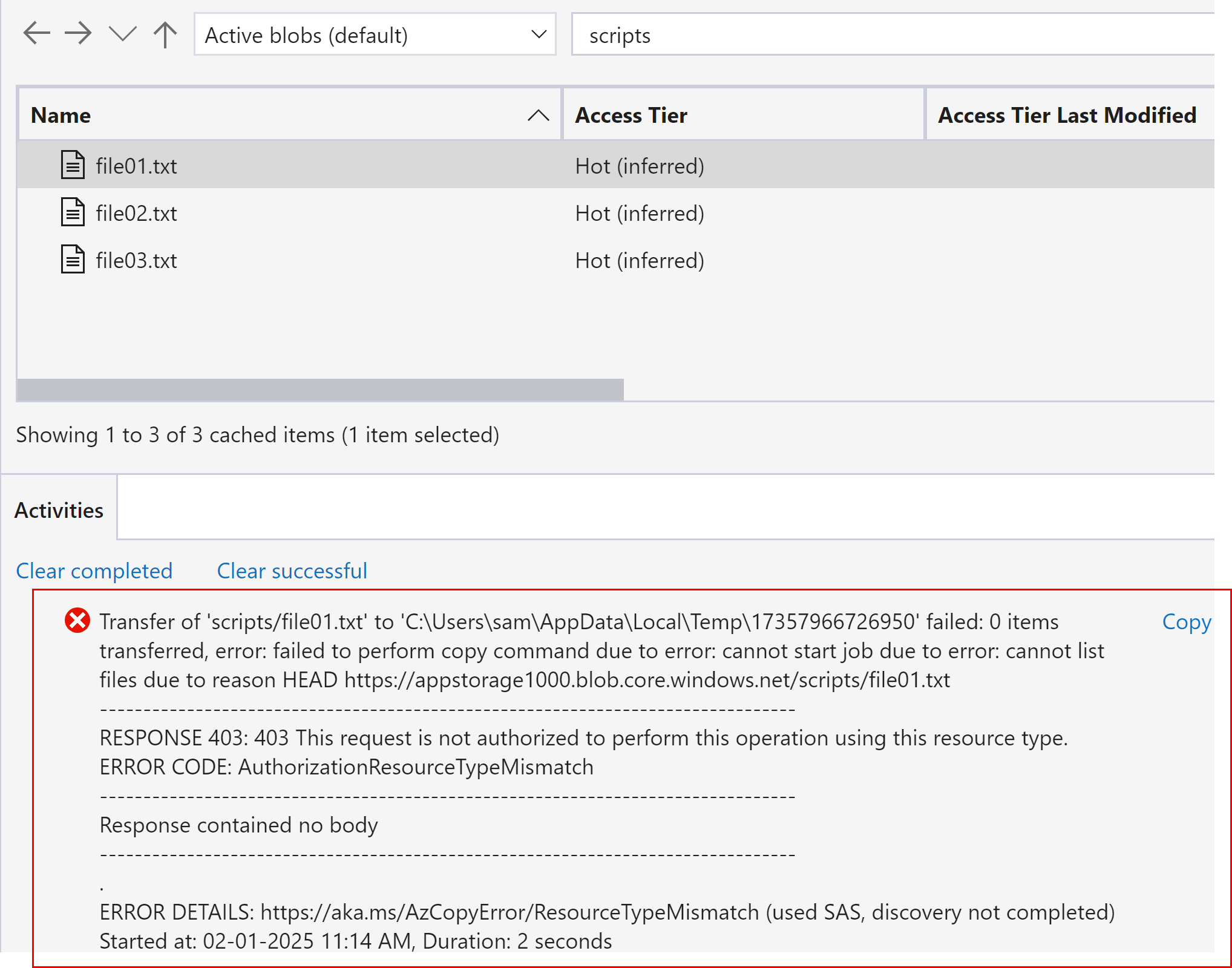
Even though, we select BLOB at Allowed Services, the Object setting at resource type must be enabled to access the individual object.
If the object is not selected, we could able to see the list of file, but cannot read, modify or delete the individual files which are objects
Access Storage Account in Azure Storage Explorer using Microsoft Entra id login
Assign a user with ‘Reader Role’ as below and login using azure credentials in the Azure Storage explorer as below.
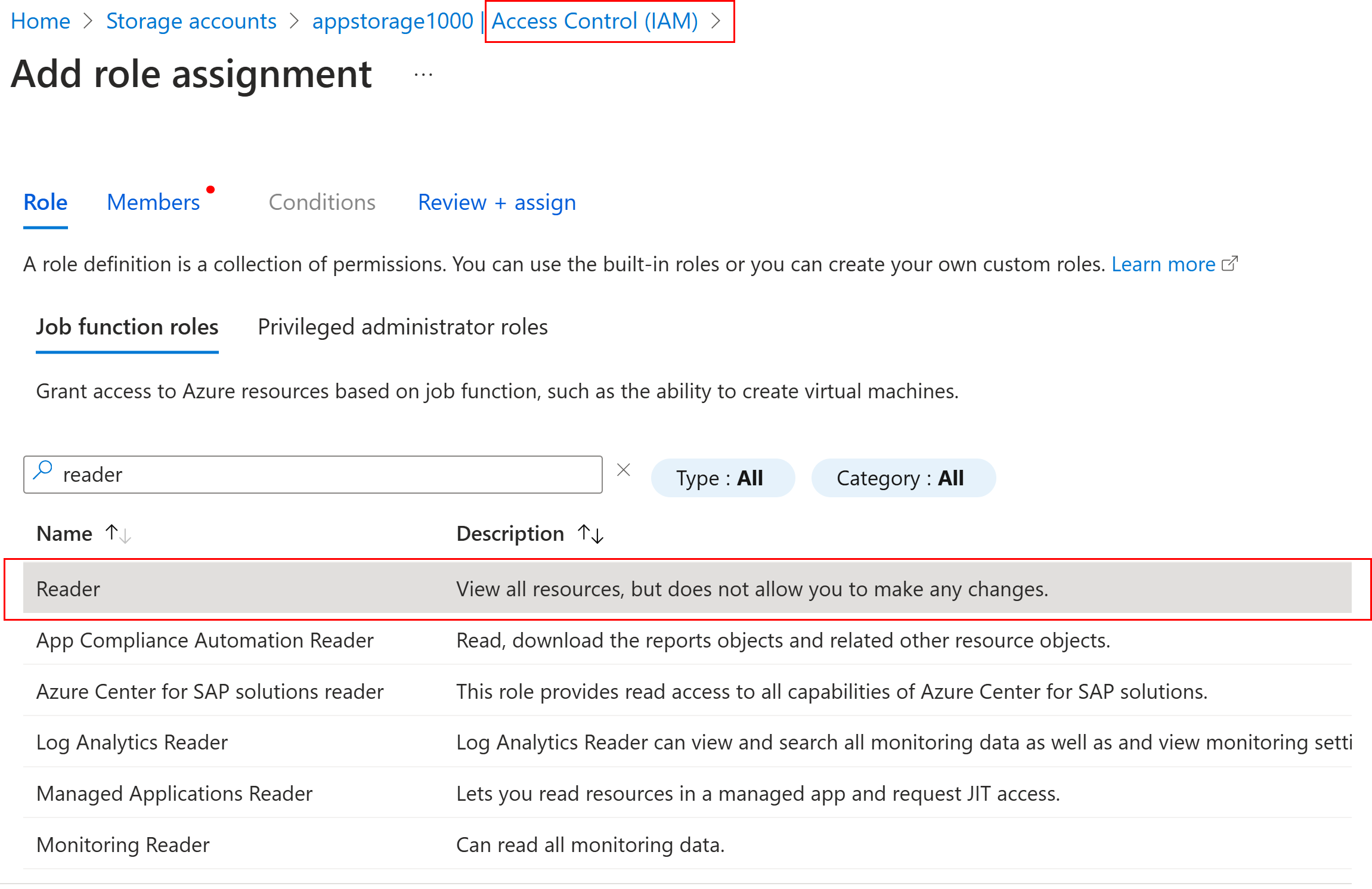
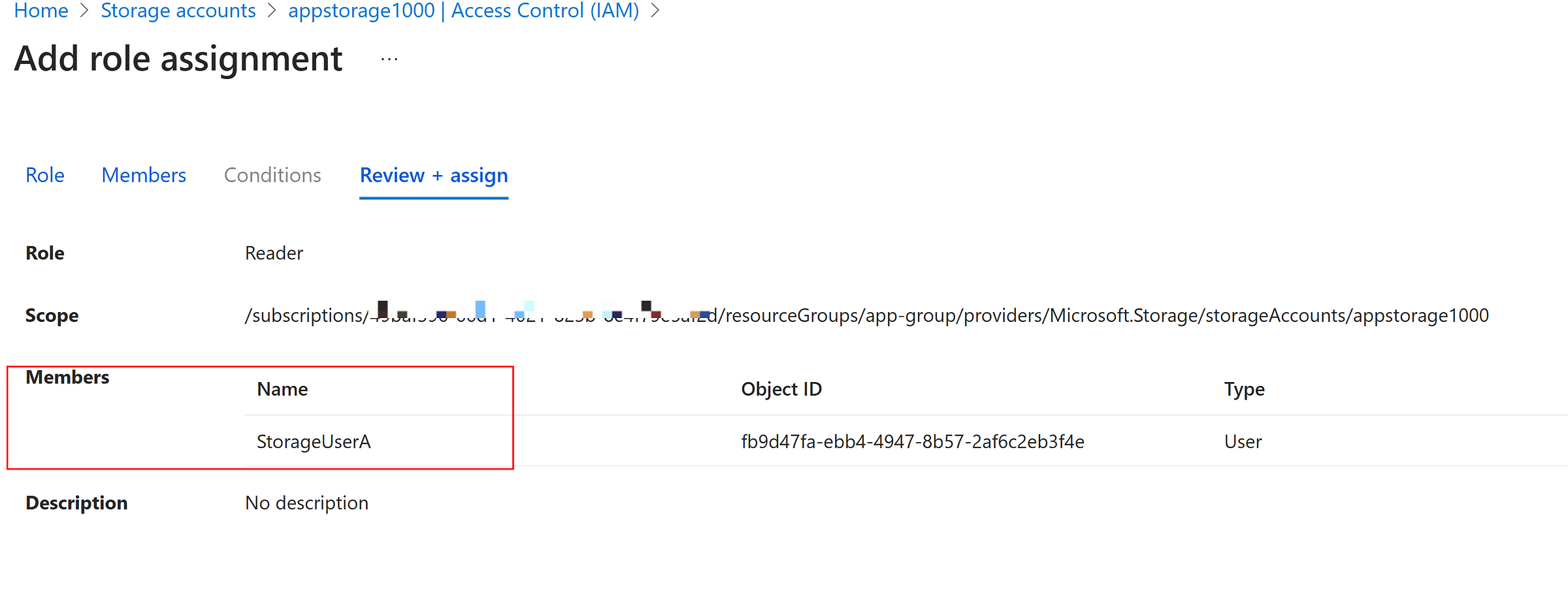
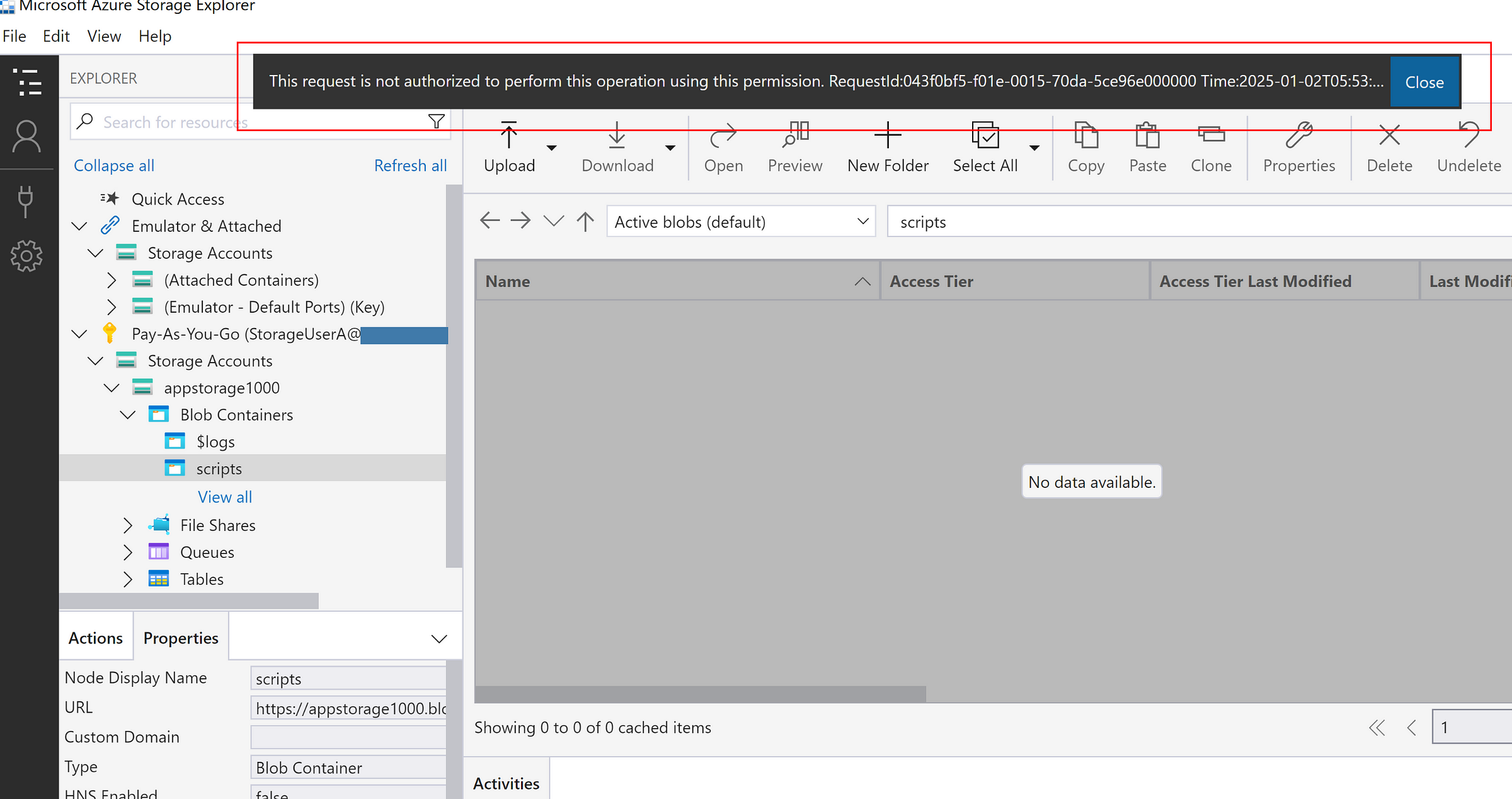
Storage account is connected, but the user cannot able to read the list of files since ‘Reader role’ doesn’t have the permissions to see the contents of the container.
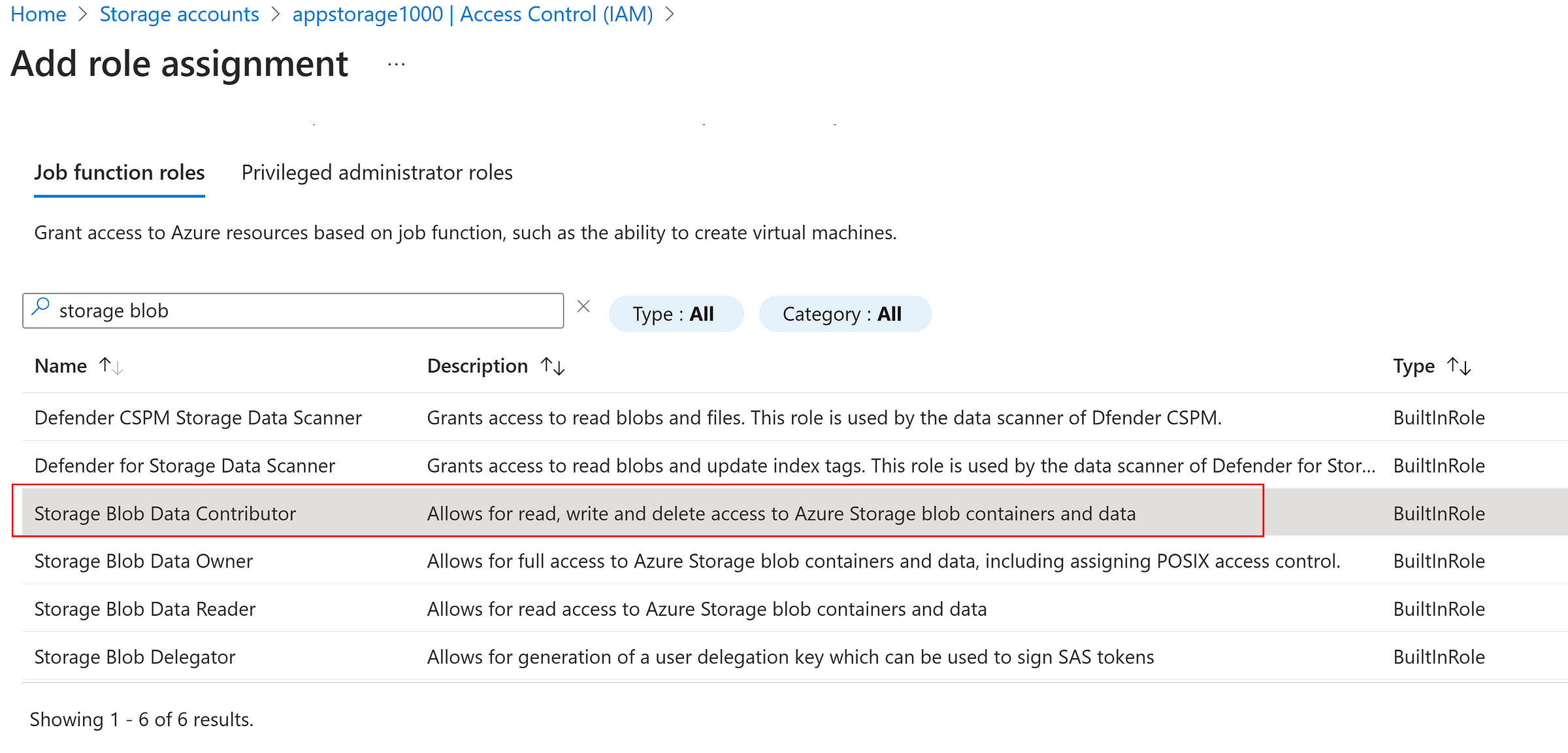
Assigning ‘Storage Blob Data Contributor’ to the user
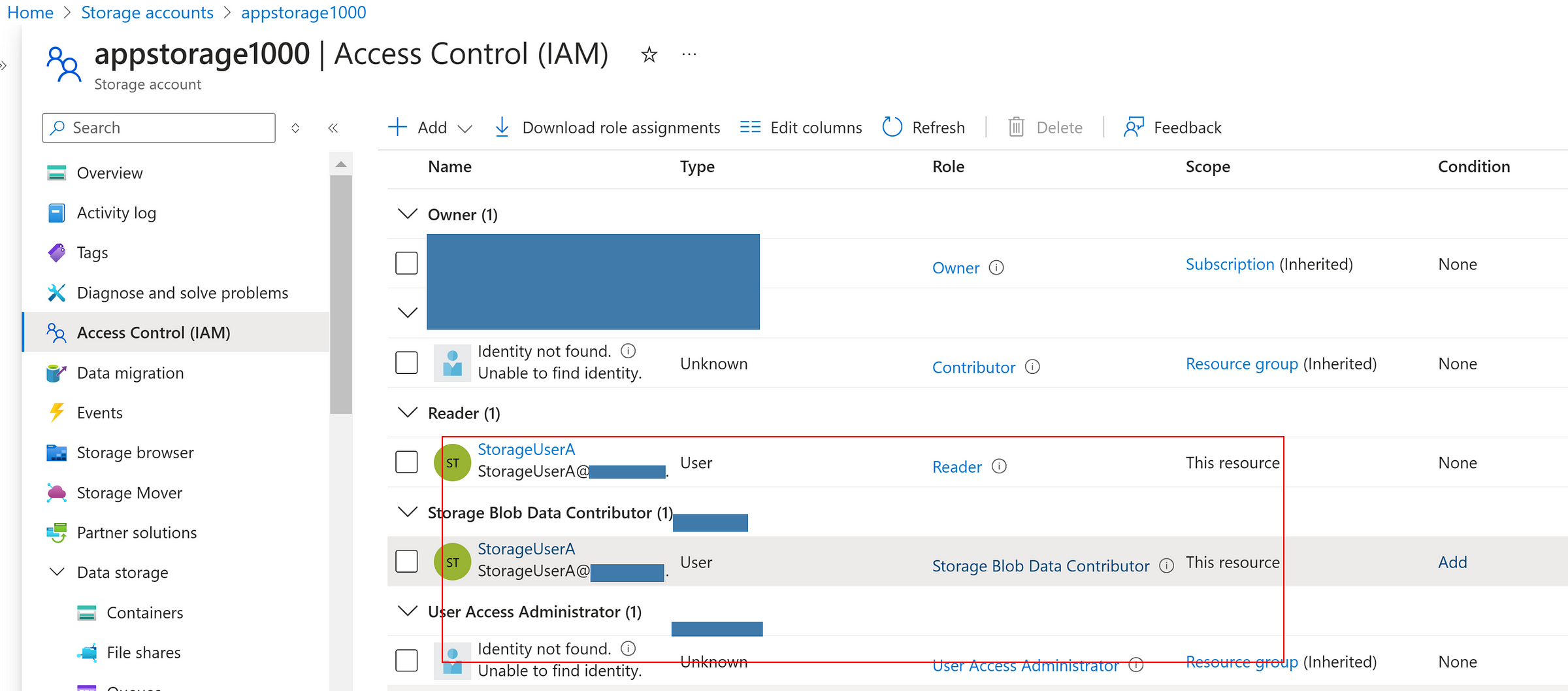
Now, the user is able to read, write and delete the files.
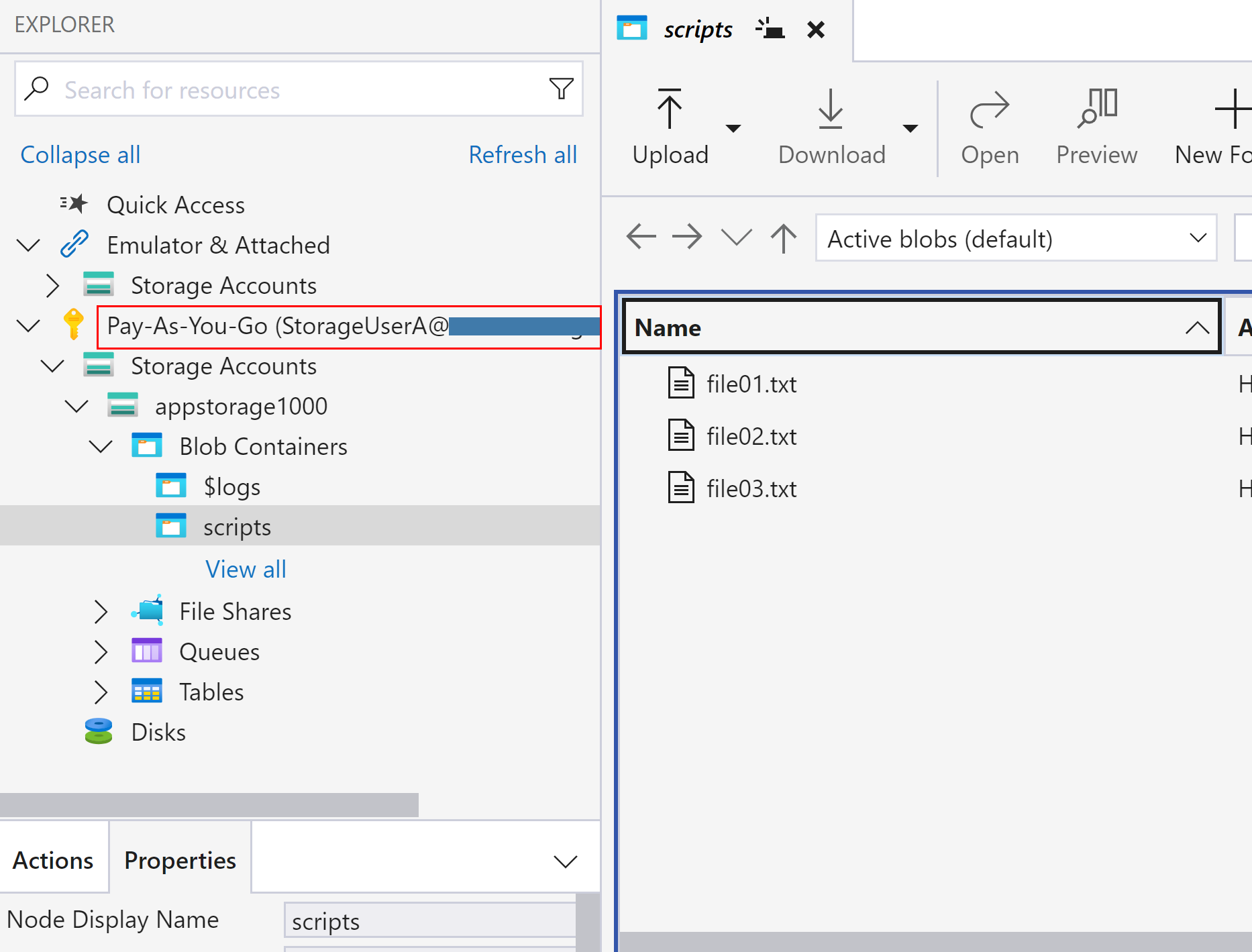
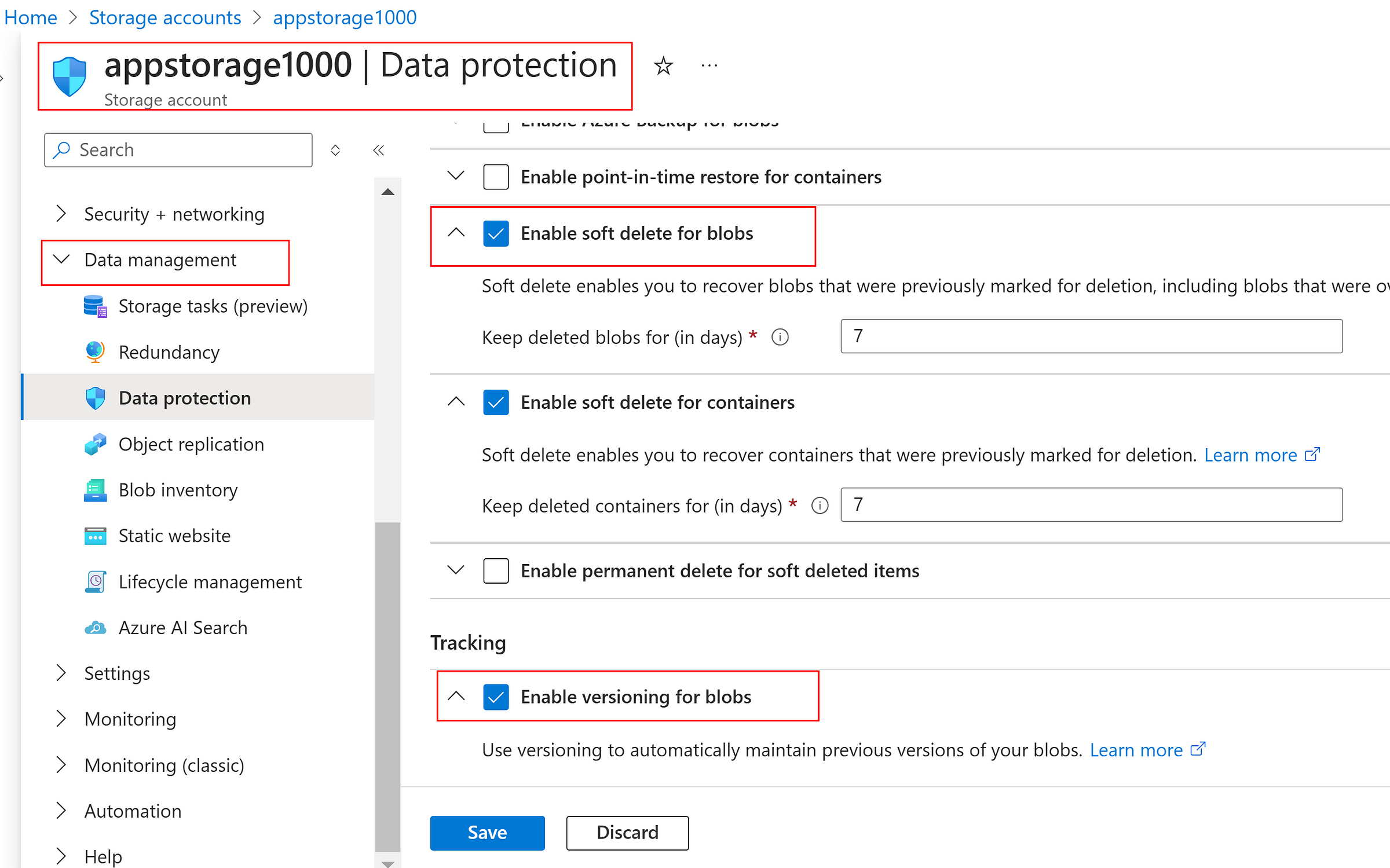
Soft Delete, Snapshots and Versioning
- Soft delete allows the recovery of files until the defined time period
- Snapshots offers instant backup facility and can be promoted to override the current version
- Versioning enables to create different versions whenever the files are modified and provides support to promote as current version
Storage Account → Data Management → Data protection
Create snapshots instantly as below
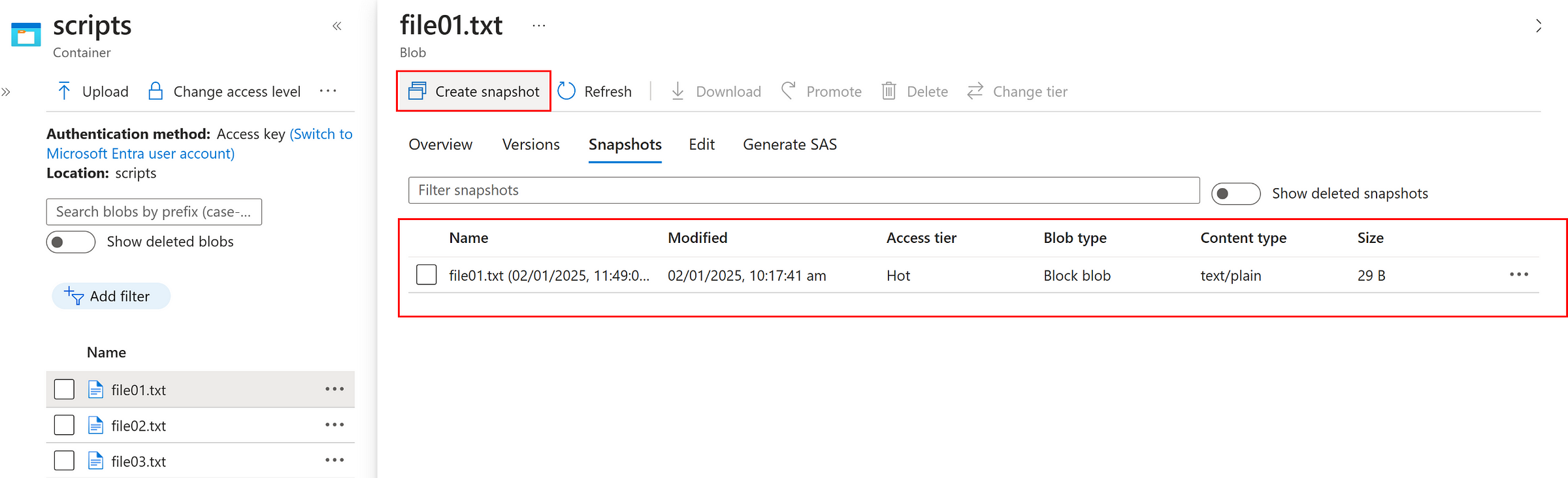
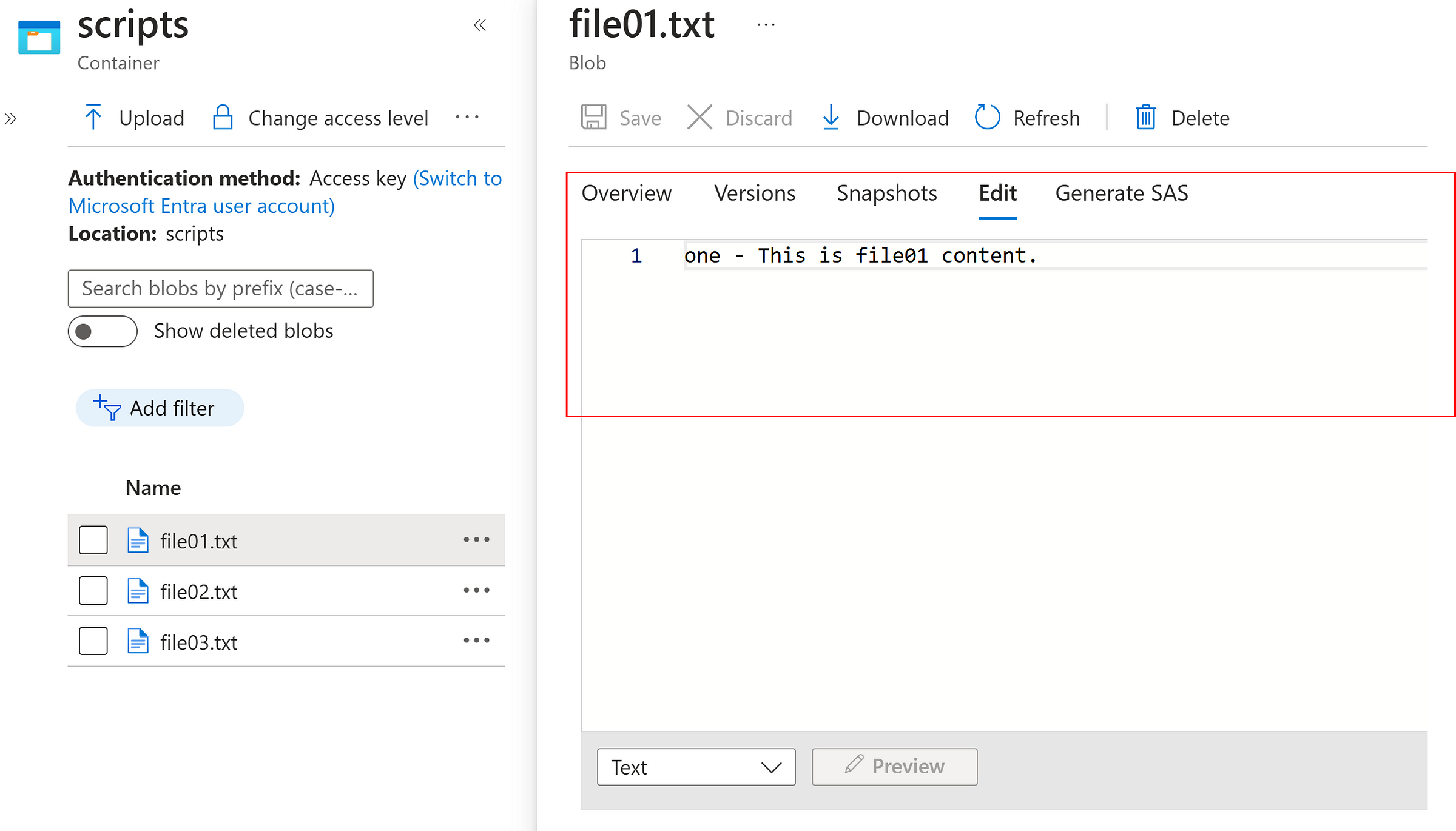
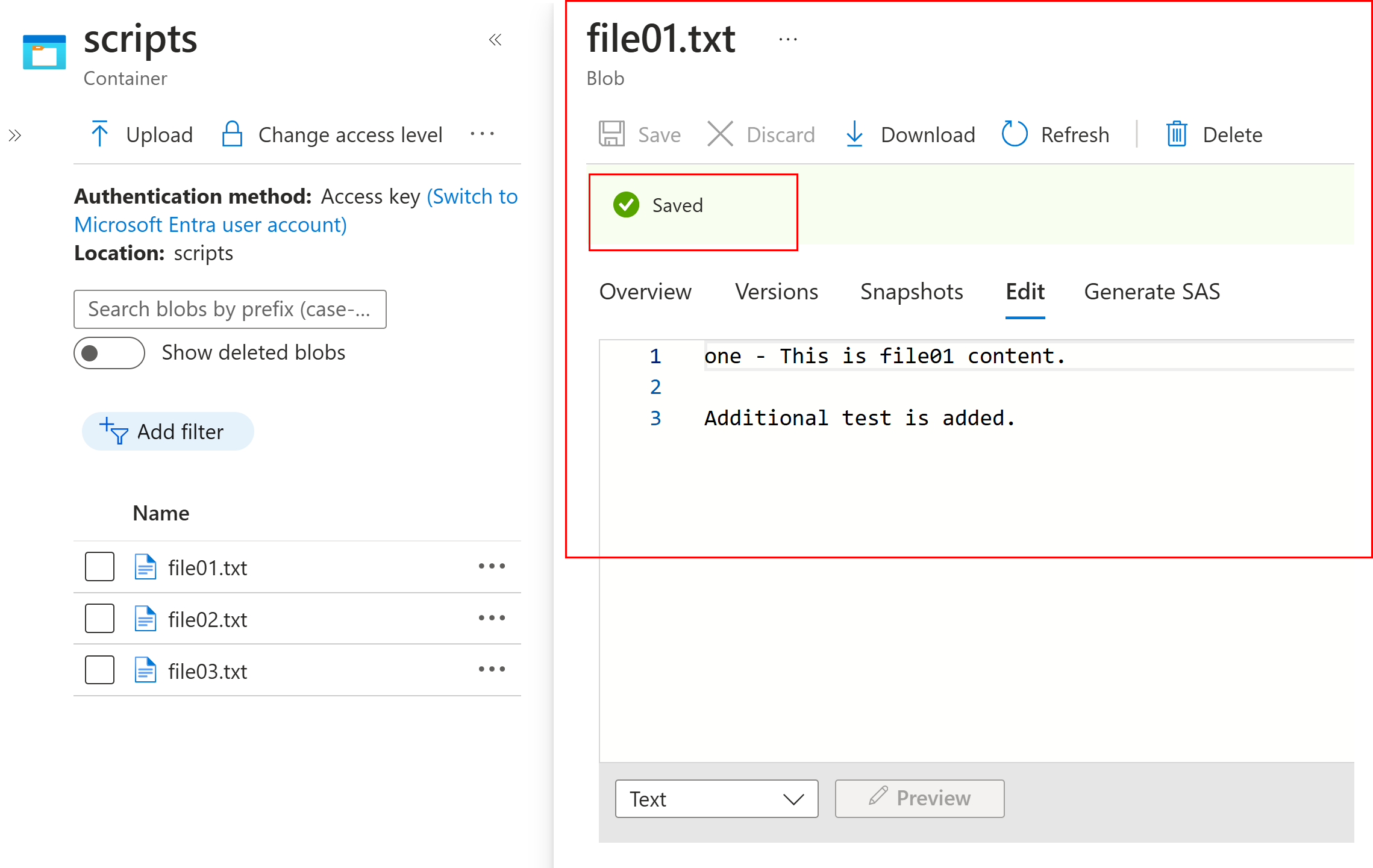
Modify the file and SAVE it.
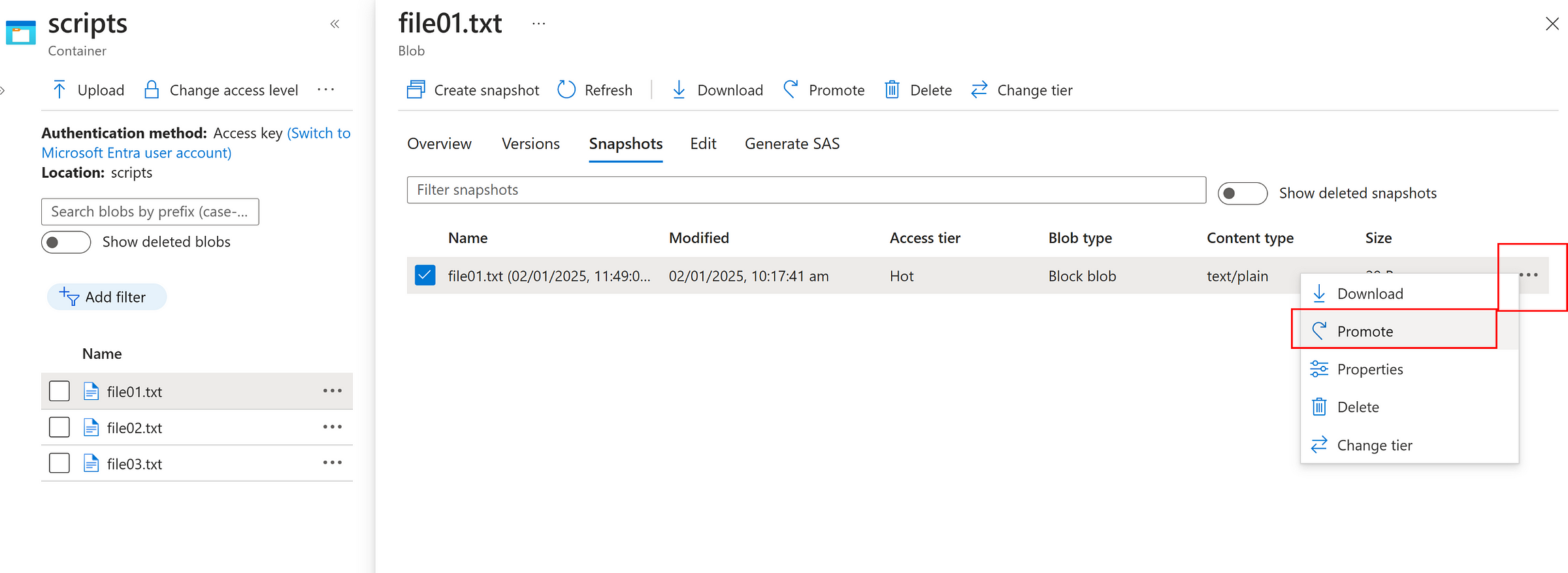
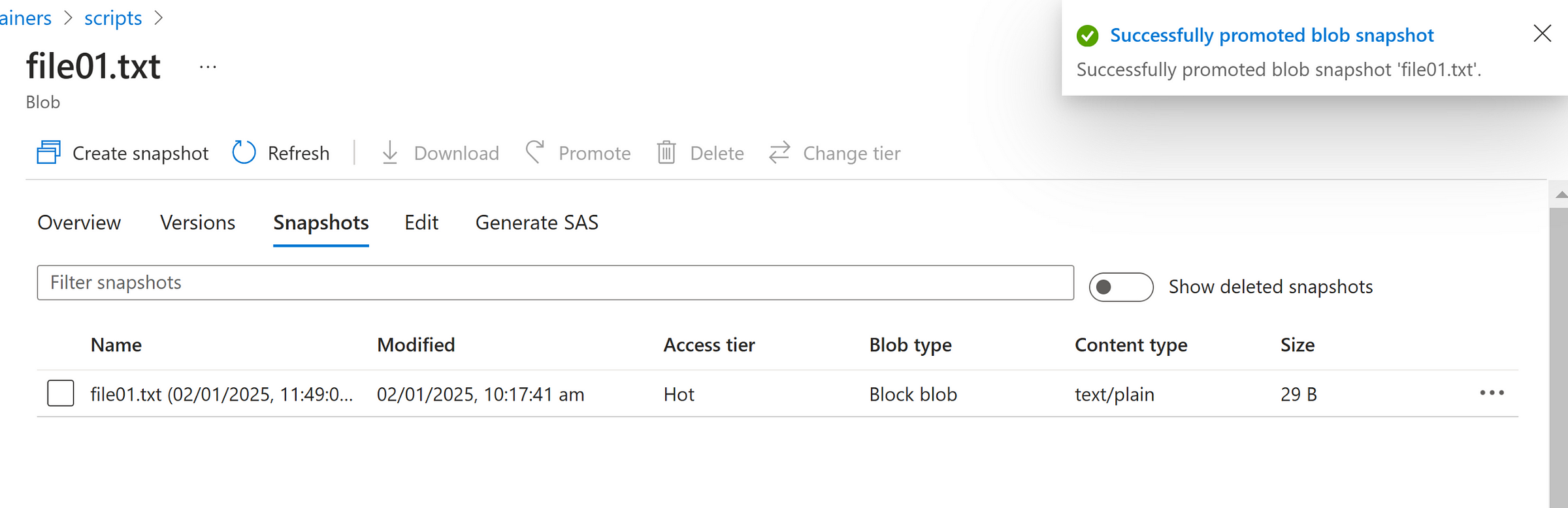
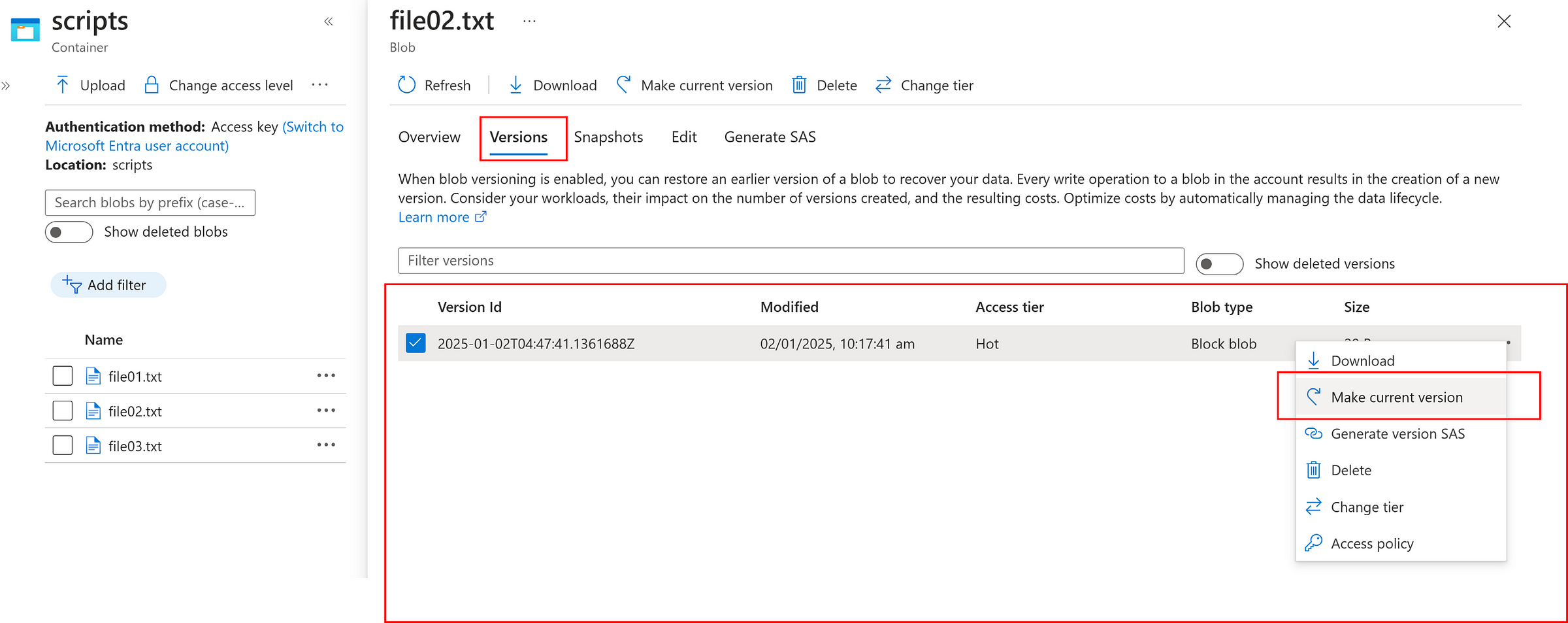
Now, we can promote the snapshot as current version if needed as below.
Versioning:
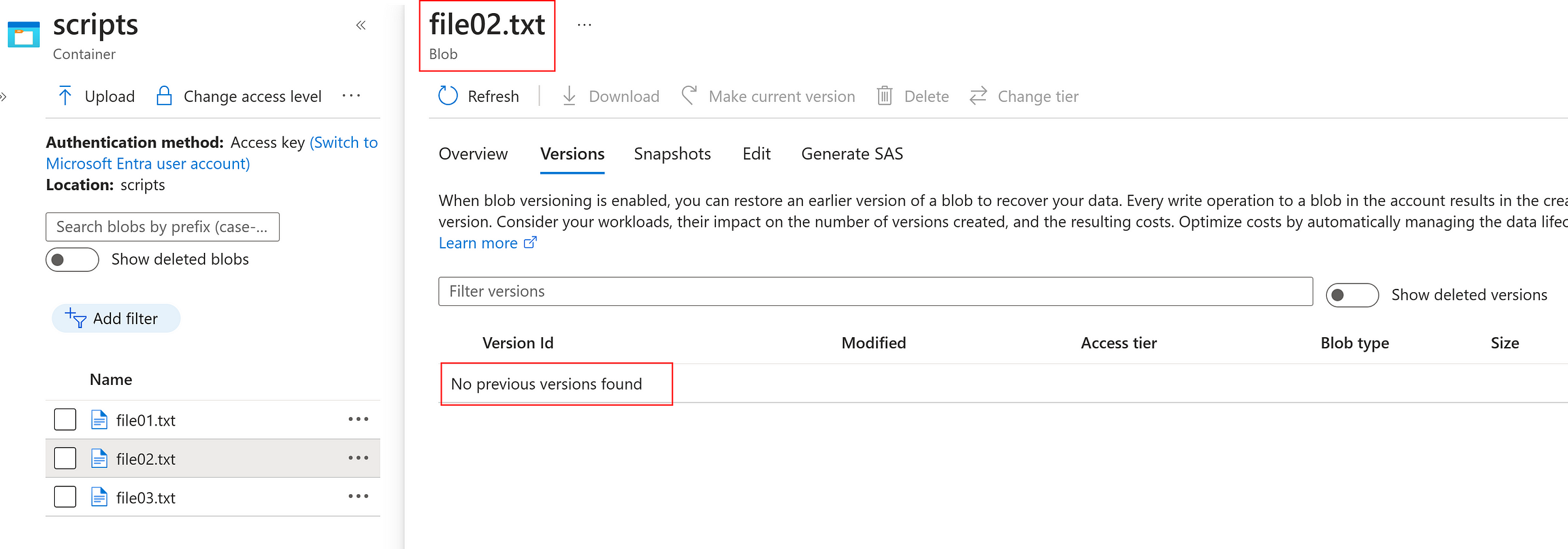
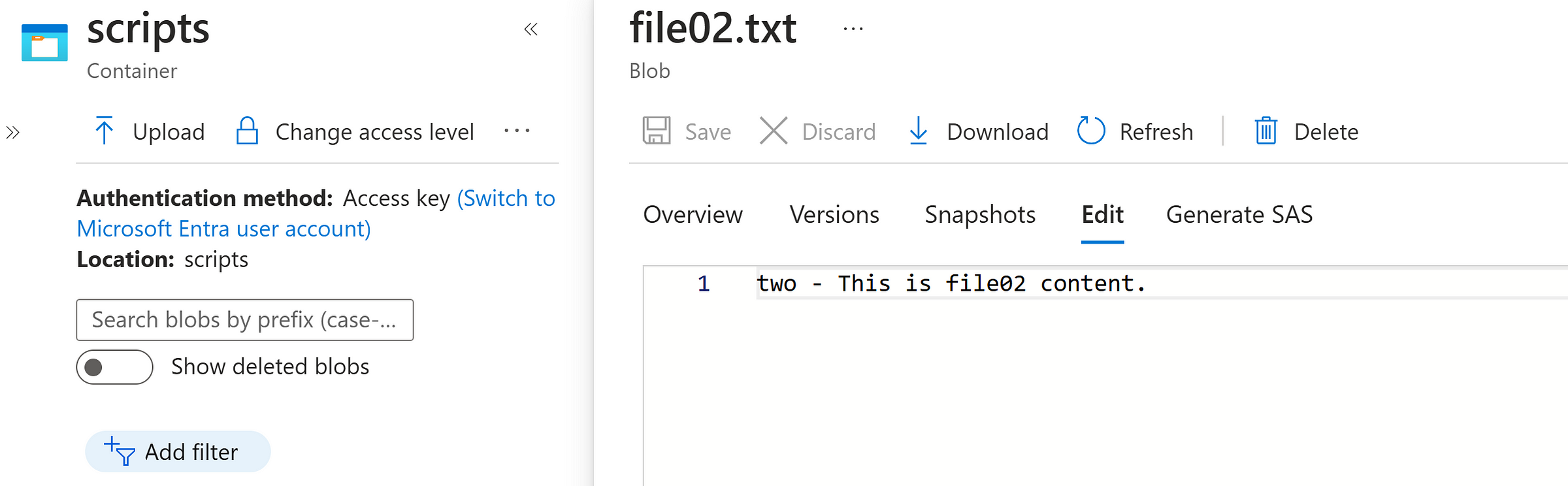
Select and Modify any file
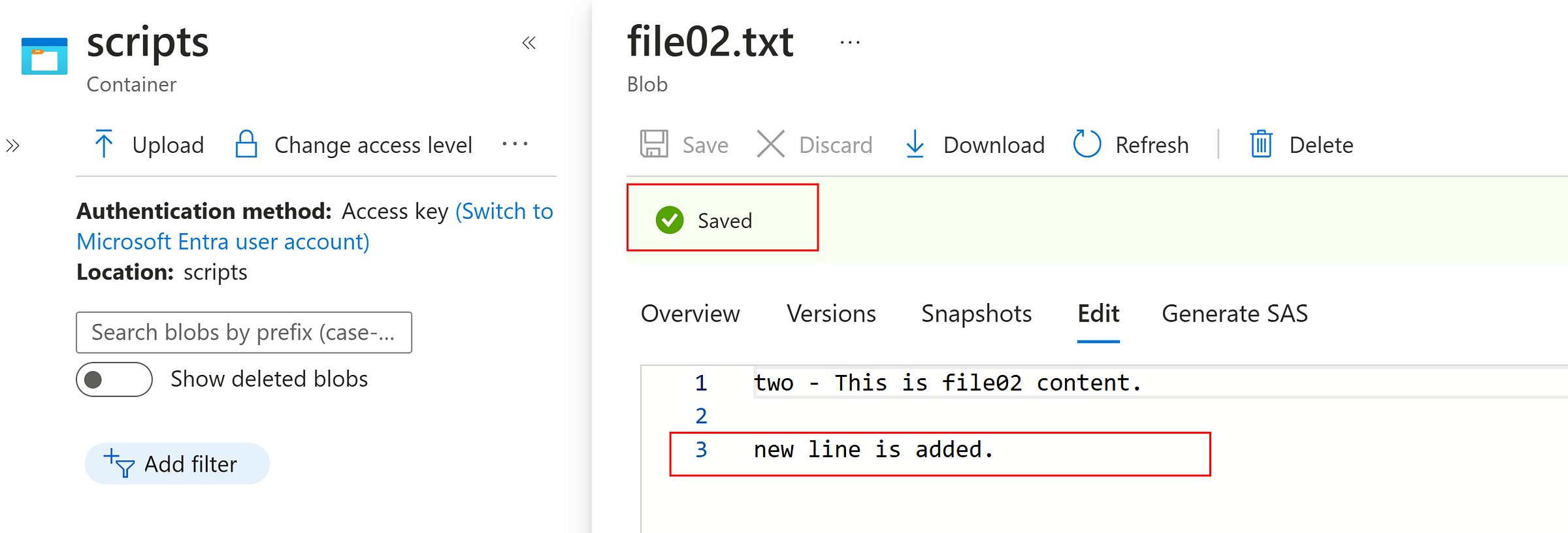
Instantly, a version is created as below which can promote as current version
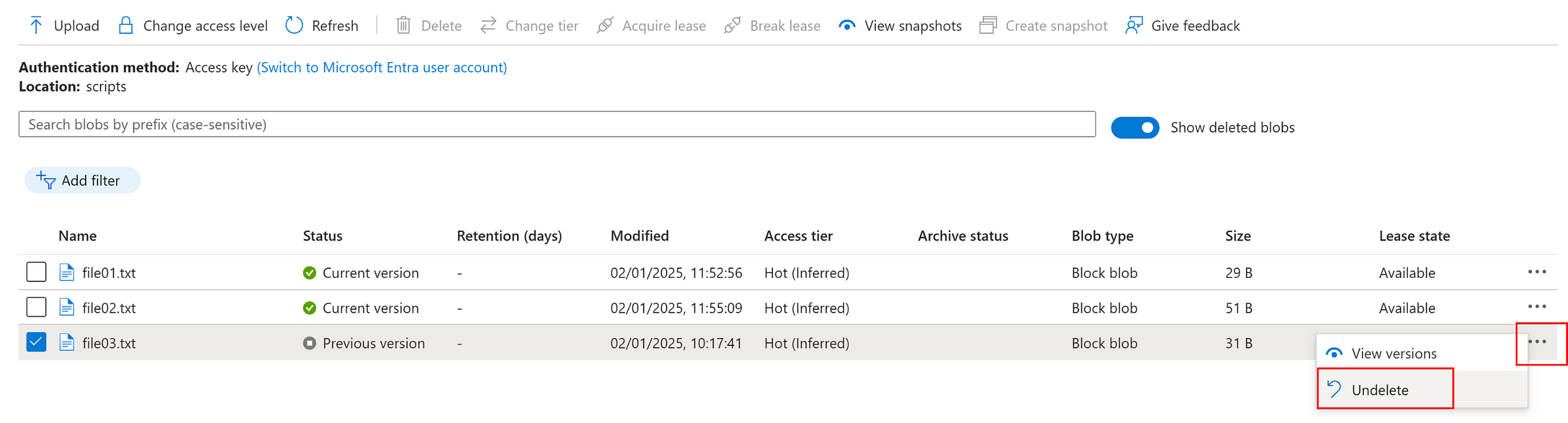
Soft delete
Delete a file
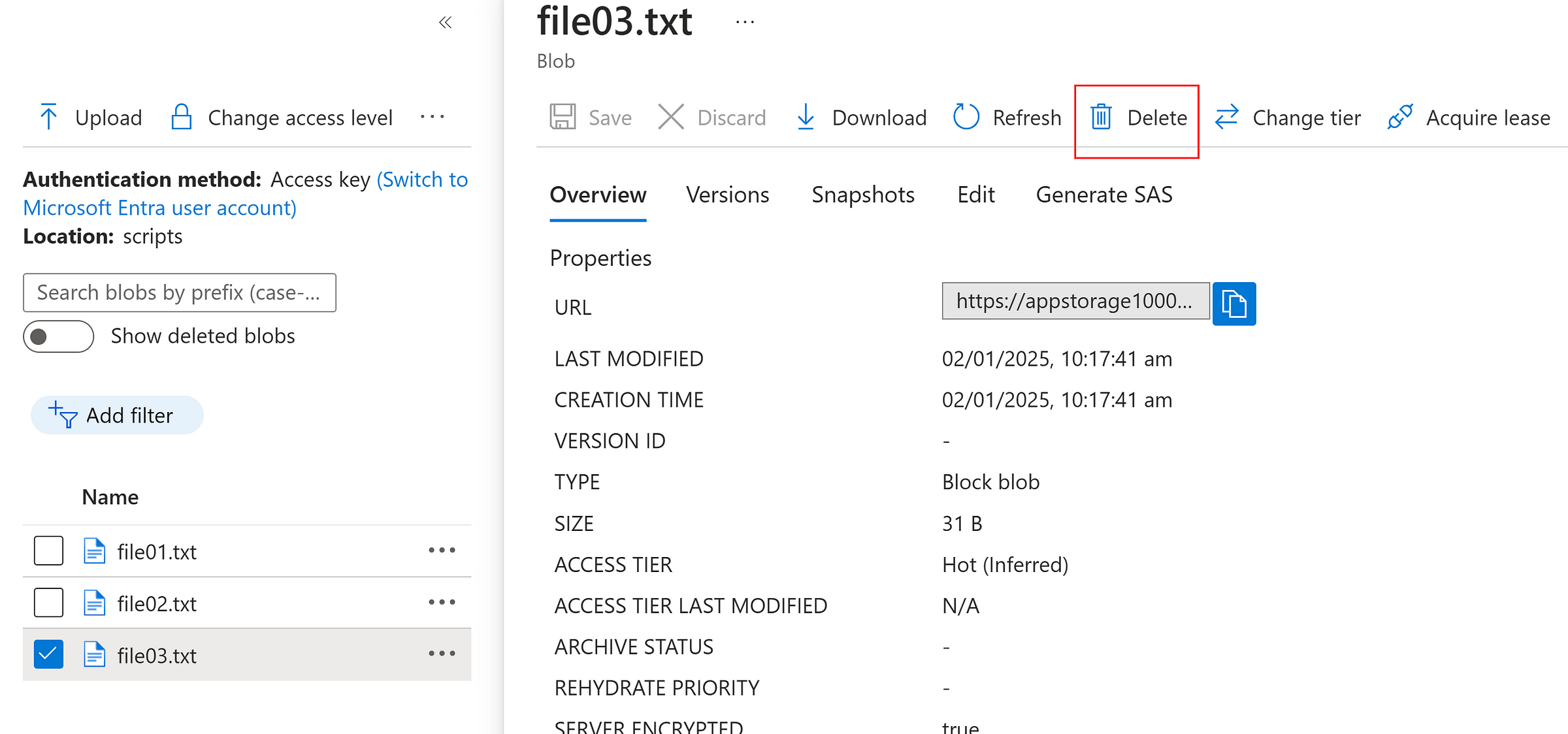
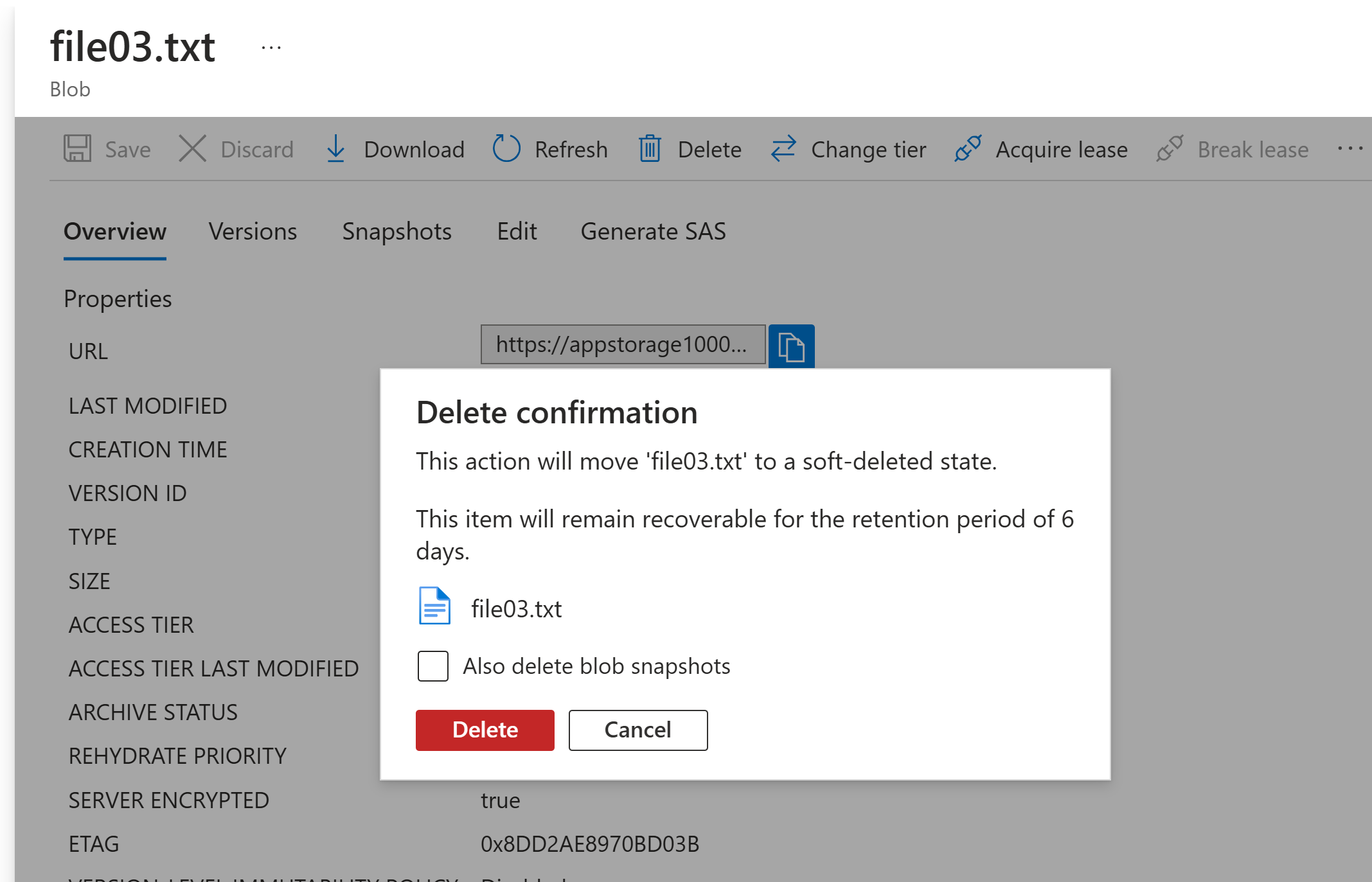
Toggle, show deleted blobs
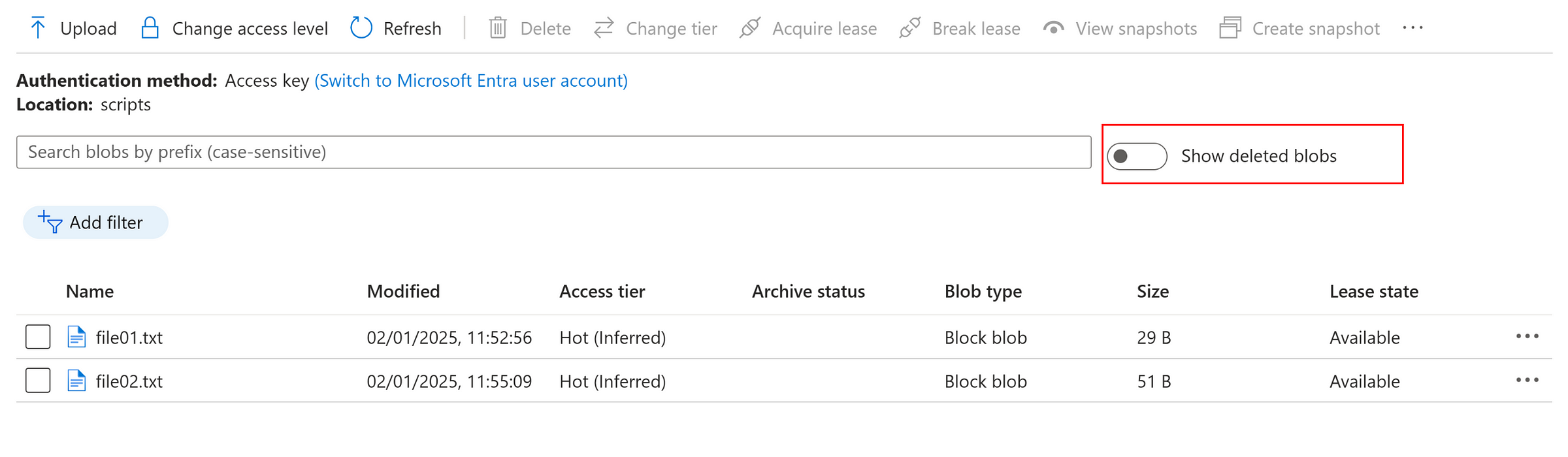
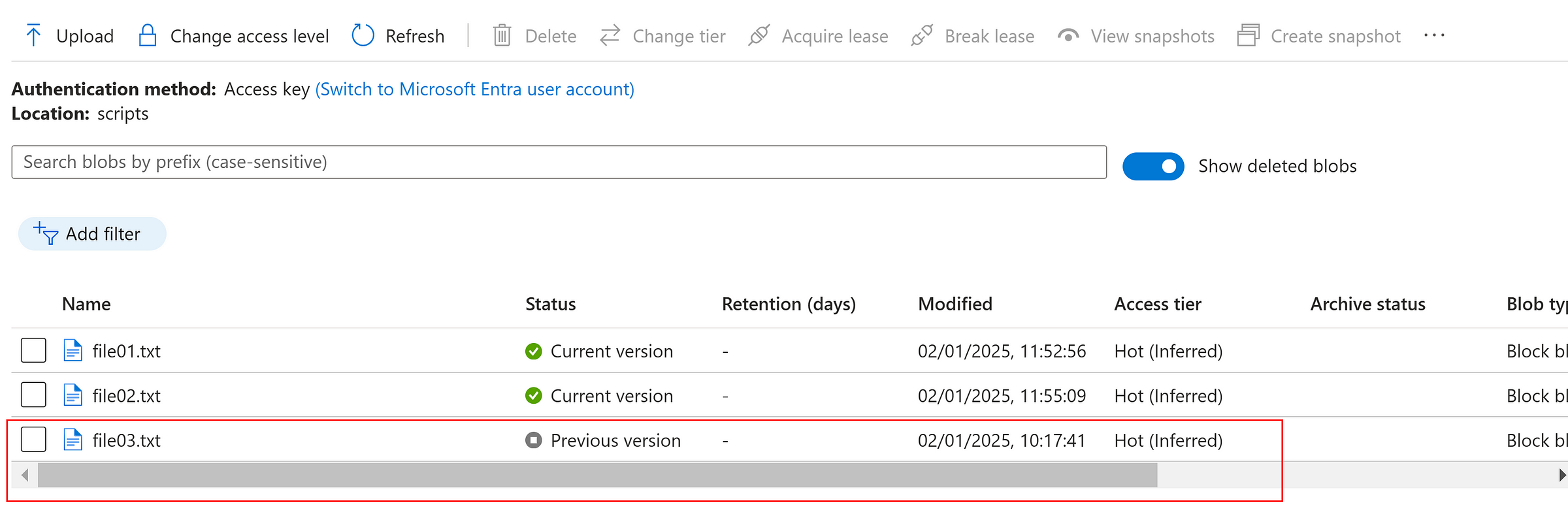
Now, we can ‘undelete’ the deleted file as below.
Microsoft Entra Roles for Azure Storage Accounts
There are many different built-in roles available, mentioned the few important roles
- Storage Blob Data Owner
- Storage Blob Data Reader
- Storage File Data Privileged Contributor
- Storage File Data Privileged Reader
- Storage Queue Data Contributor
- Storage Queue Data Message Sender — can ‘send’ a message, but cannot read his own message in the Storage Queue
- Storage Table Data Contributor
- Storage Table Data Reader
Other Types — File Storage, Queue, Table
When is comes to access and security, most of the blob related activities we saw already work for files, queues and tables. But the role assignments are different for each type as mentioned above.
There are other security measures such as customer-managed keys, encryption options and other methods which are not covered in this blog as then can be presented separately.
Please let me know if you have any comments. Thanks for reading this blog.
#AzureStorageAccount #AzureStorage #AzureStorageSecurity #AzureSecurity #AZ500 #StorageSecurity
Leave a Reply